Lucky Ransomware Analysis and File Decryption
Author:Hcamael & 0x7F@Knownsec 404 Team
Date: December 4, 2018
Chinese Version: https://paper.seebug.org/758/
0x00 Preface
Recently, a ransomware called lucky broke out on the Internet. This ransomware encrypts the specified file and modifies the suffix to .lucky.
Knownsec 404 Team's 'refining pot' honeypot system first captured related traffic of this ransomware on November 10, 2018. The CNC server of the ransomware is still alive till December 4, 2018.
According to the analysis, it is known that the lucky ransomware is almost the Satan ransomware, since the overall structure has not changed much, and the CNC server has not changed as well. The Satan ransomware changed over time: it switched from profiting from blackmail to mining, and the new version of the lucky ransomware has combined extortion with mining.
Knownsec 404 Team quickly followed and analyzed the ransomware. We focused on analyzing the cryptographic module of the ransomware, and unexpectedly found that the pseudo-random number can be used to restore the encryption key. And we successfully decrypted the file. The link of decryption script in Python is: https://github.com/knownsec/Decrypt-ransomware.
This article provides an overview of the lucky ransomware and focuses on the encryption process and the process of restoring keys.
0x01 Introduction of Lucky Ransomware
Lucky ransomware can be spread and executed on Windows and Linux platforms. Its main functions are "file encryption", "propagation infection" and "mining".
Encrypt documents
Lucky ransomware traverses the folder, encrypts the file with the following suffix name, and modifies the suffix to .lucky:
bak,sql,mdf,ldf,myd,myi,dmp,xls,xlsx,docx,pptx,eps,txt,ppt,csv,rtf,pdf,db,vdi,vmdk,vmx,pem,pfx,cer,psd
In order to make sure that the system can run normally, the ransomware will skip the system key directory when encrypting, such as:
Windows: windows, microsoft games, 360rec, windows mail .etcLinux: /bin/, /boot/, /lib/, /usr/bin/ .etc
Spread infection
The lucky ransomware propagation module does not have new features and still uses the following vulnerabilities to spread:
1.JBoss deserialization vulnerability(CVE-2013-4810)2.JBoss default configuration vulnerability(CVE-2010-0738)
3.Tomcat file uploading vulnerability(CVE-2017-12615)
4.Tomcat web management backstage weak password blasting
5.Weblogic WLS component vulnerability(CVE-2017-10271)
6.Windows SMB remote code execution vulnerability MS17-010
7.Apache Struts2 remote code execution vulnerability S2-045
8.Apache Struts2 remote code execution vulnerability S2-057
Mining
The ransomware uses the self-built mine pool address: 194.88.155.5:443, and wants to gain extra profits through mining. At the same time, the pool address is the same address the Satan ransomware variant uses.
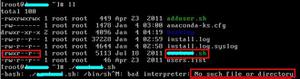
Screenshot
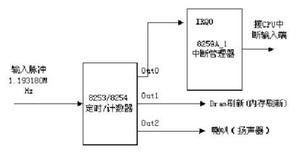
0x02 Ransomware Flow Chart
The overall structure of the lucky ransomware continues the structure of the Satan ransomware, including the following components:
Preloader: fast.exe/ft32, a very small file for loading cryptographic modules and propagation modulesEncryption module: cpt.exe/cry32, encrypts files
Propagation module: conn.exe/conn32, spreads and infects by using multiple application vulnerabilities
Mining module: mn32.exe/mn32, connects self-built mine pool address
Service module: srv.exe, creates a service under Windows for stable execution
The flow chart is roughly as follows:
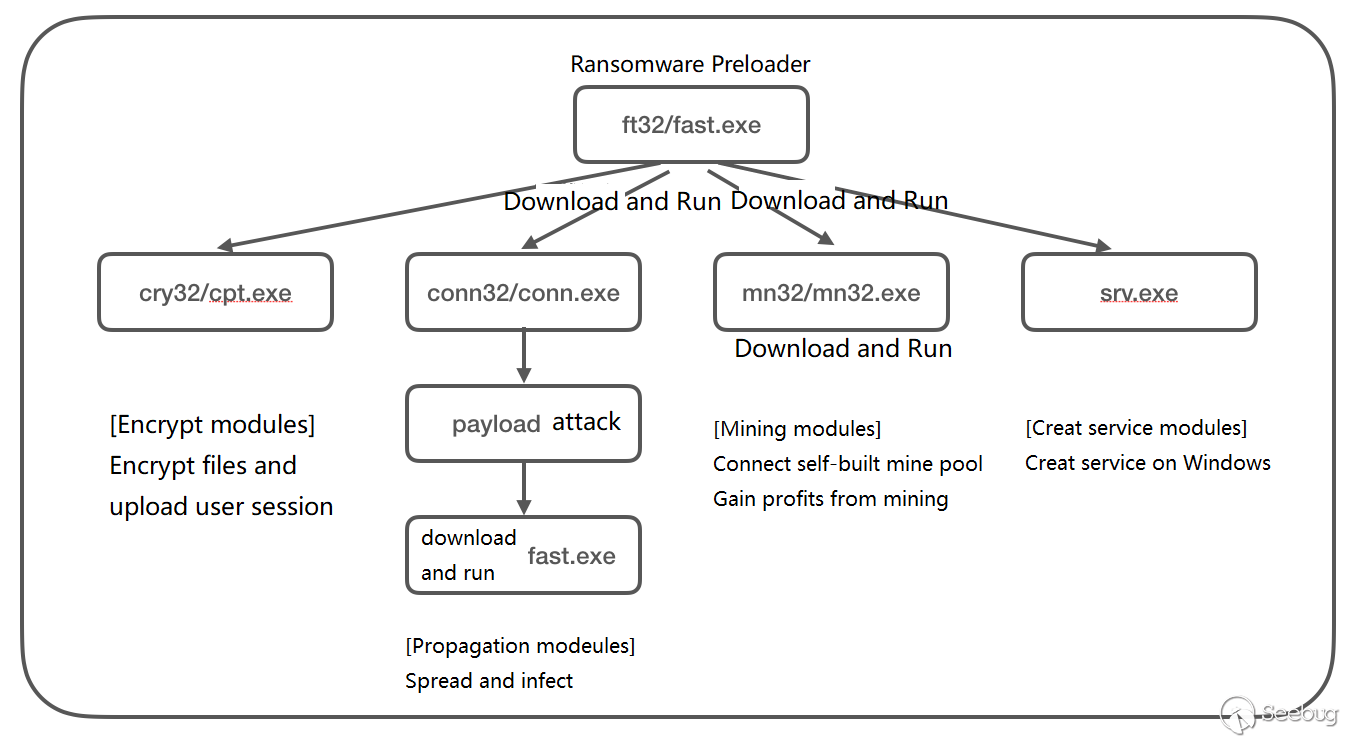
Every module of the lucky ransomware uses a common shell for shell protection, such as UPX, MPRESS, which can be automatically unpacked by using common unpack software.
0x03 Encryption Process
For a ransomware, the most important thing is its cryptographic module. For lucky ransomware, the cryptographic module is a separate executable file. The cryptographic module is analyzed in detail below. (using cpt.exe under Windows as an example of analysis)
1. Take off upx
cpt.exe uses upx for shelling and can be unpacked by using common unpack tools.
2. Encrypt main function
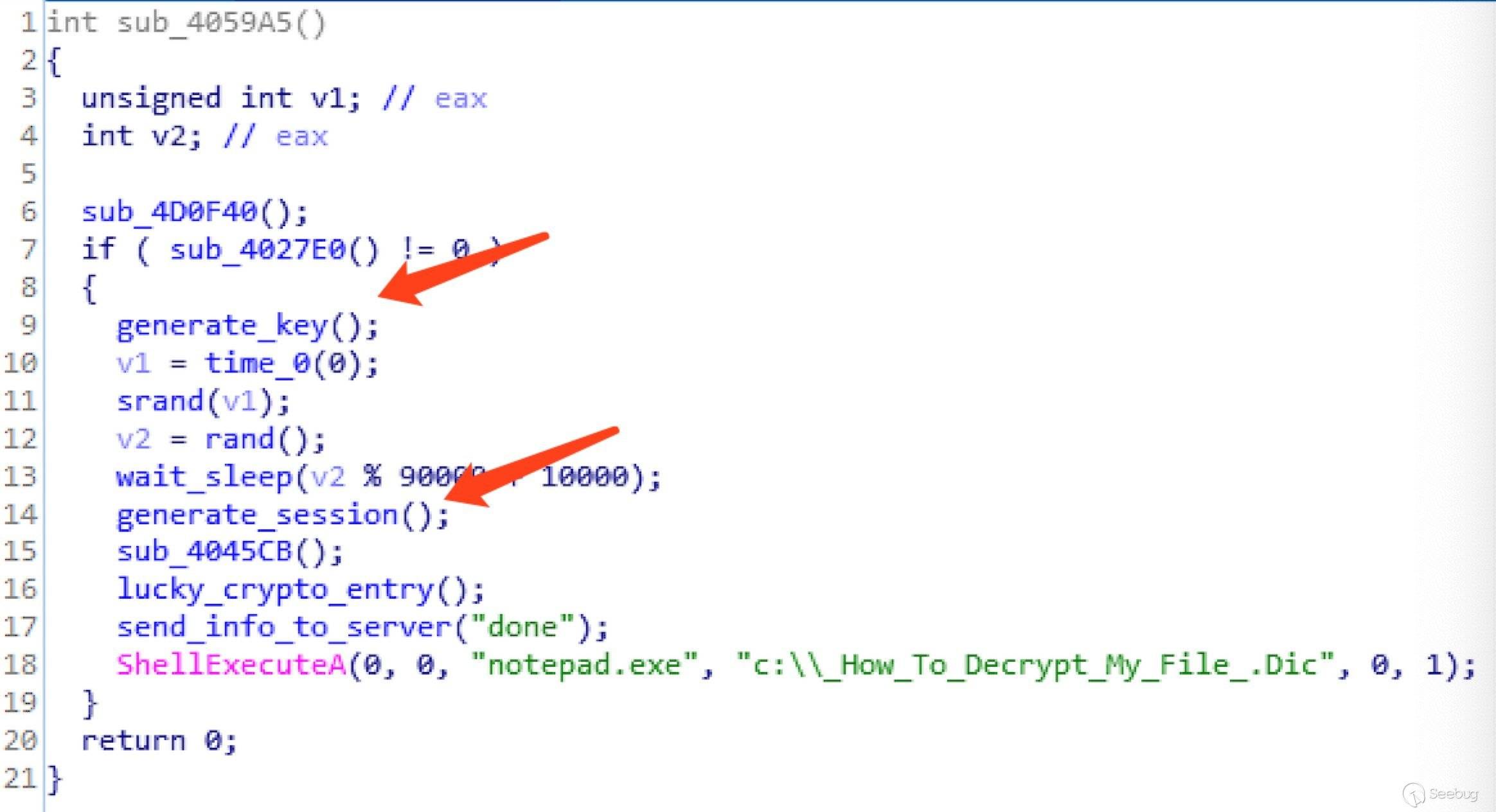
Use IDA to load the unpacked cpt.exe.unp. There are a lot of initialization operations in the main function. Ignore these operations and follow the function to find the main function of the encryption logic. These functions are labeled as follows:
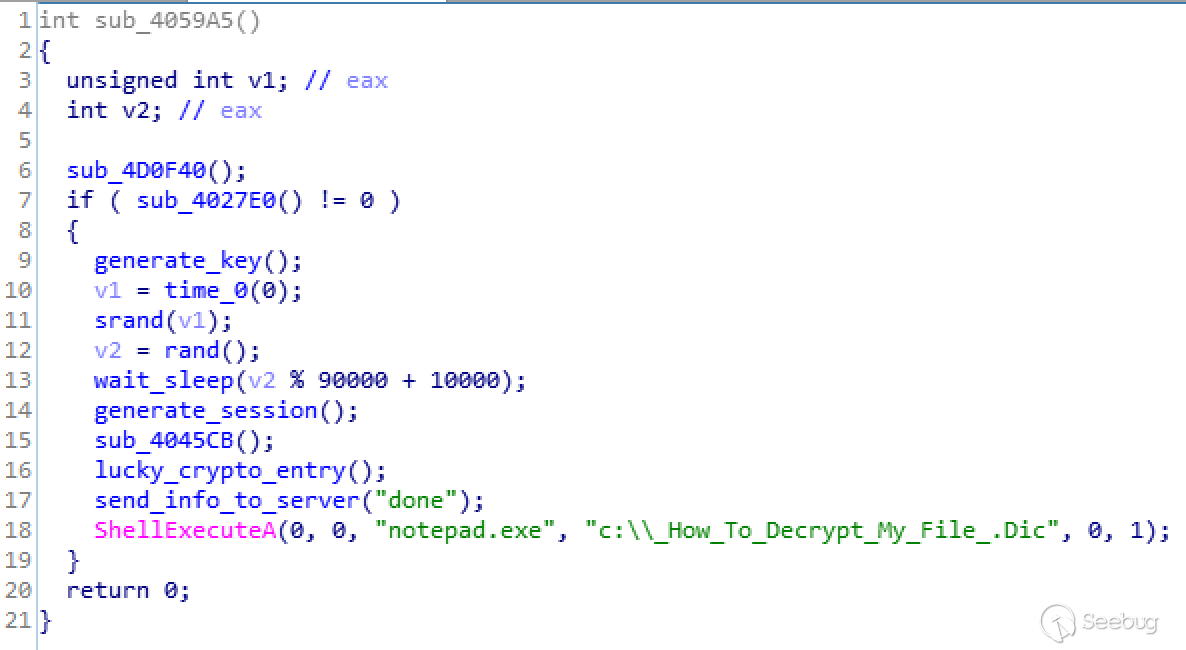
generate_key: Generates a 60-bit random string for subsequent encrypted files.
wait_sleep: Waits for a while.
generate_session: Generates a 16-bit random string as the user's session.
lucky_crypto_entry: Function of the specific encrypted file.
send_info_to_server: Reports the completion of encryption to the server.
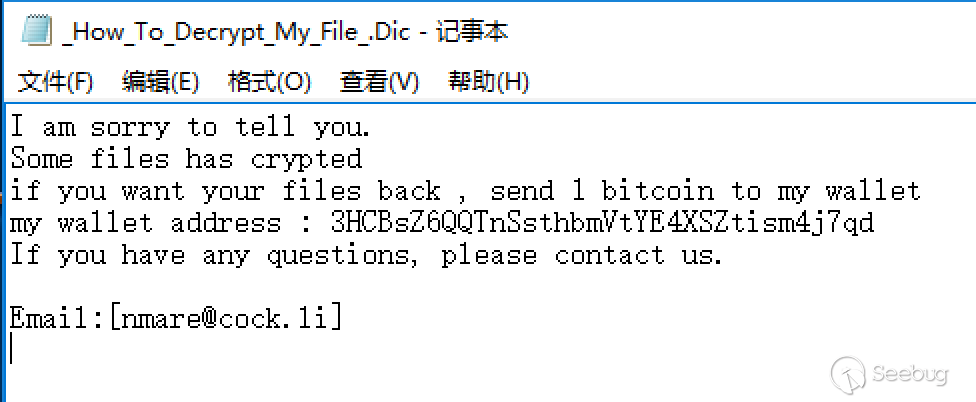
The approximate encryption process is as the functions above. Finally, a file c:\\_How_To_Decrypt_My_File_.Dic is written to notify the user that it has been encrypted by the ransomware and the bitcoin address is left.
3. generate_key()
This function generates an encryption key. It uses a random number to randomly selects characters from a preset sequence of strings to form a 60-byte key.
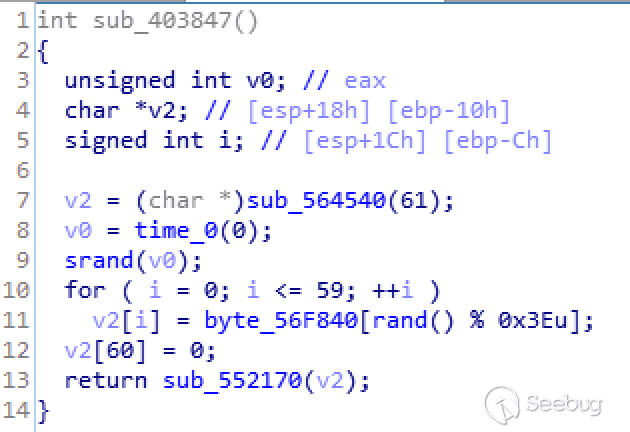
byte_56F840 is a preset string sequence:
ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz01234567894. generate_session()
This function is used by the cryptographic module to generate an identifier to distinguish every user. It also use random numbers to randomly selects characters from the preset string sequence, and finally forms a 16-byte session, which will be saved to the file in C:\\Windows\\Temp\\Ssession.
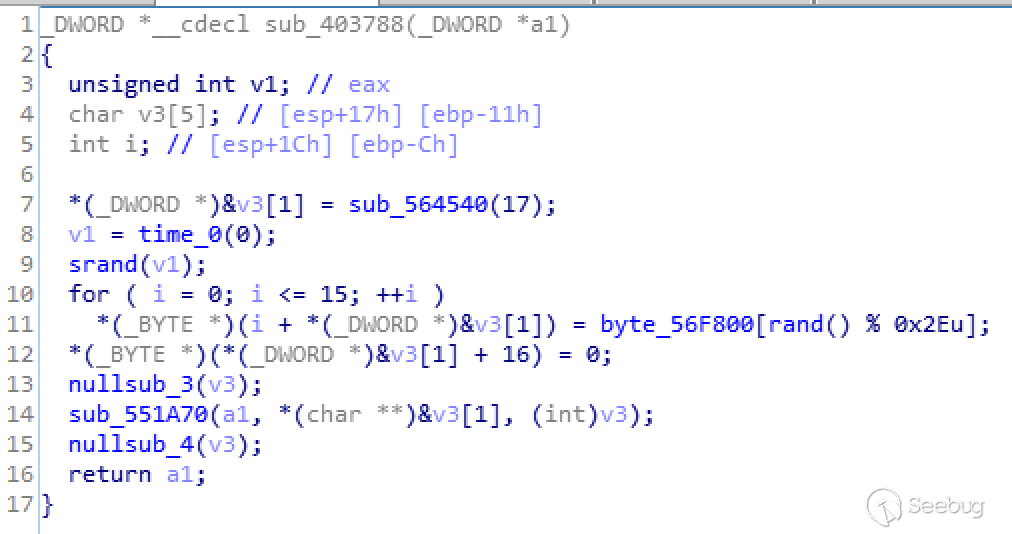
The string byte_56F800 is:
ABCDEFGHIJPQRSTUVWdefghijklmnopqrstuvwx34567895. lucky_crypto_entry()
Format of File's Name
This function is the entry of the encrypted file, and the format of the encrypted file's name is spliced in advance as follows:
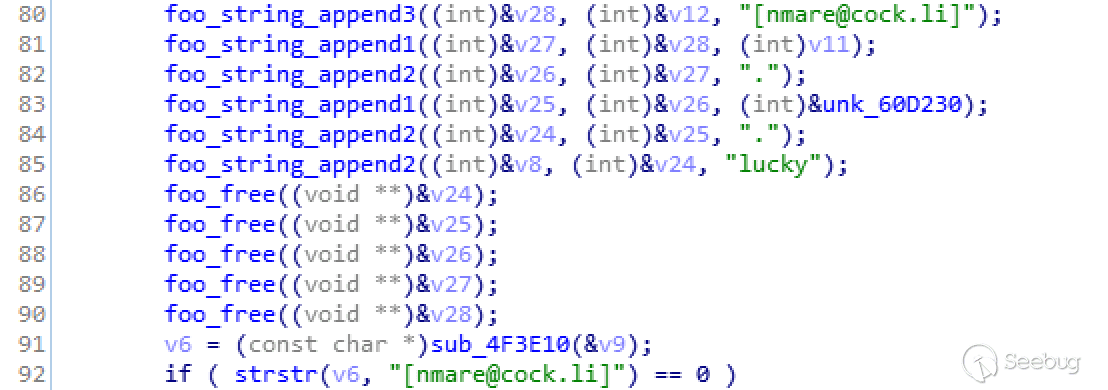
The format of the encrypted file's name is as follows:
[nmare@cock.li]filename.AiVjdtlUjI9m45f6.luckyWhere filename is the name of the file itself, and the subsequent string is the user's session.
Notify the Server
Before encryption, an HTTP message is first sent to the server to inform the server that the user has started encrypting:
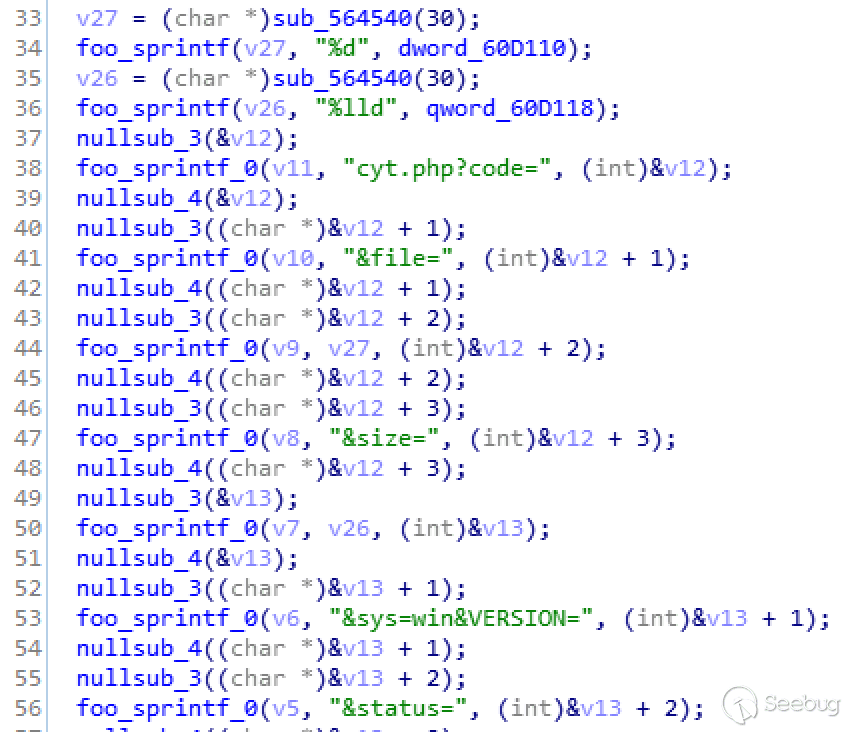
The HTTP packet format is as the following:
GET /cyt.php?code=AiVjdtlUjI9m45f6&file=1&size=0&sys=win&VERSION=4.4&status=begin HTTP/1.1Filter Files
In the cryptographic module, lucky encrypts the file with the specified suffix name:
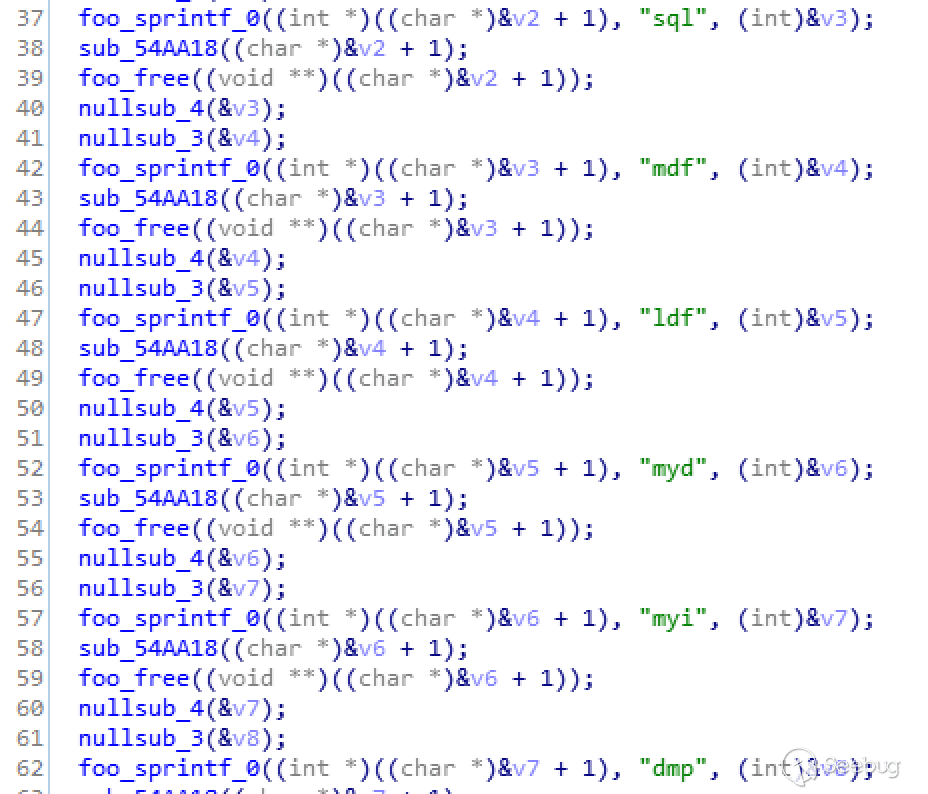
The encrypted suffix file includes:
Bak, sql, mdf, ldf, myd, myi, dmp, xls, xlsx, docx, pptx, eps,Txt, ppt, csv, rtf, pdf, db, vdi, vmdk, vmx, pem, pfx, cer, psd
6.AES_ECB encryption method
Lucky uses the previously generated 60-bytes key, takes the first 32 bytes for encryption, reads the file in turn, and performs AEC_ECB encryption every 16 bytes.
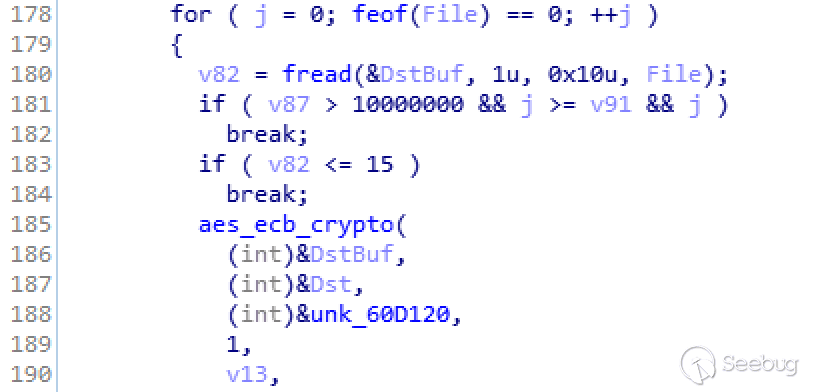
In addition, it can be known from the context of the encryption function that the ransomware has different ways of processing for different sizes of files. Here we assume that there are n bytes in the file:
- For portions that are less than 16 bytes at the end, no encryption
- If n > 10000000 bytes, and when n > 99999999 bytes, divide the file into n / 80 blocks, encrypts n / 16 blocks in the front
- If n > 10000000 bytes, and when 99999999 <= n <= 499999999 bytes, divide the file into n / 480 blocks, encrypts n / 16 blocks in the front
- If n > 10000000 bytes, and when n > 499999999 bytes, divide the file into n / 1280 blocks, encrypts n / 16 blocks in the front
After each file is encrypted, the ransomware will package and add the AES key to the end of the file by using the RSA algorithm.
7. Encryption completion
After all files have been encrypted, lucky sends a message to the server again, indicating that the user has completed the encryption. Then it alerts the user of running into the ransomware encryption in c:\\_How_To_Decrypt_My_File_.Dic.
File comparison before and after encryption:
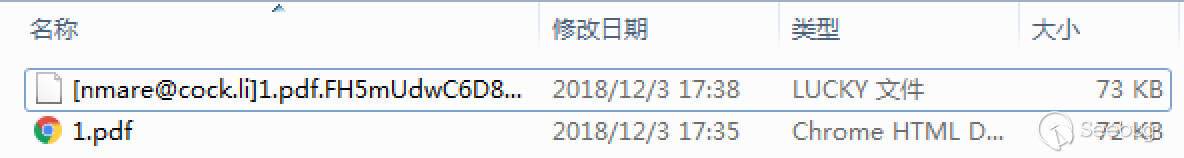
0x04 Key Restore
Before discussing the key restoration, let's take a look at the process after user's payment.
As a victim, if you want to decrypt the file, you have to pay 1BTC to the attacker, and submit the AES key packaged by the RSA algorithm to the attacker. The attacker decrypts with the private key and finally returns the plaintext AES key to be used for file decryption. Unfortunately, the victim can not decrypt it even if he gets the key. The lucky ransomware does not provide decryption modules.
The decryption process expected by the ransomware:
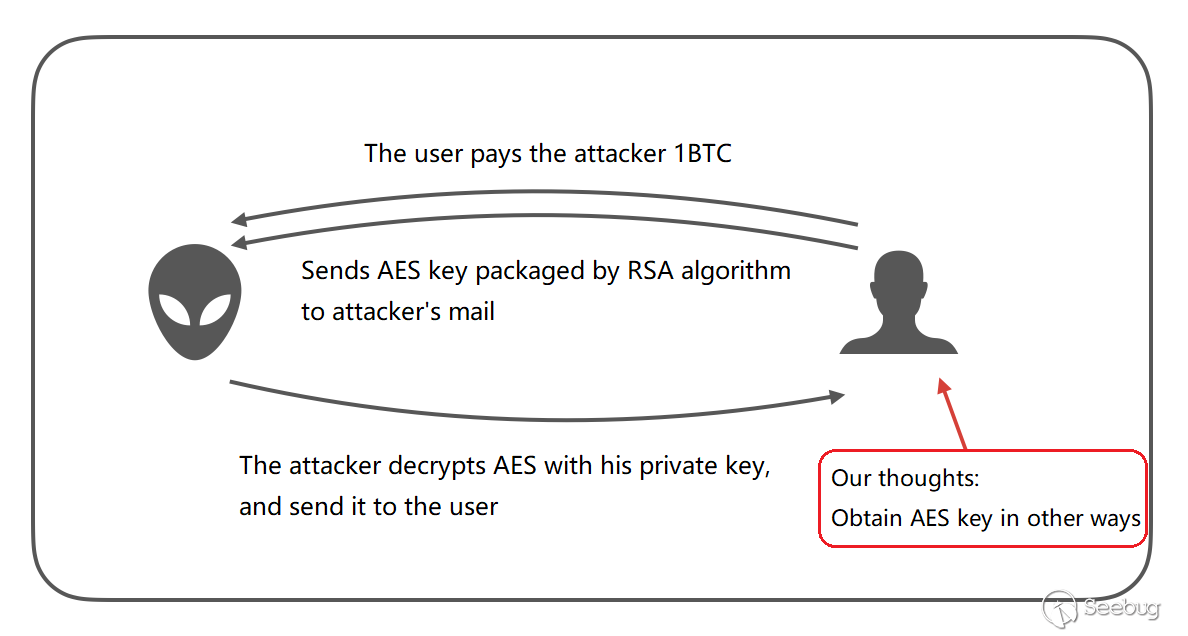
What if you can find the AES key directly?
After a complete analysis of the encryption process, some you may have discovered that the AES key is generated by the generate_key() function. Let's review the function:

The current timestamp is used as the seed of the random number, and the random number is used to select characters from the preset string sequence to form a 60-byte key.
Random number=>pseudo-random number
Programmers should know that there are no real random numbers. All random numbers are pseudo-random numbers, and the characteristics of pseudo-random numbers are "for an algorithm, if the initial value (seed) used is not changed, then the order of the pseudo-random number is also unchanged." Therefore, if you can determine the timestamp of the generate_key() function, you can use the timestamp as a random seed to reproduce the key generation process and obtain the key.
Determining timestamp
Blasting
Of course, the most violent way is to directly blast in seconds, with a marked file (such as a PDF file header) as a reference, constantly guessing the possible keys, if the decrypted file header contains %PDF (PDF header), then the key is correct.
File Modification Time
Is there any other way? The file is rewritten to the file after it is encrypted, so from the operating system perspective, the encrypted file has an exact modification time that can be used to determine the key generation timestamp:
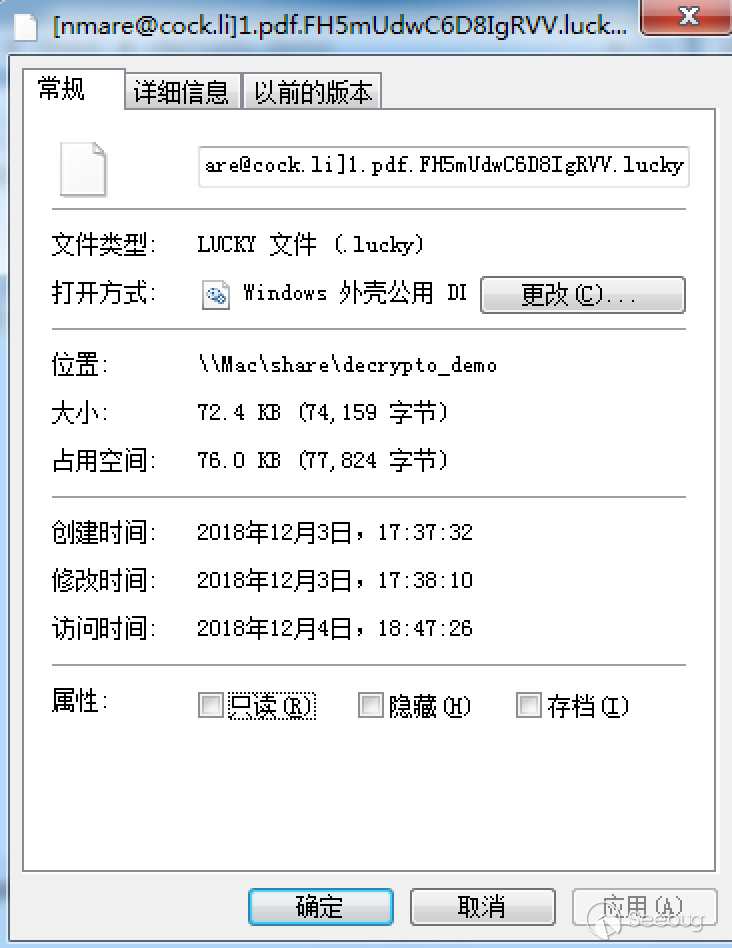
If there are more files to be encrypted, then the time the encrypted file is modified is not the time the key is generated. It should be moved forward. But this also greatly narrow down the list of guessing.
Using User Session
The use of file modification time greatly reduces the scope of guessing. In actual tests, it is found that the process of encrypting files takes a very long time, resulting in too much difference between file modification time and key generation time. Then you need to check whether the key is correct, which takes a lot of time. You can use the user session to further narrow down the list of guessing.
Looking back at the encryption process, we can find that the user session is generated by using the time random number, and that is what we can make use of. Use a timestamp to generate a random number and then use this number to generate a possible user session. When a session is found to be the same as the currently encrypted user session, it means that the generate_session() function is called at that moment. The function is called earlier than file encryption, later than the key generation function.
After the timestamp of the generated user session is found, take this time as the starting point, and the time stamp for generating the key can be found.
Supplement: In fact, it is to convert the process of restoring the entire key into finding a timestamp; if the timestamp is correct, try to use a file with a flag, such as the PDF file header %PDF as a plain text comparison.
Restore Key
The timestamp is found by the above method, and then we can restore the key with the timestamp. The pseudo code is as follows:
Sequence = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789"Key = []
Timestamp = 1542511041
Srand(timestamp)
For (i = 0; i < 60; i++) {
Key[i] = sequence[rand() % 0x3E]
}
File decryption
Get the AES key and decrypt the file with the AES_ECB algorithm.
Pay attention to two points:
1. Before decryption, remove the content at the end of the file (key content packaged by the RSA algorithm) 2. Do different decryption processing for file size.
0x05 Summary
The ransomware is still looting, and users should be wary of it. Although the lucky ransomware has a loophole during the encryption process, but we should not let this happen. Since the lucky ransomware spreds by exploiting the vulnerability of multiple applications, every operation and maintenance personnel should patch the application in time.
In addition, Knownsec 404 Team has converted the file decryption method mentioned in the article into a tool. If you are unfortunately affected by the lucky ransomware in this incident, you can contact us at any time.
References:
Tencent: https://s.tencent.com/research/report/571.html
Nsfocus: https://mp.weixin.qq.com/s/uwWTS_ta29YlYntaZN3omQ
Sangfor: https://mp.weixin.qq.com/s/zA1bK1sLwaZsUvuOzVHBKg
The Python decryption script: https://github.com/knownsec/Decrypt-ransomware
About Knownsec & 404 Team
Beijing Knownsec Information Technology Co., Ltd. was established by a group of high-profile international security experts. It has over a hundred frontier security talents nationwide as the core security research team to provide long-term internationally advanced network security solutions for the government and enterprises.
Knownsec's specialties include network attack and defense integrated technologies and product R&D under new situations. It provides visualization solutions that meet the world-class security technology standards and enhances the security monitoring, alarm and defense abilities of customer networks with its industry-leading capabilities in cloud computing and big data processing. The company's technical strength is spanly recognized by the State Ministry of Public Security, the Central Government Procurement Center, the Ministry of Industry and Information Technology (MIIT), China National Vulnerability Database of Information Security (CNNVD), the Central Bank, the Hong Kong Jockey Club, Microsoft, Zhejiang Satellite TV and other well-known clients.
404 Team, the core security team of Knownsec, is dedicated to the research of security vulnerability and offensive and defensive technology in the fields of Web, IoT, industrial control, blockchain, etc. 404 team has submitted vulnerability research to many well-known vendors such as Microsoft, Apple, Adobe, Tencent, Alibaba, Baidu, etc. And has received a high reputation in the industry.
The most well-known sharing of Knownsec 404 Team includes: KCon Hacking Conference, Seebug Vulnerability Database and ZoomEye Cyberspace Search Engine.
以上是 Lucky Ransomware Analysis and File Decryption 的全部内容, 来源链接: utcz.com/p/199382.html