Zoomeye Cyberspace Mapping——Impact of 2019 Venezuelan Blackouts on Its Network Critical Infrastructure and Important Information Systems
Author: Knownsec 404 Team
ZoomEye Topic: https://www.zoomeye.org/topic?id=ZoomEye-series-report-VE-en
Chinese Version: https://paper.seebug.org/869/
1. Introduction
Venezuela is a tropical country located in the north of South America and the most important oil producing country in South America. According to the 2012 World Energy Statistics Report, Venezuela has proven oil reserves of 296.5 billion barrels, accounting for 18% of the world. Oil exports have also become the main economic pillar of the country.
Due to the influence of various factors such as the country's policies and the international situation, the country's oil production is declining in recent years, and the domestic situation is turbulent. On the evening of March 7th, 2019, a large-scale blackout occurred in Venezuela, and the country was in a dark state.
This paper will analyze and judge the network construction situation and power outage events in the country from the perspective of network space mapping.
2. Venezuela Network Construction
As of March 15th, 2019, ZoomEye has included a total of 3,067,202 banner information for 1,637,553 IP in Venezuela.
2.1 Device Type Statistics
The identified device components account for approximately 2/3 of the country's total equipment components, with the ZTE ZXV10 W300 router's web management interface accounting for approximately 1/10 of the total device components.
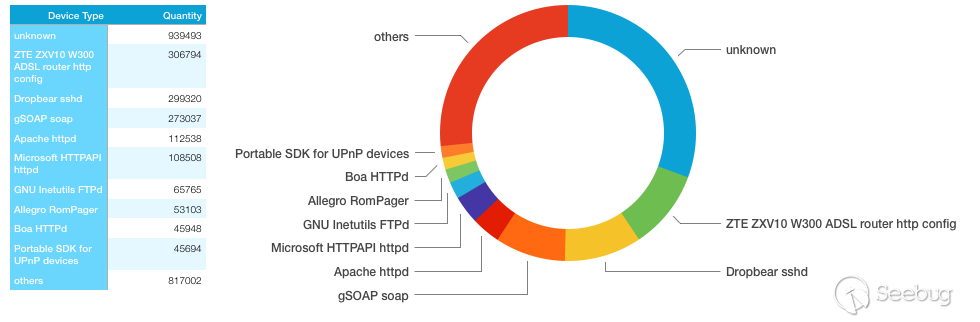
It is worth mentioning that a total of 306,444 ZTE ZXV10 W300 routers and 299,250 Dropbear sshd services are identified, and the IP addresses of the ZTE ZXV10 W300 router which has a Dropbear sshd service are up to 244,111.
Therefore, a judgment can be made that the router may be widely used as a home router. This means that once the vulnerable router is attacked, it can lead to a wide range of home networks paralysis in Venezuela.
2.2 Open Port Statistics
The port distribution is as follows:
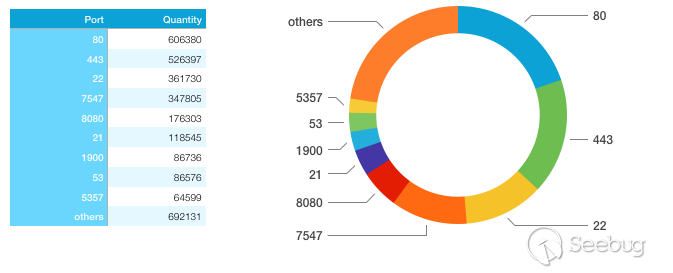
According to the known conclusions of 2.1, the banners which have been identified in the country mainly belong to the ZTE ZXV10 W300 router. The 80, 443, 22, and 7547 ports account for a relatively high proportion of the router.
It is worth noting that port 5357 appears in the tenth place, of which 62139 banners are recognized as Microsoft-HTTPAPI/2.0. After judging, these IPs belong to Movilnet. According to its official website, Movilnet is a subsidiary of Venezuela's state-owned telephone and Internet service provider CANTV.
2.3 ISP Statistics
According to the ISP (Internet Service Provider) statistics, the results are as follows:
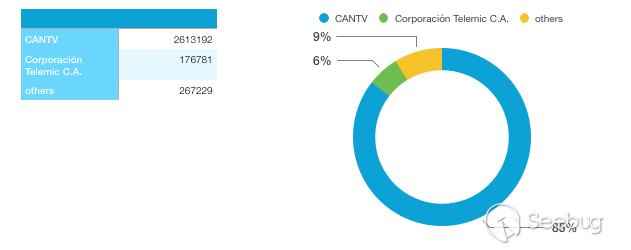
CANTV, Venezuela's state-owned telephone and Internet service provider, has an absolute advantage, with 85% of IP owned by the company.
Note: CANTV is a national telephone and Internet service provider, which is the largest telecommunications provider in Venezuela. After privatization in 1991, it was re-nationalized in 2007. Concerned about the routers belonging to this ISP, most of them are ZTE ZXV10 W300, and a few of them are other brands, such as D-Link, TP-Link, etc. Some routers may have vulnerabilities. (such as the D-Link DIR series, their routers have a large number of security vulnerabilities in history. There are three D-Link DIR series routers belonging to this ISP.)
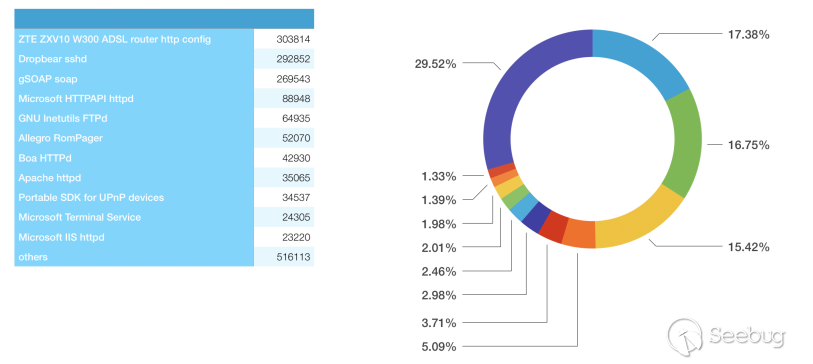
Statistics of the Identified Components Belonging to CANTV
The second-ranked Corporación Telemic C.A. is a Venezuelan television broadcaster and telecommunications provider. Compared to the components of CANTV, there are not a large number of civilian routers belonging to this ISP, instead, there are 11,219 components identified as Microsoft HTTPAPI httpd. It has been verified that these IP addresses are used by the real Windows systems.
2.4 HTTPS Certificate Statistics
The ZoomEye cyberspace search engine identified a total of 252,144 HTTPS certificate information. After removing the certificate information such as the router's certificate and self-signed certificate, a total of 645 domain names information was extracted. The types of the domain names are as follows:
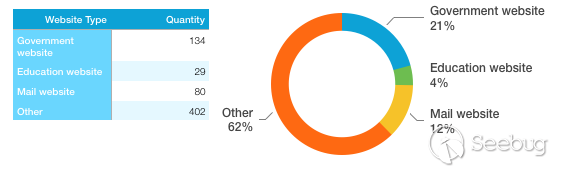
Government and educational websites make up a quarter of the total number of websites. Mail-based websites account for 12%, and other types of websites account for only 62%. From the perspective of HTTPS certificates, the country's Internet development is relatively backward, and government/educational websites are still the main force for Internet development in the country.
2.5 Security Response Capability
After the leak of the EternalBlue in 2017, the ability to quickly fix the vulnerability also reflect the security response capability.
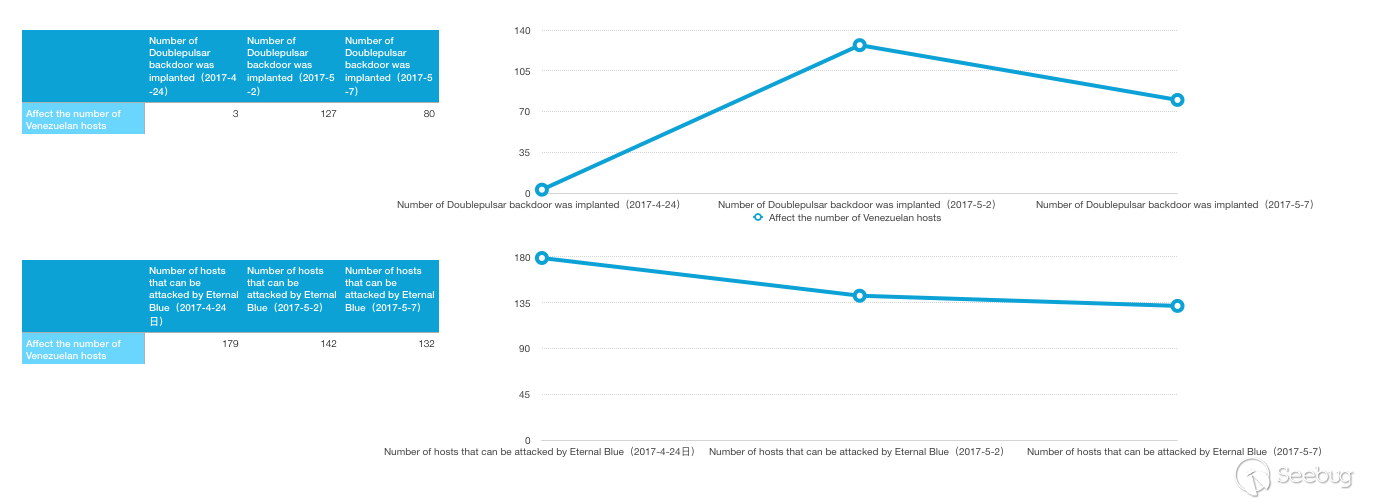
It can be seen that on April 24th, 2017, when the vulnerability just broke out, only three hosts were implanted in the backdoor of Doublepulsar. This also reflects from the side that the country is not the main target of cyber warfare. But three weeks after the vulnerability has broken out, there are still 132 hosts with vulnerabilities in the country, only 47 fewer than the original 179, which also reflects the country's lack of security response capabilities.
2.6 Oil Sales Channels
During the understanding of the country's background, it can be known that the country mainly relies on oil exports. But after searching the existing banner, we only found one company related to oil production (http://200.*.*.*) and one company that exports all kinds of items (including oil) (http:/ /201.*.*.*).
It also reflects that the country’s oil exports have fixed distribution channels, confirming the fact that oil exploitation is controlled by state-owned enterprises.
2.7 Distribution of ICS Ports
According to the data of the ZoomEye cyberspace search engine, a small number of industrial control system devices in Venezuela was exposed to the public network. Known industrial control system devices or industrial control protocols (active in the past year) are as follows:
| ICS devices/protocols | Quantity |
| Siemens S7 PLC Device | 1 |
| Modbus | 6 |
| BACnet | 1 |
| Crimson V3 | 1 |
| OMRON FINS | 1 |
3. Impact of Power Outages
The ZoomEye cyberspace search engine has a certain periodicity and regularity for external detection.
According to the above, we know that there is a large proportion of home routers on the Venezuelan public network.
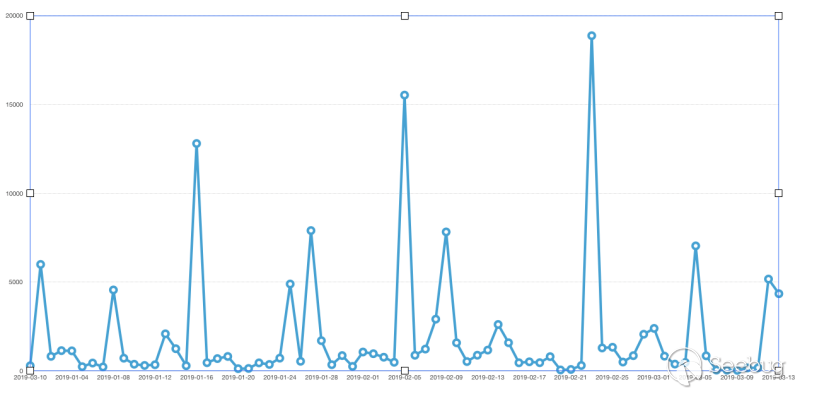
The above picture shows the number of banners that ZoomEye daily imported in Venezuela. In early March, there were significant data changes. We believe this has a span correlation with the blackout in Venezuela.
The specific data for March is as follows:
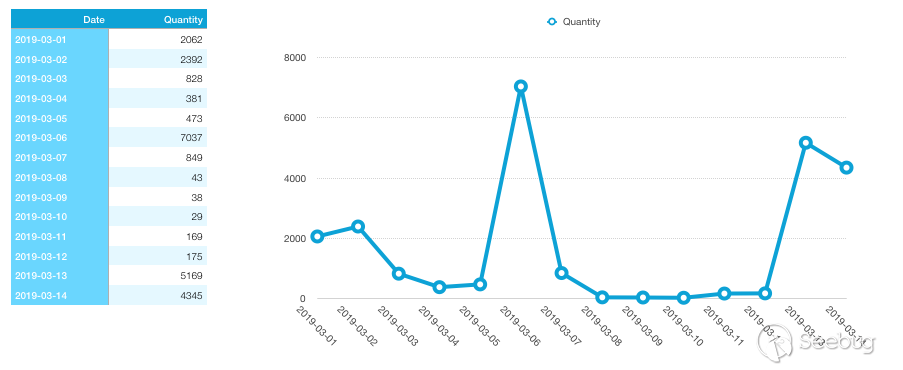
It can be seen that since March 8th, the number of ZoomEye recorded banners has plummeted, and it has rebounded on March 11th, then returned to normal levels on March 13. This is basically consistent with the known Venezuelan blackout event (the power outage began on the evening of March 7th). This also shows from another level that since March 13th, 2019, the power supply in Venezuela has been normal.
During the large-scale power outage in Venezuela, the banner data included by the ZoomEye cyberspace search engine from March 9th to March 12th, shows that there are still some devices that can connect to network in these areas:
| Area | Number of entries during power outage |
| Capital(Caracas, capital of Venezuela) | 250 |
| Carabobo(Vara Vivo, Venezuela) | 66 |
| Mérida(Merida, Venezuela) | 52 |
| Unknown area | 16 |
| Anzoátegui | 14 |
| Miranda | 13 |
| Aragua | 9 |
| Zulia | 8 |
| Táchira | 6 |
| Lara | 6 |
| Vargas | 5 |
| Portuguesa | 2 |
| Guárico | 2 |
| Falcón | 2 |
| Bolívar | 1 |
| Barinas | 1 |
| Amazonas | 1 |
During the large-scale blackouts in the country, Caracas, the capital of Venezuela, and the state of Carabobo near the capital (the state has its own power plant) and Merida in the west still have electricity.
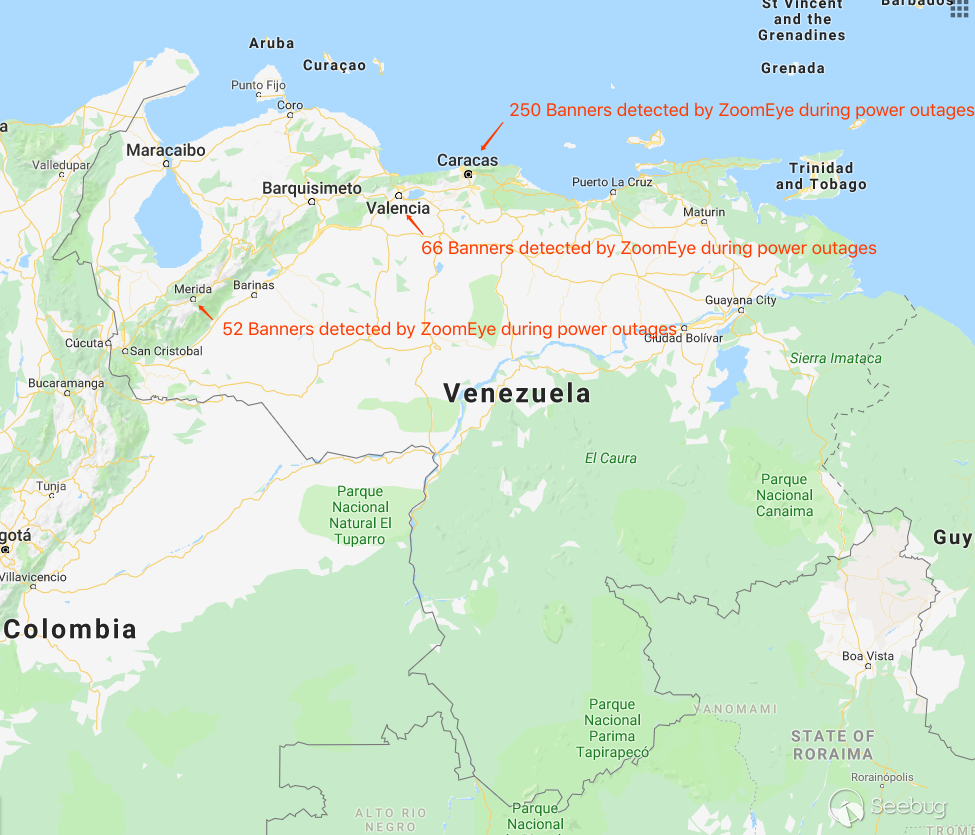
Note: The ZoomEye cyberspace search engine uses the IP database provided by GeoIP to obtain geographic information corresponding to the IP address. In theory, IP location information can be accurate to the city level.
The components identified during the power outage include routers, cameras, Windows systems, and so on. But the router type ZTE ZXV10 W300, which is commonly used, does not appear. It can be seen that during the large-scale power outages nationwide, limited power is only used for the normal operation of the national machine.
4. Conclusion
Regarding the blackout event, it cannot be proved from the perspective of cyberspace mapping that the power outage is caused by cyber attacks before there is actual and span evidence.
This article explores the development of the Internet in Venezuela and the recovery of power outages from the perspective of ZoomEye's cyberspace search engine. The main conclusions are as follows:
The country’s Internet construction is relatively backward.
The power outage in the country resumed on March 13th, 2019 (the sixth day after the power outage).
If there is a cyber attack behind the power outage, many ZTE routers exposed on the public network and related hosts of Movilnet may become the potential target.
Network security construction is not a one-step process, and Venezuela has a long way to go in this regard.
About ZoomEye
ZoomEye is a well-known Cyberspace Search Engine recording information of devices, websites, services and components etc. It was developed by knownsec 404 team and first released in 2013.
Explore now: https://www.zoomeye.org/
以上是 Zoomeye Cyberspace Mapping——Impact of 2019 Venezuelan Blackouts on Its Network Critical Infrastructure and Important Information Systems 的全部内容, 来源链接: utcz.com/p/199283.html