019.Kubernetes二进制部署插件dashboard

一 修改配置文件1.1 下载解压
1 [root@k8smaster01 ~]# cd /opt/k8s/work/kubernetes/ 2 [root@k8smaster01 kubernetes]# tar -xzvf kubernetes-src.tar.gz
提示:k8smaster01节点已解压完毕,可直接修改配置。1.2 修改配置
1 [root@k8smaster01 ~]# cd /opt/k8s/work/kubernetes/cluster/addons/dashboard 2 [root@k8smaster01 dashboard]# vi dashboard-service.yaml
3 ……
4 type: NodePort #增加此行,使用node形式访问
5 ……
6 #使用node方式访问dashboard
1.3 修改为国内源
1 [root@k8smaster01 dashboard]# vi dashboard-controller.yaml 2 ……
3 image: mirrorgooglecontainers/kubernetes-dashboard-amd64:v1.10.1
4 ……
提示:将yaml文件中的image字段修改为mirrorgooglecontainers/kubernetes-dashboard-amd64:v1.10.1。二 创建 dashboard2.1 创建dashboard并检查
1 [root@k8smaster01 ~]# cd /opt/k8s/work/kubernetes/cluster/addons/dashboard 2 [root@k8smaster01 dashboard]# kubectl apply -f .
2.2 查看分配的NodePort
1 [root@k8smaster01 ~]# kubectl get deployment kubernetes-dashboard -n kube-system 2 NAME READY UP-TO-DATE AVAILABLE AGE
3 kubernetes-dashboard 1/1 1 1 84s
4 [root@k8smaster01 ~]# kubectl --namespace kube-system get pods -o wide
5 [root@k8smaster01 ~]# kubectl get services kubernetes-dashboard -n kube-system
提示:k8smaster02 NodePort 31181 映射到 dashboard pod 443 端口。2.3 查看dashboard参数
1 [root@k8smaster01 ~]# kubectl exec --namespace kube-system -it kubernetes-dashboard-7848d45466-bgz94 -- /dashboard --help提示:dashboard 的 --authentication-mode 支持 token、basic,默认为 token。如果使用 basic,则 kube-apiserver 必须配置 --authorization-mode=ABAC 和 --basic-auth-file 参数。三 dashboard验证方式由于Kubernetes默认证书可能过期导致无法访问dashboard,本实验在已成功部署Kubernetes后手动重新创建证书。3.1 创建证书
1 [root@k8smaster01 ~]# cd /opt/k8s/work/ 2 [root@k8smaster01 work]# openssl genrsa -out dashboard.key 2048
3 [root@k8smaster01 work]# openssl rsa -passin pass:x -in dashboard.key -out dashboard.key
4 [root@k8smaster01 work]# openssl req -new -key dashboard.key -out dashboard.csr
5 -----
6 Country Name (2 letter code) [XX]:CN
7 State or Province Name (full name) []:Shanghai
8 Locality Name (eg, city) [Default City]:Shanghai
9 Organization Name (eg, company) [Default Company Ltd]:k8s
10 Organizational Unit Name (eg, section) []:System
11 [root@k8smaster01 work]# openssl x509 -req -sha256 -days 365 -in dashboard.csr -signkey dashboard.key -out dashboard.crt
12 [root@k8smaster01 work]# openssl x509 -noout -text -in ./dashboard.crt #查看证书
3.2 分发证书
1 [root@k8smaster01 ~]# cd /opt/k8s/work 2 [root@k8smaster01 work]# source /opt/k8s/bin/environment.sh
3 [root@k8smaster01 work]# for all_ip in ${ALL_IPS[@]}
4do
5 echo ">>> ${all_ip}"
6 scp dashboard.* root@${all_ip}:/etc/kubernetes/cert
7 done
3.3 修改默认证书配置
1 [root@k8smaster01 work]# cd /opt/k8s/work/kubernetes/cluster/addons/dashboard 2 [root@k8smaster01 dashboard]# kubectl delete -f . #删除使用默认证书所创建的dashboard
3 [root@k8smaster01 dashboard]# ll /etc/kubernetes/cert/dashboard.*
4 -rw-r--r-- 1 root root 1.2K Jun 28 18:06 /etc/kubernetes/cert/dashboard.crt
5 -rw-r--r-- 1 root root 976 Jun 28 18:06 /etc/kubernetes/cert/dashboard.csr
6 -rw-r--r-- 1 root root 1.7K Jun 28 18:06 /etc/kubernetes/cert/dashboard.key
7
8 [root@master dashboard]# kubectl create secret generic kubernetes-dashboard-certs --from-file="/etc/kubernetes/cert/dashboard.crt,/etc/kubernetes/cert/dashboard.key" -n kube-system #挂载新证书到dashboard
9 [root@master dashboard]# kubectl get secret kubernetes-dashboard-certs -n kube-system -o yaml #查看新证书
3.4 重新部署dashboard
1 [root@k8smaster01 work]# cd /opt/k8s/work/kubernetes/cluster/addons/dashboard 2 [root@master dashboard]# kubectl apply -f .
3 [root@master dashboard]# kubectl get pods --namespace=kube-system | grep dashboard #确认验证
3.5 确认验证
1 [root@k8smaster01 ~]# kubectl get deployment kubernetes-dashboard -n kube-system 2 [root@k8smaster01 ~]# kubectl --namespace kube-system get pods -o wide
3 [root@k8smaster01 ~]# kubectl get services kubernetes-dashboard -n kube-system
提示:k8smaster03 NodePort 30938 映射到 dashboard pod 443 端口。四 访问dashboard3.1 导入证书
将dashboard.crt导入IE浏览器,并设置为信任,导入操作略。3.2 访问方式
本实验采用nodeip:nodepord方式访问。浏览器访问:https://172.24.8.73:30938提示:更多dashboard访问方式及认证可参考《附004.Kubernetes Dashboard简介及使用》。dashboard登录整个流程可参考:https://www.cnadn.net/post/2613.htmapiserver方式见3.4,Kubeconfig验证方式见《附006.Kubernetes身份认证》中的3.5。五 验证方式5.1 创建token
1 [root@k8smaster01 ~]# kubectl create sa dashboard-admin -n kube-system 2 [root@k8smaster01 ~]# kubectl create clusterrolebinding dashboard-admin --clusterrole=cluster-admin --serviceaccount=kube-system:dashboard-admin
3 [root@k8smaster01 ~]# ADMIN_SECRET=$(kubectl get secrets -n kube-system | grep dashboard-admin | awk "{print $1}")
4 [root@k8smaster01 ~]# DASHBOARD_LOGIN_TOKEN=$(kubectl describe secret -n kube-system ${ADMIN_SECRET} | grep -E "^token" | awk "{print $2}")
5 [root@k8smaster01 ~]# echo ${DASHBOARD_LOGIN_TOKEN} #输入登录的token
6 eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tdmc5bWgiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiZTlkNGRjNGUtOTk3OC0xMWU5LTkzNTItMDAwYzI5ZmE3YTc5Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.X1NJsPNaAgV2TzJo0NlqOWFofDYOsSdkeiYHFGQFk5nNy0nbbnfnnoH0yumj_Ld0nGPakIjEpsUq9dqgCazeCpgk5EsygD6UlSg5sYA2sTLswbDoZdS3QzrOjY5MXWD3VDc_OQofD94MZqHMMw7IABVlfVsZ0vMEvHe-Qtyt6EQlFlHq5QjwDX8dCQDKRbwuiCr-Iy_dCWHHIhaT25BREf2viei8sZ497D8h4TXgO_u2CGf3qXRGNXj26VSdD8bT-BFGiDdyuXPbDHPU5LalvxF4WThChRfjO4zHLI2fOXq8BBF6DjbjhtG4X8fLuvJaxF4YWAmVS_78eJHhA3nvRg
3.4 创建kubeconfig文件
使用token相对复杂,可将token添加至kubeconfig文件中,使用KubeConfig 文件访问dashboard。 1 [root@k8smaster01 ~]# cd /opt/k8s/work/ 2 [root@k8smaster01 work]# source /opt/k8s/bin/environment.sh
3 [root@k8smaster01 work]# kubectl config set-cluster kubernetes
4 --certificate-authority=/etc/kubernetes/cert/ca.pem
5 --embed-certs=true
6 --server=${KUBE_APISERVER}
7 --kubeconfig=dashboard.kubeconfig # 设置集群参数
8 [root@k8smaster01 work]# kubectl config set-credentials dashboard_user
9 --token=${DASHBOARD_LOGIN_TOKEN}
10 --kubeconfig=dashboard.kubeconfig # 设置客户端认证参数,使用上面创建的 Token
11 [root@k8smaster01 work]# kubectl config set-context default
12 --cluster=kubernetes
13 --user=dashboard_user
14 --kubeconfig=dashboard.kubeconfig # 设置上下文参数
15 [root@k8smaster01 work]# kubectl config use-context default --kubeconfig=dashboard.kubeconfig # 设置默认上下文,将dashboard.kubeconfig文件导入,以便于浏览器使用该文件登录。
六 正式登录6.1 kubeconfig访问
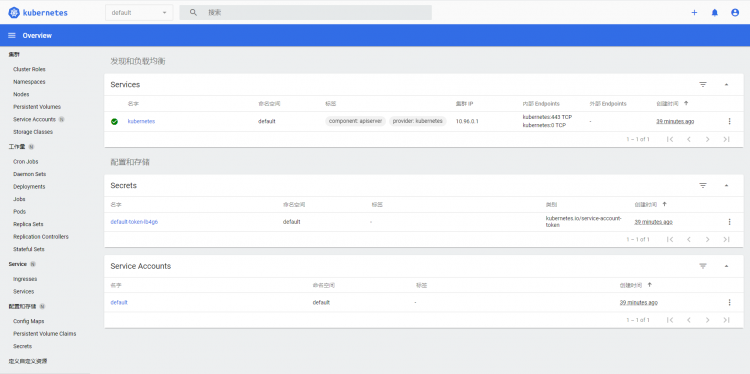
浏览器访问:https://172.24.8.73:30938
提示:由于缺少 Heapster 插件,当前 dashboard 不能展示 Pod、Nodes 的 CPU、内存等统计数据和图表。
2 [root@k8smaster01 kubernetes]# tar -xzvf kubernetes-src.tar.gz
2 [root@k8smaster01 dashboard]# vi dashboard-service.yaml
3 ……
4 type: NodePort #增加此行,使用node形式访问
5 ……
6 #使用node方式访问dashboard
2 ……
3 image: mirrorgooglecontainers/kubernetes-dashboard-amd64:v1.10.1
4 ……
2.1 创建dashboard并检查
1 [root@k8smaster01 ~]# cd /opt/k8s/work/kubernetes/cluster/addons/dashboard2 [root@k8smaster01 dashboard]# kubectl apply -f .
2.2 查看分配的NodePort
1 [root@k8smaster01 ~]# kubectl get deployment kubernetes-dashboard -n kube-system提示:k8smaster02 NodePort 31181 映射到 dashboard pod 443 端口。2 NAME READY UP-TO-DATE AVAILABLE AGE
3 kubernetes-dashboard 1/1 1 1 84s
4 [root@k8smaster01 ~]# kubectl --namespace kube-system get pods -o wide
5 [root@k8smaster01 ~]# kubectl get services kubernetes-dashboard -n kube-system
2.3 查看dashboard参数
1 [root@k8smaster01 ~]# kubectl exec --namespace kube-system -it kubernetes-dashboard-7848d45466-bgz94 -- /dashboard --help提示:dashboard 的 --authentication-mode 支持 token、basic,默认为 token。如果使用 basic,则 kube-apiserver 必须配置 --authorization-mode=ABAC 和 --basic-auth-file 参数。三 dashboard验证方式由于Kubernetes默认证书可能过期导致无法访问dashboard,本实验在已成功部署Kubernetes后手动重新创建证书。3.1 创建证书
1 [root@k8smaster01 ~]# cd /opt/k8s/work/ 2 [root@k8smaster01 work]# openssl genrsa -out dashboard.key 2048
3 [root@k8smaster01 work]# openssl rsa -passin pass:x -in dashboard.key -out dashboard.key
4 [root@k8smaster01 work]# openssl req -new -key dashboard.key -out dashboard.csr
5 -----
6 Country Name (2 letter code) [XX]:CN
7 State or Province Name (full name) []:Shanghai
8 Locality Name (eg, city) [Default City]:Shanghai
9 Organization Name (eg, company) [Default Company Ltd]:k8s
10 Organizational Unit Name (eg, section) []:System
11 [root@k8smaster01 work]# openssl x509 -req -sha256 -days 365 -in dashboard.csr -signkey dashboard.key -out dashboard.crt
12 [root@k8smaster01 work]# openssl x509 -noout -text -in ./dashboard.crt #查看证书
3.2 分发证书
1 [root@k8smaster01 ~]# cd /opt/k8s/work 2 [root@k8smaster01 work]# source /opt/k8s/bin/environment.sh
3 [root@k8smaster01 work]# for all_ip in ${ALL_IPS[@]}
4do
5 echo ">>> ${all_ip}"
6 scp dashboard.* root@${all_ip}:/etc/kubernetes/cert
7 done
3.3 修改默认证书配置
1 [root@k8smaster01 work]# cd /opt/k8s/work/kubernetes/cluster/addons/dashboard 2 [root@k8smaster01 dashboard]# kubectl delete -f . #删除使用默认证书所创建的dashboard
3 [root@k8smaster01 dashboard]# ll /etc/kubernetes/cert/dashboard.*
4 -rw-r--r-- 1 root root 1.2K Jun 28 18:06 /etc/kubernetes/cert/dashboard.crt
5 -rw-r--r-- 1 root root 976 Jun 28 18:06 /etc/kubernetes/cert/dashboard.csr
6 -rw-r--r-- 1 root root 1.7K Jun 28 18:06 /etc/kubernetes/cert/dashboard.key
7
8 [root@master dashboard]# kubectl create secret generic kubernetes-dashboard-certs --from-file="/etc/kubernetes/cert/dashboard.crt,/etc/kubernetes/cert/dashboard.key" -n kube-system #挂载新证书到dashboard
9 [root@master dashboard]# kubectl get secret kubernetes-dashboard-certs -n kube-system -o yaml #查看新证书
3.4 重新部署dashboard
1 [root@k8smaster01 work]# cd /opt/k8s/work/kubernetes/cluster/addons/dashboard 2 [root@master dashboard]# kubectl apply -f .
3 [root@master dashboard]# kubectl get pods --namespace=kube-system | grep dashboard #确认验证
3.5 确认验证
1 [root@k8smaster01 ~]# kubectl get deployment kubernetes-dashboard -n kube-system 2 [root@k8smaster01 ~]# kubectl --namespace kube-system get pods -o wide
3 [root@k8smaster01 ~]# kubectl get services kubernetes-dashboard -n kube-system
提示:k8smaster03 NodePort 30938 映射到 dashboard pod 443 端口。四 访问dashboard3.1 导入证书
将dashboard.crt导入IE浏览器,并设置为信任,导入操作略。3.2 访问方式
本实验采用nodeip:nodepord方式访问。浏览器访问:https://172.24.8.73:30938提示:更多dashboard访问方式及认证可参考《附004.Kubernetes Dashboard简介及使用》。dashboard登录整个流程可参考:https://www.cnadn.net/post/2613.htmapiserver方式见3.4,Kubeconfig验证方式见《附006.Kubernetes身份认证》中的3.5。五 验证方式5.1 创建token
1 [root@k8smaster01 ~]# kubectl create sa dashboard-admin -n kube-system 2 [root@k8smaster01 ~]# kubectl create clusterrolebinding dashboard-admin --clusterrole=cluster-admin --serviceaccount=kube-system:dashboard-admin
3 [root@k8smaster01 ~]# ADMIN_SECRET=$(kubectl get secrets -n kube-system | grep dashboard-admin | awk "{print $1}")
4 [root@k8smaster01 ~]# DASHBOARD_LOGIN_TOKEN=$(kubectl describe secret -n kube-system ${ADMIN_SECRET} | grep -E "^token" | awk "{print $2}")
5 [root@k8smaster01 ~]# echo ${DASHBOARD_LOGIN_TOKEN} #输入登录的token
6 eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tdmc5bWgiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiZTlkNGRjNGUtOTk3OC0xMWU5LTkzNTItMDAwYzI5ZmE3YTc5Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.X1NJsPNaAgV2TzJo0NlqOWFofDYOsSdkeiYHFGQFk5nNy0nbbnfnnoH0yumj_Ld0nGPakIjEpsUq9dqgCazeCpgk5EsygD6UlSg5sYA2sTLswbDoZdS3QzrOjY5MXWD3VDc_OQofD94MZqHMMw7IABVlfVsZ0vMEvHe-Qtyt6EQlFlHq5QjwDX8dCQDKRbwuiCr-Iy_dCWHHIhaT25BREf2viei8sZ497D8h4TXgO_u2CGf3qXRGNXj26VSdD8bT-BFGiDdyuXPbDHPU5LalvxF4WThChRfjO4zHLI2fOXq8BBF6DjbjhtG4X8fLuvJaxF4YWAmVS_78eJHhA3nvRg
3.4 创建kubeconfig文件
使用token相对复杂,可将token添加至kubeconfig文件中,使用KubeConfig 文件访问dashboard。 1 [root@k8smaster01 ~]# cd /opt/k8s/work/ 2 [root@k8smaster01 work]# source /opt/k8s/bin/environment.sh
3 [root@k8smaster01 work]# kubectl config set-cluster kubernetes
4 --certificate-authority=/etc/kubernetes/cert/ca.pem
5 --embed-certs=true
6 --server=${KUBE_APISERVER}
7 --kubeconfig=dashboard.kubeconfig # 设置集群参数
8 [root@k8smaster01 work]# kubectl config set-credentials dashboard_user
9 --token=${DASHBOARD_LOGIN_TOKEN}
10 --kubeconfig=dashboard.kubeconfig # 设置客户端认证参数,使用上面创建的 Token
11 [root@k8smaster01 work]# kubectl config set-context default
12 --cluster=kubernetes
13 --user=dashboard_user
14 --kubeconfig=dashboard.kubeconfig # 设置上下文参数
15 [root@k8smaster01 work]# kubectl config use-context default --kubeconfig=dashboard.kubeconfig # 设置默认上下文,将dashboard.kubeconfig文件导入,以便于浏览器使用该文件登录。
六 正式登录6.1 kubeconfig访问
浏览器访问:https://172.24.8.73:30938
提示:由于缺少 Heapster 插件,当前 dashboard 不能展示 Pod、Nodes 的 CPU、内存等统计数据和图表。
2 [root@k8smaster01 work]# openssl genrsa -out dashboard.key 2048
3 [root@k8smaster01 work]# openssl rsa -passin pass:x -in dashboard.key -out dashboard.key
4 [root@k8smaster01 work]# openssl req -new -key dashboard.key -out dashboard.csr
5 -----
6 Country Name (2 letter code) [XX]:CN
7 State or Province Name (full name) []:Shanghai
8 Locality Name (eg, city) [Default City]:Shanghai
9 Organization Name (eg, company) [Default Company Ltd]:k8s
10 Organizational Unit Name (eg, section) []:System
11 [root@k8smaster01 work]# openssl x509 -req -sha256 -days 365 -in dashboard.csr -signkey dashboard.key -out dashboard.crt
12 [root@k8smaster01 work]# openssl x509 -noout -text -in ./dashboard.crt #查看证书
2 [root@k8smaster01 work]# source /opt/k8s/bin/environment.sh
3 [root@k8smaster01 work]# for all_ip in ${ALL_IPS[@]}
4do
5 echo ">>> ${all_ip}"
6 scp dashboard.* root@${all_ip}:/etc/kubernetes/cert
7 done
2 [root@k8smaster01 dashboard]# kubectl delete -f . #删除使用默认证书所创建的dashboard
3 [root@k8smaster01 dashboard]# ll /etc/kubernetes/cert/dashboard.*
4 -rw-r--r-- 1 root root 1.2K Jun 28 18:06 /etc/kubernetes/cert/dashboard.crt
5 -rw-r--r-- 1 root root 976 Jun 28 18:06 /etc/kubernetes/cert/dashboard.csr
6 -rw-r--r-- 1 root root 1.7K Jun 28 18:06 /etc/kubernetes/cert/dashboard.key
7
8 [root@master dashboard]# kubectl create secret generic kubernetes-dashboard-certs --from-file="/etc/kubernetes/cert/dashboard.crt,/etc/kubernetes/cert/dashboard.key" -n kube-system #挂载新证书到dashboard
9 [root@master dashboard]# kubectl get secret kubernetes-dashboard-certs -n kube-system -o yaml #查看新证书
2 [root@master dashboard]# kubectl apply -f .
3 [root@master dashboard]# kubectl get pods --namespace=kube-system | grep dashboard #确认验证
2 [root@k8smaster01 ~]# kubectl --namespace kube-system get pods -o wide
3 [root@k8smaster01 ~]# kubectl get services kubernetes-dashboard -n kube-system
3.1 导入证书
将dashboard.crt导入IE浏览器,并设置为信任,导入操作略。3.2 访问方式
本实验采用nodeip:nodepord方式访问。浏览器访问:https://172.24.8.73:30938提示:更多dashboard访问方式及认证可参考《附004.Kubernetes Dashboard简介及使用》。dashboard登录整个流程可参考:https://www.cnadn.net/post/2613.htmapiserver方式见3.4,Kubeconfig验证方式见《附006.Kubernetes身份认证》中的3.5。五 验证方式5.1 创建token
1 [root@k8smaster01 ~]# kubectl create sa dashboard-admin -n kube-system 2 [root@k8smaster01 ~]# kubectl create clusterrolebinding dashboard-admin --clusterrole=cluster-admin --serviceaccount=kube-system:dashboard-admin
3 [root@k8smaster01 ~]# ADMIN_SECRET=$(kubectl get secrets -n kube-system | grep dashboard-admin | awk "{print $1}")
4 [root@k8smaster01 ~]# DASHBOARD_LOGIN_TOKEN=$(kubectl describe secret -n kube-system ${ADMIN_SECRET} | grep -E "^token" | awk "{print $2}")
5 [root@k8smaster01 ~]# echo ${DASHBOARD_LOGIN_TOKEN} #输入登录的token
6 eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tdmc5bWgiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiZTlkNGRjNGUtOTk3OC0xMWU5LTkzNTItMDAwYzI5ZmE3YTc5Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.X1NJsPNaAgV2TzJo0NlqOWFofDYOsSdkeiYHFGQFk5nNy0nbbnfnnoH0yumj_Ld0nGPakIjEpsUq9dqgCazeCpgk5EsygD6UlSg5sYA2sTLswbDoZdS3QzrOjY5MXWD3VDc_OQofD94MZqHMMw7IABVlfVsZ0vMEvHe-Qtyt6EQlFlHq5QjwDX8dCQDKRbwuiCr-Iy_dCWHHIhaT25BREf2viei8sZ497D8h4TXgO_u2CGf3qXRGNXj26VSdD8bT-BFGiDdyuXPbDHPU5LalvxF4WThChRfjO4zHLI2fOXq8BBF6DjbjhtG4X8fLuvJaxF4YWAmVS_78eJHhA3nvRg
3.4 创建kubeconfig文件
使用token相对复杂,可将token添加至kubeconfig文件中,使用KubeConfig 文件访问dashboard。 1 [root@k8smaster01 ~]# cd /opt/k8s/work/ 2 [root@k8smaster01 work]# source /opt/k8s/bin/environment.sh
3 [root@k8smaster01 work]# kubectl config set-cluster kubernetes
4 --certificate-authority=/etc/kubernetes/cert/ca.pem
5 --embed-certs=true
6 --server=${KUBE_APISERVER}
7 --kubeconfig=dashboard.kubeconfig # 设置集群参数
8 [root@k8smaster01 work]# kubectl config set-credentials dashboard_user
9 --token=${DASHBOARD_LOGIN_TOKEN}
10 --kubeconfig=dashboard.kubeconfig # 设置客户端认证参数,使用上面创建的 Token
11 [root@k8smaster01 work]# kubectl config set-context default
12 --cluster=kubernetes
13 --user=dashboard_user
14 --kubeconfig=dashboard.kubeconfig # 设置上下文参数
15 [root@k8smaster01 work]# kubectl config use-context default --kubeconfig=dashboard.kubeconfig # 设置默认上下文,将dashboard.kubeconfig文件导入,以便于浏览器使用该文件登录。
六 正式登录6.1 kubeconfig访问
浏览器访问:https://172.24.8.73:30938
提示:由于缺少 Heapster 插件,当前 dashboard 不能展示 Pod、Nodes 的 CPU、内存等统计数据和图表。
2 [root@k8smaster01 ~]# kubectl create clusterrolebinding dashboard-admin --clusterrole=cluster-admin --serviceaccount=kube-system:dashboard-admin
3 [root@k8smaster01 ~]# ADMIN_SECRET=$(kubectl get secrets -n kube-system | grep dashboard-admin | awk "{print $1}")
4 [root@k8smaster01 ~]# DASHBOARD_LOGIN_TOKEN=$(kubectl describe secret -n kube-system ${ADMIN_SECRET} | grep -E "^token" | awk "{print $2}")
5 [root@k8smaster01 ~]# echo ${DASHBOARD_LOGIN_TOKEN} #输入登录的token
6 eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tdmc5bWgiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiZTlkNGRjNGUtOTk3OC0xMWU5LTkzNTItMDAwYzI5ZmE3YTc5Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.X1NJsPNaAgV2TzJo0NlqOWFofDYOsSdkeiYHFGQFk5nNy0nbbnfnnoH0yumj_Ld0nGPakIjEpsUq9dqgCazeCpgk5EsygD6UlSg5sYA2sTLswbDoZdS3QzrOjY5MXWD3VDc_OQofD94MZqHMMw7IABVlfVsZ0vMEvHe-Qtyt6EQlFlHq5QjwDX8dCQDKRbwuiCr-Iy_dCWHHIhaT25BREf2viei8sZ497D8h4TXgO_u2CGf3qXRGNXj26VSdD8bT-BFGiDdyuXPbDHPU5LalvxF4WThChRfjO4zHLI2fOXq8BBF6DjbjhtG4X8fLuvJaxF4YWAmVS_78eJHhA3nvRg
2 [root@k8smaster01 work]# source /opt/k8s/bin/environment.sh
3 [root@k8smaster01 work]# kubectl config set-cluster kubernetes
4 --certificate-authority=/etc/kubernetes/cert/ca.pem
5 --embed-certs=true
6 --server=${KUBE_APISERVER}
7 --kubeconfig=dashboard.kubeconfig # 设置集群参数
8 [root@k8smaster01 work]# kubectl config set-credentials dashboard_user
9 --token=${DASHBOARD_LOGIN_TOKEN}
10 --kubeconfig=dashboard.kubeconfig # 设置客户端认证参数,使用上面创建的 Token
11 [root@k8smaster01 work]# kubectl config set-context default
12 --cluster=kubernetes
13 --user=dashboard_user
14 --kubeconfig=dashboard.kubeconfig # 设置上下文参数
15 [root@k8smaster01 work]# kubectl config use-context default --kubeconfig=dashboard.kubeconfig # 设置默认上下文,将dashboard.kubeconfig文件导入,以便于浏览器使用该文件登录。
6.1 kubeconfig访问
浏览器访问:https://172.24.8.73:30938提示:由于缺少 Heapster 插件,当前 dashboard 不能展示 Pod、Nodes 的 CPU、内存等统计数据和图表。
以上是 019.Kubernetes二进制部署插件dashboard 的全部内容, 来源链接: utcz.com/z/510925.html