新版的 Spring Authorization Server 自定义 UserDetails 应该怎么配置
这个实现了 UserDetailsService
@Servicepublic class UserDetailsServiceImpl implements UserDetailsService {
@Override
public UserDetails loadUserByUsername(String username) throws UsernameNotFoundException {
...
return userDetails;
}
}
之后在 SecurityConfig 配置里面应该还要做点什么吧,用内存模式就可以,自定义应该怎么配置
@EnableWebSecuritypublic class DefaultSecurityConfig {
@Bean
SecurityFilterChain defaultSecurityFilterChain(HttpSecurity http) throws Exception {
http
.authorizeRequests(authorizeRequests ->
authorizeRequests
.anyRequest().authenticated()
)
.formLogin(withDefaults());
return http.build();
}
@Bean
UserDetailsService users() {
UserDetails user = User.withDefaultPasswordEncoder()
.username("user")
.password("123456")
.roles("USER")
.build();
return new InMemoryUserDetailsManager(user);
}
}
还有,这个里面还需要配置吗?
@Configuration(proxyBeanMethods = false)public class AuthorizationServerConfig {
@Bean
@Order(Ordered.HIGHEST_PRECEDENCE)
public SecurityFilterChain authorizationServerSecurityFilterChain(HttpSecurity http) throws Exception {
OAuth2AuthorizationServerConfiguration.applyDefaultSecurity(http);
http
.exceptionHandling(exceptions ->
exceptions.authenticationEntryPoint(new LoginUrlAuthenticationEntryPoint("/login"))
);
return http.build();
}
@Bean
public RegisteredClientRepository registeredClientRepository(JdbcTemplate jdbcTemplate) {
RegisteredClient registeredClient = RegisteredClient.withId(UUID.randomUUID().toString())
.clientId("messaging-client")
.clientSecret("{noop}secret")
.clientAuthenticationMethod(ClientAuthenticationMethod.CLIENT_SECRET_BASIC)
.authorizationGrantType(AuthorizationGrantType.AUTHORIZATION_CODE)
.authorizationGrantType(AuthorizationGrantType.REFRESH_TOKEN)
.authorizationGrantType(AuthorizationGrantType.CLIENT_CREDENTIALS)
.redirectUri("http://127.0.0.1:8080/login/oauth2/code/messaging-client-oidc")
.redirectUri("http://127.0.0.1:8080/authorized")
.scope(OidcScopes.OPENID)
.scope("message.read")
.scope("message.write")
.clientSettings(ClientSettings.builder().requireAuthorizationConsent(true).build())
.build();
JdbcRegisteredClientRepository registeredClientRepository = new JdbcRegisteredClientRepository(jdbcTemplate);
registeredClientRepository.save(registeredClient);
return registeredClientRepository;
}
@Bean
public OAuth2AuthorizationService authorizationService(JdbcTemplate jdbcTemplate, RegisteredClientRepository registeredClientRepository) {
return new JdbcOAuth2AuthorizationService(jdbcTemplate, registeredClientRepository);
}
@Bean
public OAuth2AuthorizationConsentService authorizationConsentService(JdbcTemplate jdbcTemplate, RegisteredClientRepository registeredClientRepository) {
return new JdbcOAuth2AuthorizationConsentService(jdbcTemplate, registeredClientRepository);
}
@Bean
public JWKSource<SecurityContext> jwkSource() {
RSAKey rsaKey = Jwks.generateRsa();
JWKSet jwkSet = new JWKSet(rsaKey);
return (jwkSelector, securityContext) -> jwkSelector.select(jwkSet);
}
@Bean
public ProviderSettings providerSettings() {
return ProviderSettings.builder().issuer("http://localhost:9000").build();
}
}
我理解的是这样的,RegisteredClient 不应该是从 UserDetailsService 中获取吗?也就是先登录 UserDetailsService 之后,才知道 RegisteredClient 呀,我看网上讲的 UserDetailsService 都是内存模式,数据库模式的也都是旧版,还有 RegisteredClient 这个讲的就都是写死了,或者 JDBC,有没有哪位大佬能教下,应该怎么做
回答:
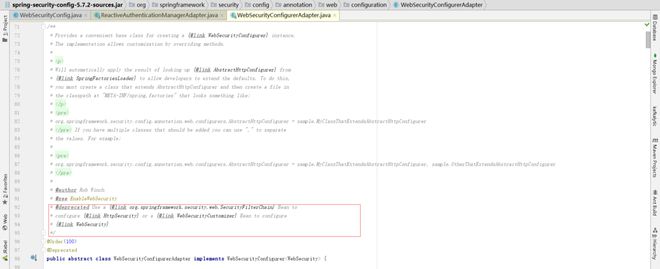 已经给出了新版的配置方式去配置HttpSecurity和WebSecurity,userdetailservice可以通过HttpSecurity自己设置,PasswordEncoder已经不需要自己单独去设置了,默认实现的处理,直接是从容器中获取passwordencoder,直接委托给它处理
已经给出了新版的配置方式去配置HttpSecurity和WebSecurity,userdetailservice可以通过HttpSecurity自己设置,PasswordEncoder已经不需要自己单独去设置了,默认实现的处理,直接是从容器中获取passwordencoder,直接委托给它处理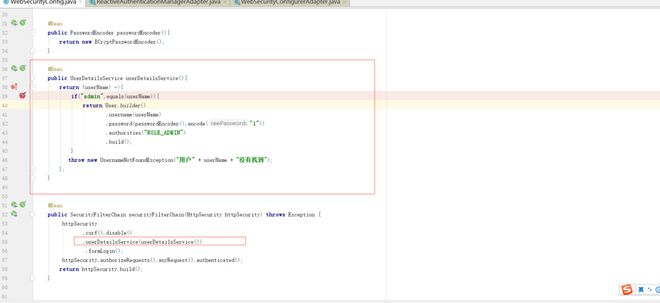
以上是 新版的 Spring Authorization Server 自定义 UserDetails 应该怎么配置 的全部内容, 来源链接: utcz.com/p/944536.html