Modification in Reverse: Unity3D Android Games
Author: dawu@Knownsec 404 Team
Chinese Version:https://paper.seebug.org/829/
0x00 Introduction
The reason why I write this simple technical article is that I really like to play digital games on google play. However, there are some drawbacks in this kind of game. In earlier stages, there is not enough resources, and you feel it very boring if you play it very slowly for a long time. As a result, I often search for its cracked version or purchased version to speed up the process until I give it up.
Actually, it’s insecure to do so, because it is impossible to tell the extra procedures of these two versions. My final solution is to reverse these APK and modify the game's logic so that I can pass the early stage quickly.
This paper is intended to introduce the idea of modification in reverse of simple Unity3D android games.
0x01 preparations
It is recommended to use the Windows system with a good JAVA environment, because it involves the modification of dll files.
1.1 Tools for reversing Android APK
For the general reverse engineering Android APK, apktool, dex2jar, jd-gui are often used, while reversing Unity3D android games, only apktool needs to be used.
- Apktool: To unzip or repackage android APK.
- dex2jar: To turn the unzipped file into "jar", and make it convenient to view via “jd-gui”.
- jd-gui: To examine the logic of dex file.
1.2 Tools for reversing dll file
The main logic of the common Unity3D Android games is in asserts/bin/data/Managed/Assembly-CSarp.dll, so we still need the tool to reverse or repackage the dll file.
- ILSpy: To view the program logic of
dll - ILDASM: To decompile
dllfiles and generateilfiles (store instructions after decompilingdllfiles) andresfiles (decompiled resource files) by installing Windows SDK or downloading from the Internet. - Ilasm: Brought by .net 4.0 and located in
C:\Windows\Microsofr.NET\Framework\v4.0.30319\ilasm.exe
1.3 Generate the repackaged self-signed certificate
Sign APK after modification and this command is used to generate a signed certificate.
keytool -genkey -v -keystore my-release-key.keystore -alias alias_name -keyalg RSA -keysize 2048 0validity 10000# 记住设置的密码,最后自签名应用的时候需要输入密码
0x02 Develop a simple Unity3D game
A simple game is develoed as example by means of Unity3D, and the logic is as follows:
Every time a hero passes a level, the combat power increases by 100.
The monster's combat power is Math.pow(2: the current level).
When the hero's combat power is less than the monster's combat power, the hero can't get through. Heroes can consider practice or rebirth to improve their combat effectiveness.
Every time the hero practices, the combat power will increase by 1000.
After the hero chooses rebirth, the number of levels is cleared and you need to play anew, but the initial combat power of the hero will increase by 2000 multipling the number of previous levels.

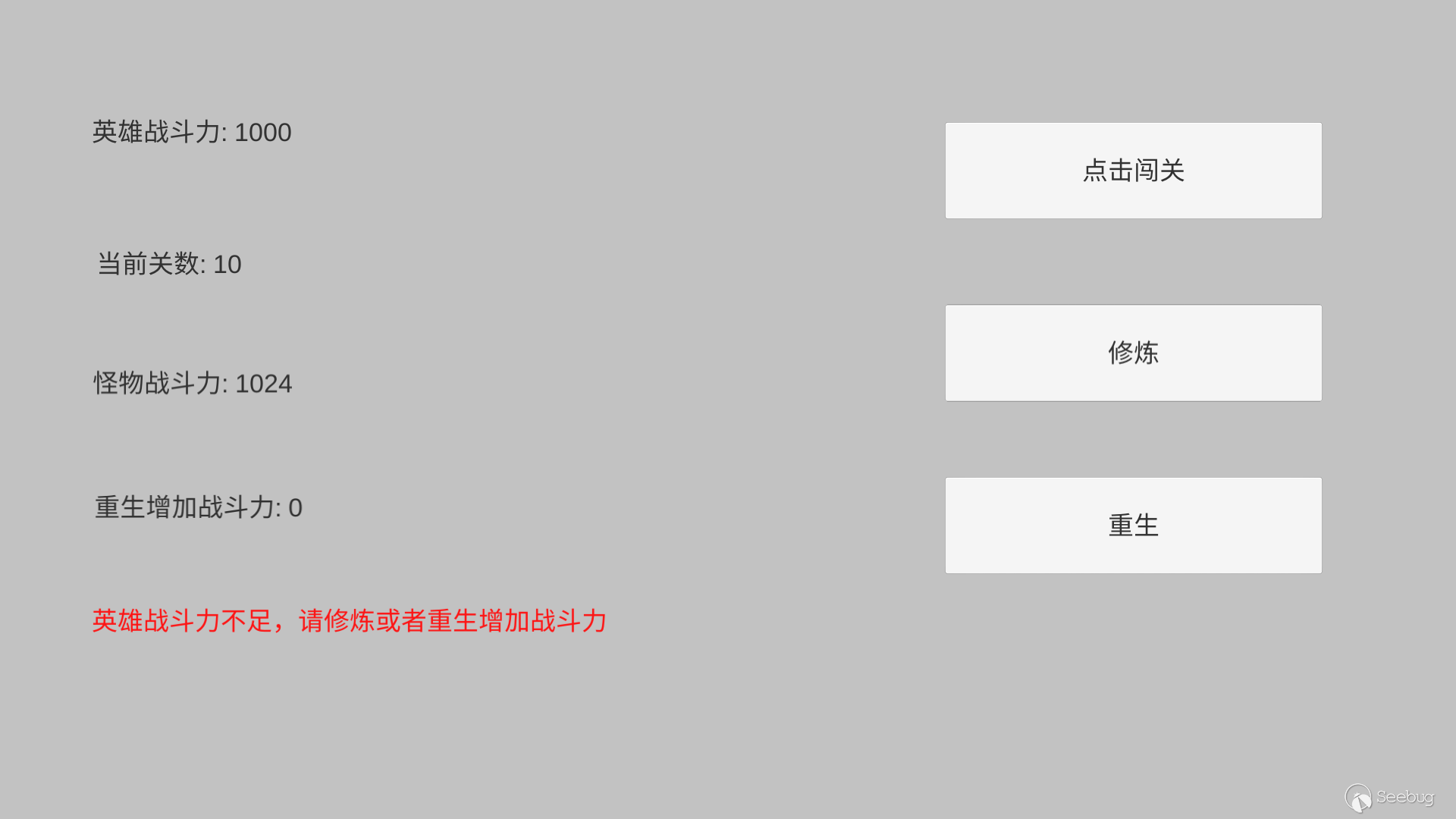
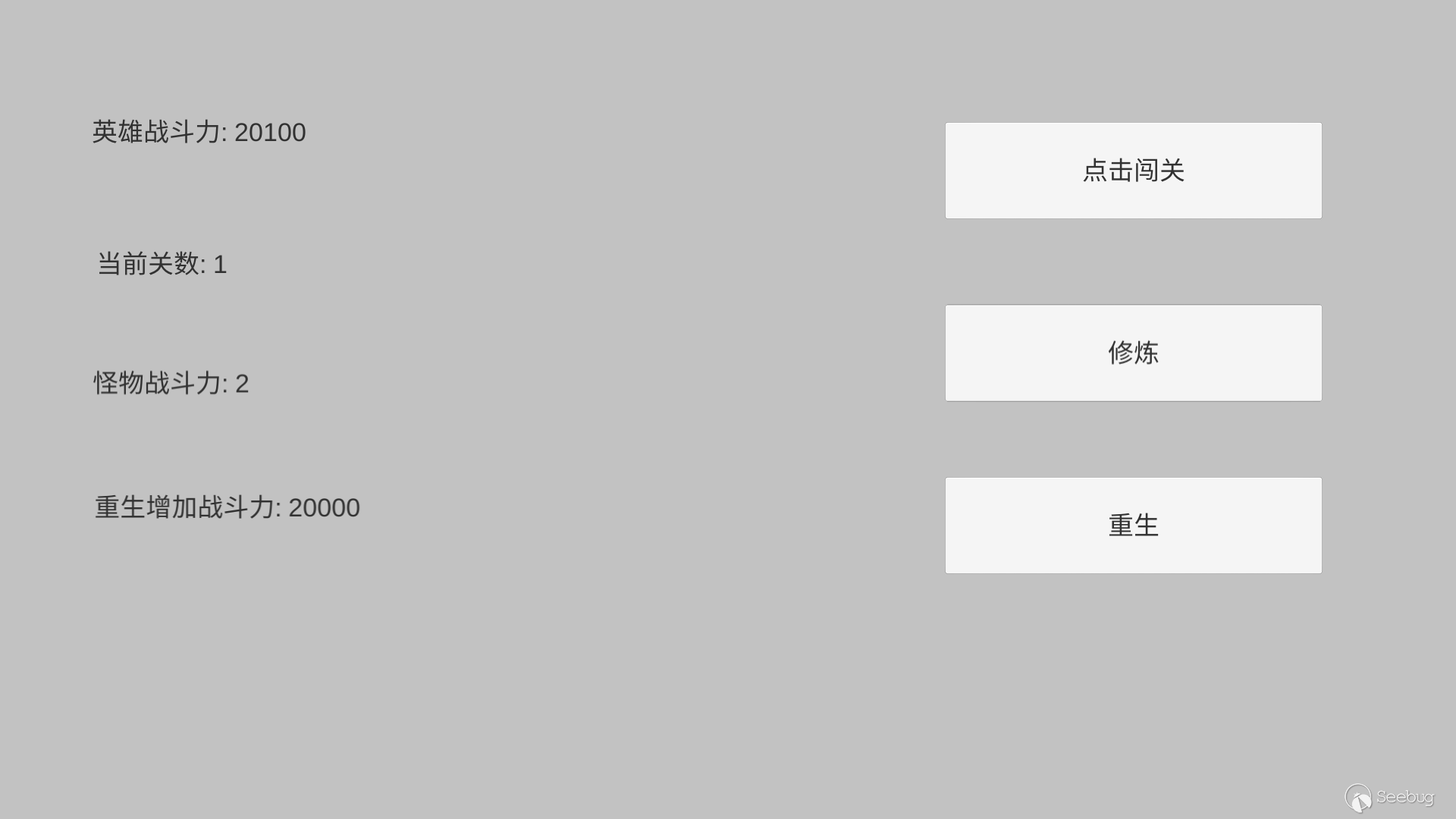
The specific code can be referred to on Github.
0x03 The reverse steps of game
(1) Unzip the game installation package with apktool
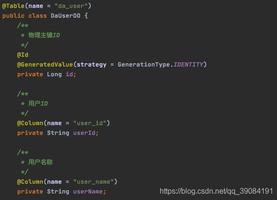
(2) Extract game/assets/bin/data/Managed/Assembly-CSarp.dll, and view the logic in dll by opening with ILSpy.
PS: The core code of Android games developed by Unity3D is in the dll file, so it’s enough to reverse or modify it, which is also different from other Android reverse.
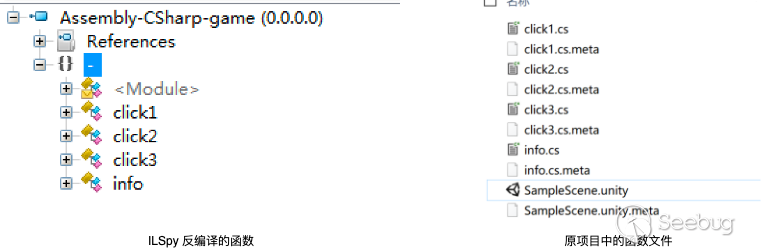
If there is no mix, the content of decompiled function is very similar to the original one:
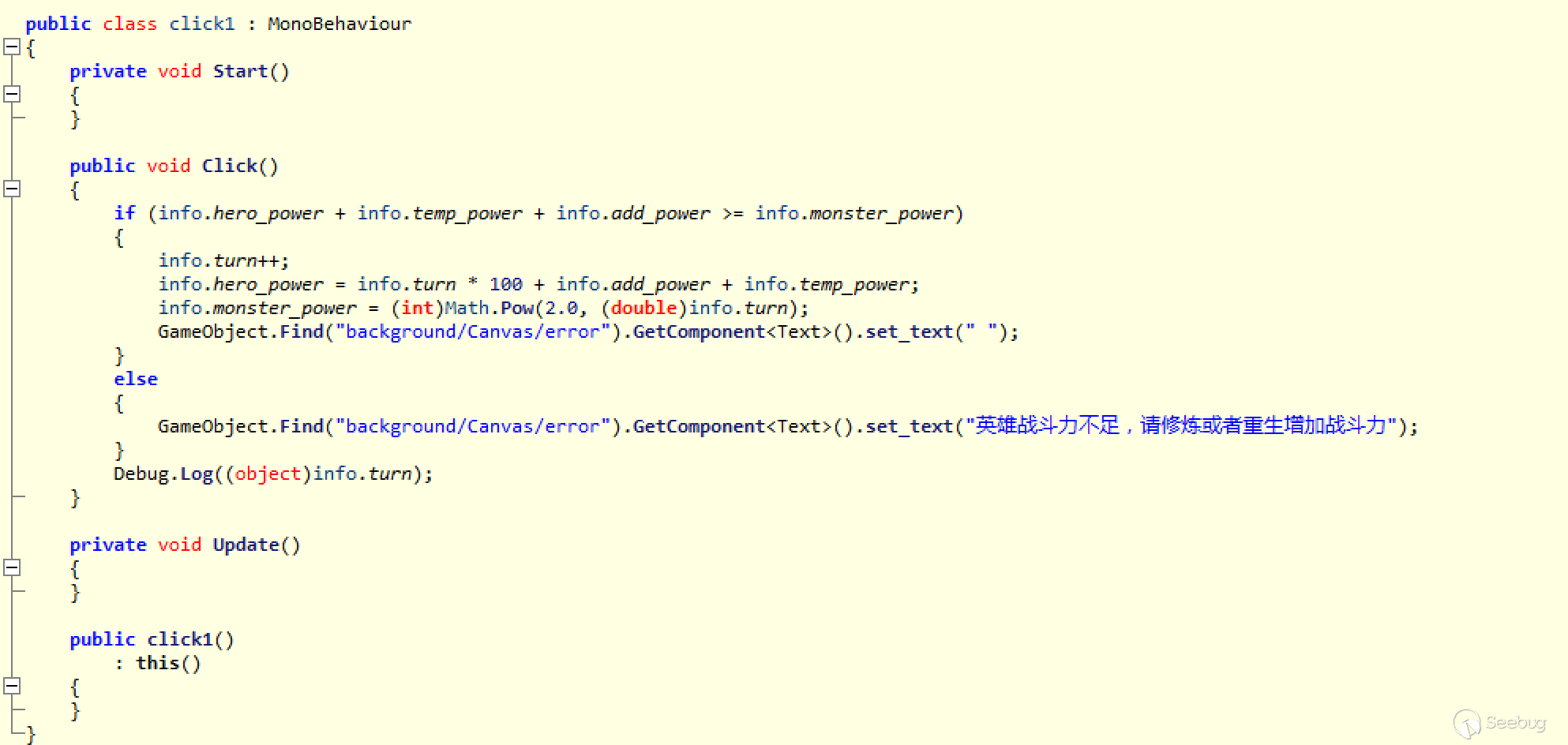
The contents of "Click1" decompiled by ILSpy
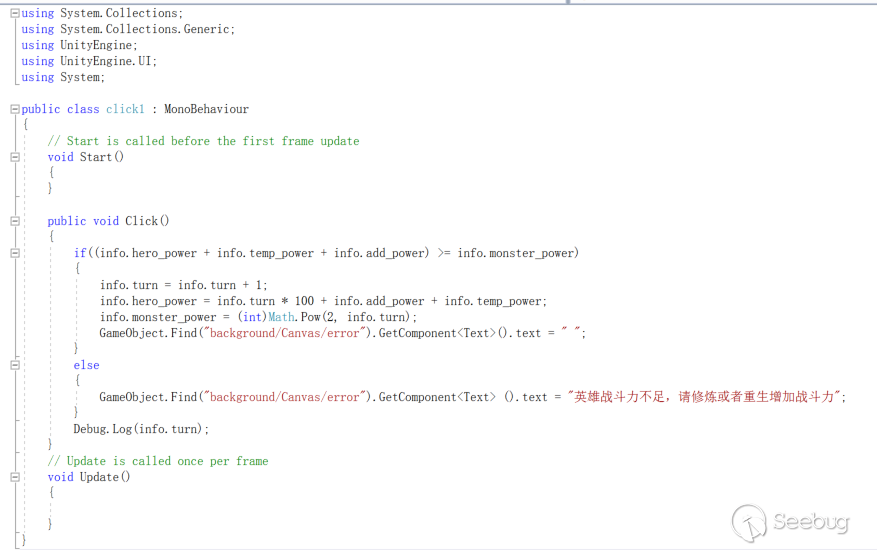
The original code of "Click1"
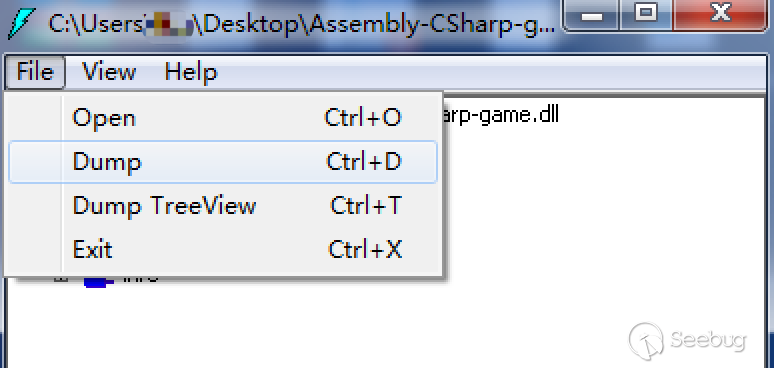
(3) Having found the key functions and key logic, you can try to decompile and modify the dll file by using ILDASM. After opening the dll file with ILDASM, the decompiled results can be exported via File -> dump.
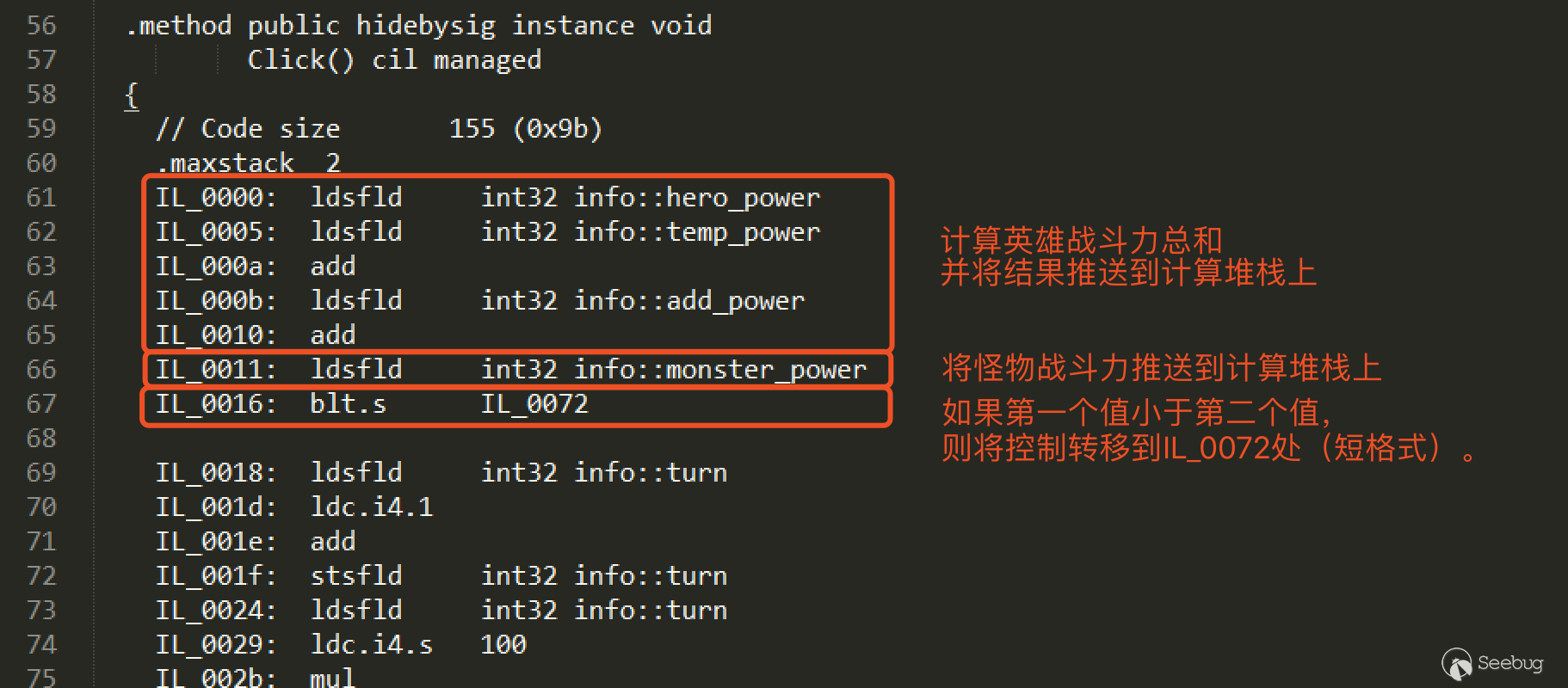
(4) It’s easy to understand the logic based on the step 2. According to the zoom table, you can know what to modify in the il files. The critical judgment is in info.hero_power + info.temp_power + info.add_power >= info.monster_power. Open the .il files in step 3 and modify the corresponding key logic on the basis of .NET IL zoom table.
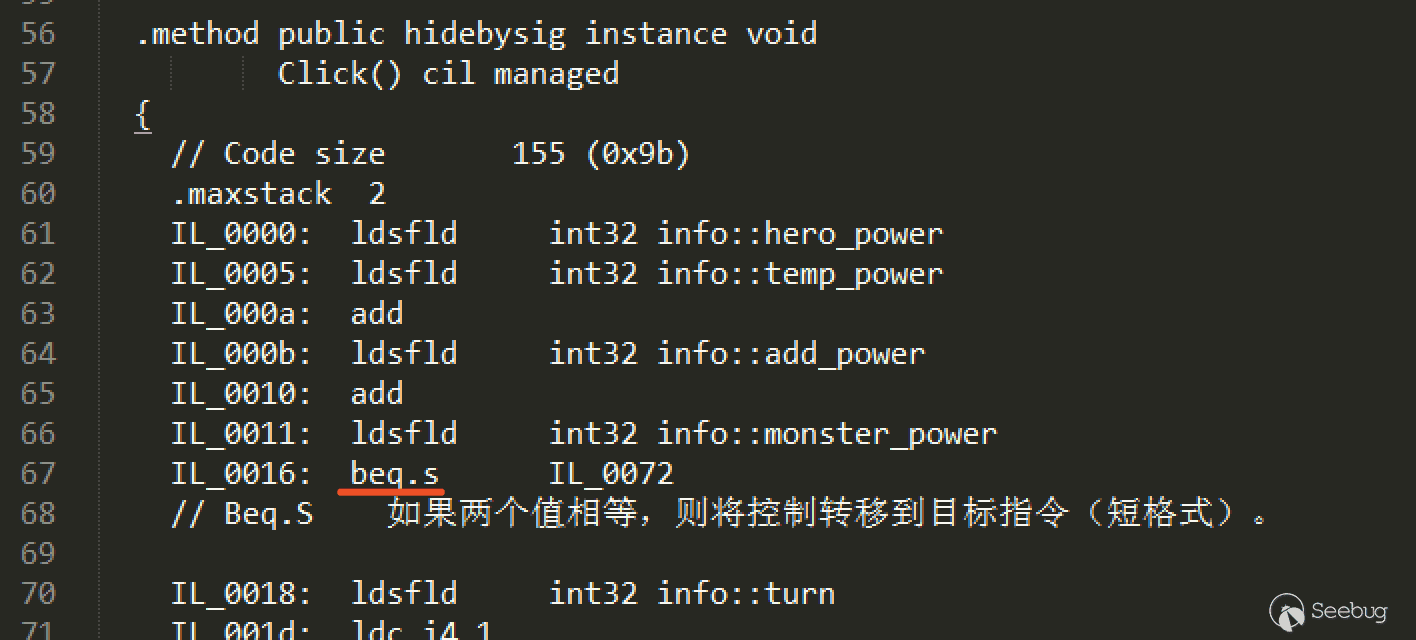
Modify it to info.hero_power + info.temp_power + info.add_power != info.monster_power, you can pass the logical judgment here.
(5) Having modified the key logic, you can install and run APK on the phone.
The command to recompile the dll file is as follows:
C:\Windows\Microsoft.NET\Framework\v4.0.30319\ilasm.exe game.il /output=Assembly-CSarp.dll /dllSend the recompiled dll back into the game/assets/bin/data/Managed/ directory and repackage the APK with apktool:
java -jar apktool.jar b gamecp game/dist/game.apk ./
Self-signed application:
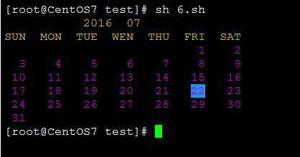
jarsigner -verbose -sigalg SHA1withRSA -digestalg SHA1 -keystore my-release-key.keystore game.apk alias_nameHaving modified successfully, once you start the training, you will be able to pass through the checkpoints infinitely.
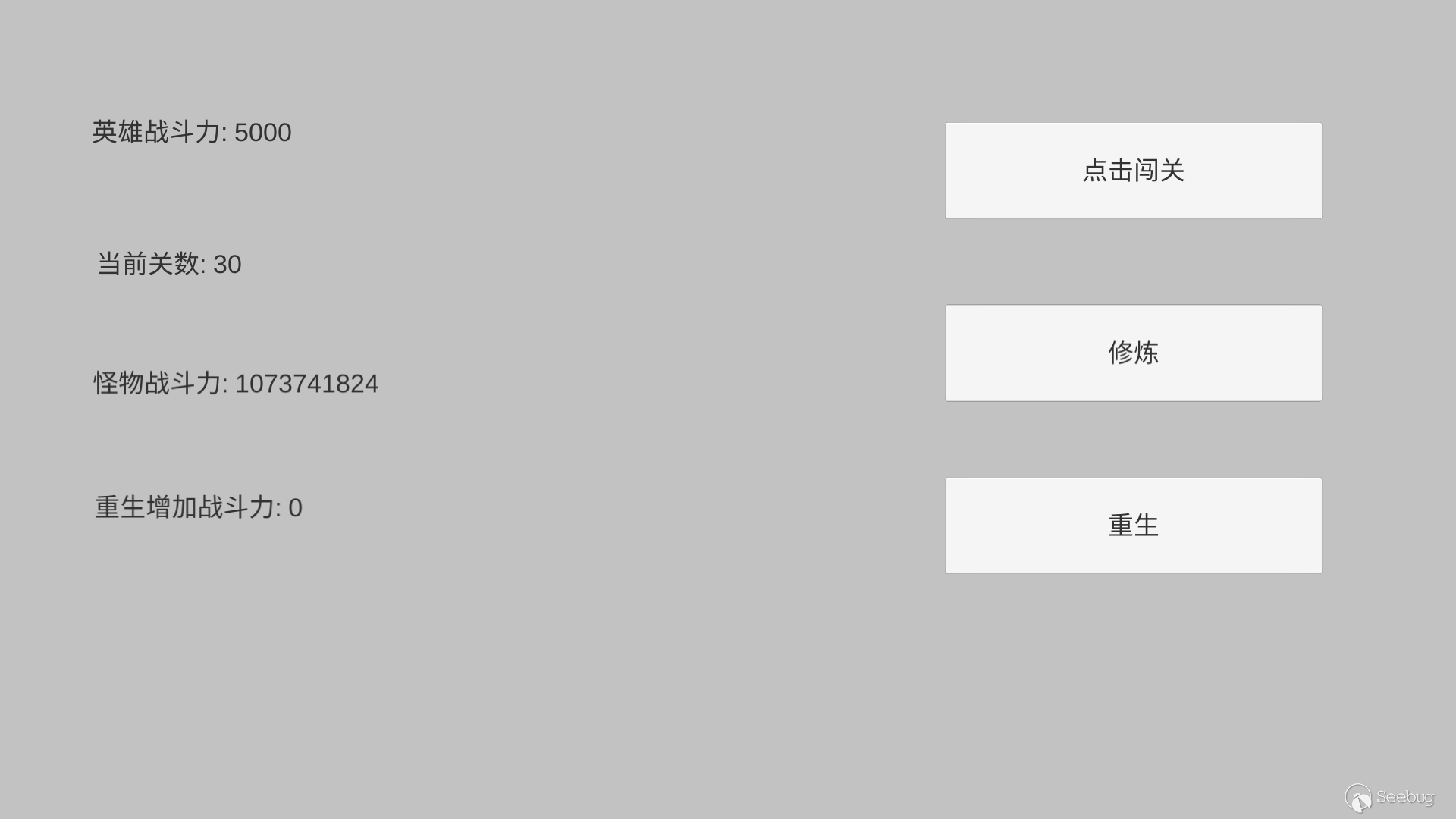
Reach the 30th level smoothly.
0x04 Conclusion
The obvious feature of Unity3D is that it will display the game LOGO at the beginning, which can be seen as a tip to judge whether a game is developed by Unity3D or not.
When the demo in this article reaches the 31st level, the integer overflow occurs and the monster’s combat power will become negative, which is because the monster's combat power is "int".
Adjusting the language of game to English before modification helps to understand the meaning of each function while reversing(for applications that have not been mixed).
It’s very easy to lose the original fun of the game after it has been modified, for it just becomes a pure digital game. Be cautious before modifying.
0x05 Reference
About Knownsec & 404 Team
Beijing Knownsec Information Technology Co., Ltd. was established by a group of high-profile international security experts. It has over a hundred frontier security talents nationwide as the core security research team to provide long-term internationally advanced network security solutions for the government and enterprises.
Knownsec's specialties include network attack and defense integrated technologies and product R&D under new situations. It provides visualization solutions that meet the world-class security technology standards and enhances the security monitoring, alarm and defense abilities of customer networks with its industry-leading capabilities in cloud computing and big data processing. The company's technical strength is spanly recognized by the State Ministry of Public Security, the Central Government Procurement Center, the Ministry of Industry and Information Technology (MIIT), China National Vulnerability Database of Information Security (CNNVD), the Central Bank, the Hong Kong Jockey Club, Microsoft, Zhejiang Satellite TV and other well-known clients.
404 Team, the core security team of Knownsec, is dedicated to the research of security vulnerability and offensive and defensive technology in the fields of Web, IoT, industrial control, blockchain, etc. 404 team has submitted vulnerability research to many well-known vendors such as Microsoft, Apple, Adobe, Tencent, Alibaba, Baidu, etc. And has received a high reputation in the industry.
The most well-known sharing of Knownsec 404 Team includes: KCon Hacking Conference, Seebug Vulnerability Database and ZoomEye Cyberspace Search Engine.
以上是 Modification in Reverse: Unity3D Android Games 的全部内容, 来源链接: utcz.com/p/199350.html