高性能计算协作平台之OpenStack网络安全认证Keystone
一、keystone简介
keystone是openstack中的核心服务,它主要作用是实现用户认证和授权以及服务目录;所谓服务目录指所有可用服务的信息库,包含所有可用服务及其API endport路径;简单点讲就是存储各服务的API endport路径和各服务的其他信息;对于openstack的认证服务来讲,有几个核心的术语要了解下;
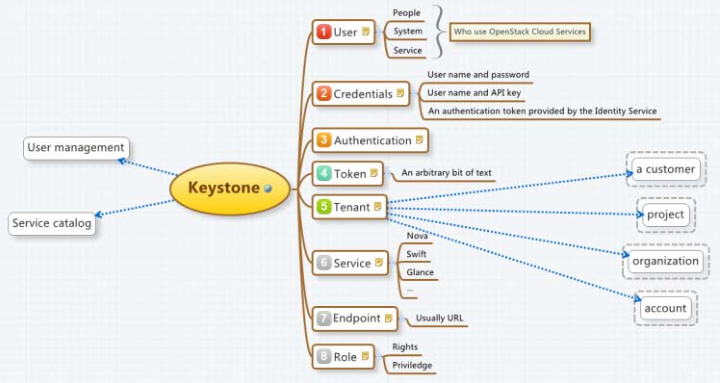
user:这里指使用openstack的用户,一个用户可以以关联多个tenant(租户)
tenant:租户,这里的租户指openstack上的项目project,或者一个组织;通常一个租户对应一个project或一个组织;
role:角色,这里的角色类似Linux用户里的用户组概念,拥有授权为一个用户为一个角色,那么这个用户就拥有这个角色所对应的权限;
token:令牌,用于认证和授权;这是另一种认证的方式;在openstack中各服务之间通过令牌来做认证的;
service:服务,这个和我们理解的服务一样,没有特别的不一样;
endport:服务端点,通常指服务访问入口;
上述这些术语对应的数据,通常会用一个数据库来存储,我们把这个数据库统称为driver,对于不同类型的数据我们可以选择不同的driver来存储;比如对于token我们可以选择存储到k/v键值存储系统中,也可以选择存储在memcached中或者mysql中;catalog我们可以选择存储在k/v键值存储系统中,也可选择存储到mysql中,也可以选择存储到一个模板中;identity我们可以存储k/v键值存储系统中,也可选择存储到mysql中或者pam中也可以;
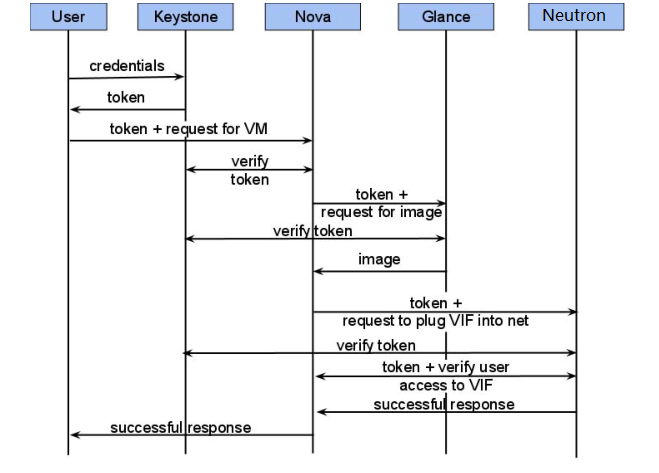
提示:上图是一个用户在openstack上创建一个虚拟机内部验证的过程;首先用户要登入openstack上要把用户的用户名和密码发送给keystone进行验证,如果在keystone中验证通过后,keystone会给用户返回一个token,此时用户就可以拿着这个返回的token去计算节点请求nova服务,进行创建虚拟机请求,在nova服务接受到用户的请求后,nova它不能直接相信用户的token是否是keystone给的,它会把这个token发送给keystone进行验证,如果keystone验证通过,此时nova才会拿着这个token去请求glance进行虚拟机镜像请求,同样的glance也不相信nova拿到这个token,它会去找keystone验证,只有keystone通过后,glance才会把镜像发送给nova,nova拿到镜像启动虚拟机;启动虚拟机过程中nova还会拿着用户的token去请求neutron服务给虚拟机分配网络,同样neutron也是不相信nova的token,它也会去keystone上验证token,只有验证通过后才给nova创建的虚拟机分配网络;最后nova启动好虚拟以后在返回,告诉用户虚拟机启动成功;从上面的过程来看,几乎所有服务都会去keystone上验证用户的token,所以keystone服务会非常繁忙;
二、keystone服务安装、配置、测试
1、创建数据库
[root@node02 ~]# mysqlWelcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 2
Server version: 10.1.20-MariaDB MariaDB Server
Copyright (c) 2000, 2016, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> CREATE DATABASE keystone;
Query OK, 1 row affected (0.00 sec)
MariaDB [(none)]> SHOW DATABASES;
+--------------------+
| Database |
+--------------------+
| information_schema |
| keystone |
| mysql |
| performance_schema |
| test |
+--------------------+
5 rows in set (0.04 sec)
MariaDB [(none)]>
2、创建keystone用户并授权允许从任何主机连接数据库
MariaDB [(none)]> GRANT ALL PRIVILEGES ON keystone.* TO 'keystone'@'%' IDENTIFIED BY 'keystone123';Query OK, 0 rows affected (0.00 sec)
MariaDB [(none)]> flush privileges;
Query OK, 0 rows affected (0.00 sec)
MariaDB [(none)]>
验证:在node01上使用keystone用户连接数据库,看看是否能够正常连接?
[root@node01 ~]# mysql -ukeystone -pkeystone123 -hnode02Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 4
Server version: 10.1.20-MariaDB MariaDB Server
Copyright (c) 2000, 2016, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| keystone |
| test |
+--------------------+
3 rows in set (0.00 sec)
MariaDB [(none)]>
提示:能够从别的主机用keystone账号连接到mysql,并看到我们刚才创建的数据库,说明我们创建的keystone账号没有问题;
3、在控制节点安装openstack-keystone、httpd和mod_wsgi
[root@node01 ~]# yum install -y openstack-keystone httpd mod_wsgiLoaded plugins: fastestmirror
Loading mirror speeds from cached hostfile
* base: mirrors.aliyun.com
* centos-qemu-ev: mirrors.aliyun.com
* extras: mirrors.aliyun.com
* updates: mirrors.aliyun.com
Resolving Dependencies
--> Running transaction check
---> Package httpd.x86_64 0:2.4.6-93.el7.centos will be installed
--> Processing Dependency: httpd-tools = 2.4.6-93.el7.centos for package: httpd-2.4.6-93.el7.centos.x86_64
--> Processing Dependency: /etc/mime.types for package: httpd-2.4.6-93.el7.centos.x86_64
--> Processing Dependency: libaprutil-1.so.0()(64bit) for package: httpd-2.4.6-93.el7.centos.x86_64
--> Processing Dependency: libapr-1.so.0()(64bit) for package: httpd-2.4.6-93.el7.centos.x86_64
---> Package mod_wsgi.x86_64 0:3.4-18.el7 will be installed
……省略部分内容……
Dependency Installed:
MySQL-python.x86_64 0:1.2.5-1.el7 apr.x86_64 0:1.4.8-5.el7
apr-util.x86_64 0:1.5.2-6.el7 httpd-tools.x86_64 0:2.4.6-93.el7.centos
mailcap.noarch 0:2.1.41-2.el7 python-aniso8601.noarch 0:0.82-3.el7
python-beaker.noarch 0:1.5.4-10.el7 python-editor.noarch 0:0.4-4.el7
python-jwcrypto.noarch 0:0.4.2-1.el7 python-keystone.noarch 1:14.2.0-1.el7
python-mako.noarch 0:0.8.1-2.el7 python-migrate.noarch 0:0.11.0-1.el7
python-oslo-cache-lang.noarch 0:1.30.4-1.el7 python-oslo-concurrency-lang.noarch 0:3.27.0-1.el7
python-oslo-db-lang.noarch 0:4.40.2-1.el7 python-oslo-middleware-lang.noarch 0:3.36.0-1.el7
python-oslo-policy-lang.noarch 0:1.38.1-1.el7 python-paste.noarch 0:1.7.5.1-9.20111221hg1498.el7
python-paste-deploy.noarch 0:1.5.2-6.el7 python-pycadf-common.noarch 0:2.8.0-1.el7
python-routes.noarch 0:2.4.1-1.el7 python-sqlparse.noarch 0:0.1.18-5.el7
python-tempita.noarch 0:0.5.1-8.el7 python2-alembic.noarch 0:0.9.7-1.el7
python2-amqp.noarch 0:2.4.0-1.el7 python2-bcrypt.x86_64 0:3.1.6-2.el7
python2-cachetools.noarch 0:2.1.0-1.el7 python2-click.noarch 0:6.7-8.el7
python2-defusedxml.noarch 0:0.5.0-2.el7 python2-eventlet.noarch 0:0.20.1-6.el7
python2-fasteners.noarch 0:0.14.1-6.el7 python2-flask.noarch 1:1.0.2-1.el7
python2-flask-restful.noarch 0:0.3.6-7.el7 python2-future.noarch 0:0.18.2-2.el7
python2-futurist.noarch 0:1.7.0-1.el7 python2-greenlet.x86_64 0:0.4.12-1.el7
python2-itsdangerous.noarch 0:0.24-14.el7 python2-jinja2.noarch 0:2.10-2.el7
python2-keystonemiddleware.noarch 0:5.2.2-1.el7 python2-kombu.noarch 1:4.2.2-1.el7
python2-ldap.x86_64 0:3.1.0-1.el7 python2-ldappool.noarch 0:2.3.1-1.el7
python2-markupsafe.x86_64 0:0.23-16.el7 python2-oauthlib.noarch 0:2.0.1-8.el7
python2-oslo-cache.noarch 0:1.30.4-1.el7 python2-oslo-concurrency.noarch 0:3.27.0-1.el7
python2-oslo-db.noarch 0:4.40.2-1.el7 python2-oslo-messaging.noarch 0:8.1.4-1.el7
python2-oslo-middleware.noarch 0:3.36.0-1.el7 python2-oslo-policy.noarch 0:1.38.1-1.el7
python2-oslo-service.noarch 0:1.31.8-1.el7 python2-osprofiler.noarch 0:2.3.1-1.el7
python2-passlib.noarch 0:1.7.1-1.el7 python2-pyasn1.noarch 0:0.3.7-6.el7
python2-pyasn1-modules.noarch 0:0.3.7-6.el7 python2-pycadf.noarch 0:2.8.0-1.el7
python2-pyngus.noarch 0:2.3.0-1.el7 python2-pysaml2.noarch 0:4.5.0-4.el7
python2-qpid-proton.x86_64 0:0.32.0-2.el7 python2-scrypt.x86_64 0:0.8.0-2.el7
python2-sqlalchemy.x86_64 0:1.2.7-1.el7 python2-statsd.noarch 0:3.2.1-5.el7
python2-tenacity.noarch 0:4.12.0-1.el7 python2-vine.noarch 0:1.2.0-1.el7
python2-webob.noarch 0:1.8.2-1.el7 python2-werkzeug.noarch 0:0.14.1-3.el7
qpid-proton-c.x86_64 0:0.32.0-2.el7
Complete!
[root@node01 ~]#
4、生成token
[root@node01 ~]# openssl rand -hex 10752e7981c9f3bb1b1a91
[root@node01 ~]#
5、编辑keystone配置文件/etc/keystone/keystone.conf,在default配置段里添加admin_token,把我们生成的token配置上;
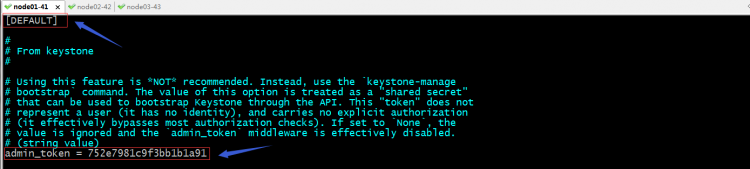
在database配置段配置连接数据库的地址;
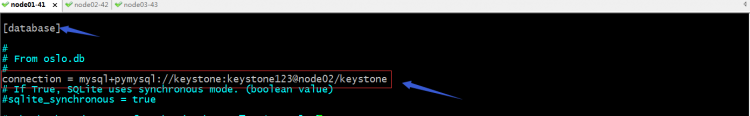
提示:连接数据库前边的mysql+pymysql://这一段不用变,默认格式就是这个,双斜线后面的是keystone用户,冒号后面是对应keystone用户的密码;@后面是数据库服务器地址;斜线后面是指连接那个数据库;我这里是因为配置了主机名解析,所以数据库服务器我用主机名代替了;
在token配置段配置provider = fernet
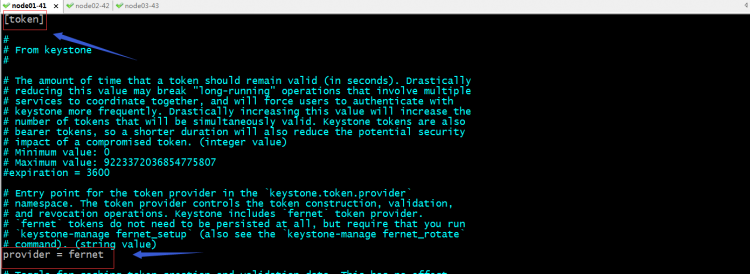
keystone的最终配置
[root@node01 ~]# grep "^[a-Z\[]" /etc/keystone/keystone.conf[DEFAULT]
admin_token = 752e7981c9f3bb1b1a91
[application_credential]
[assignment]
[auth]
[cache]
[catalog]
[cors]
[credential]
[database]
connection = mysql+pymysql://keystone:keystone123@node02/keystone
[domain_config]
[endpoint_filter]
[endpoint_policy]
[eventlet_server]
[federation]
[fernet_tokens]
[healthcheck]
[identity]
[identity_mapping]
[ldap]
[matchmaker_redis]
[memcache]
[oauth1]
[oslo_messaging_amqp]
[oslo_messaging_kafka]
[oslo_messaging_notifications]
[oslo_messaging_rabbit]
[oslo_messaging_zmq]
[oslo_middleware]
[oslo_policy]
[policy]
[profiler]
[resource]
[revoke]
[role]
[saml]
[security_compliance]
[shadow_users]
[signing]
[token]
provider = fernet
[tokenless_auth]
[trust]
[unified_limit]
[wsgi]
[root@node01 ~]#
提示:这个配置文件是ini风格的配置文件,里面有很多配置段,其实生效的就只有我们刚才配置的三段;
6、在控制节点初始化keystone数据库
[root@node01 ~]# su -s /bin/sh -c "keystone-manage db_sync" keystone[root@node01 ~]#
提示:以上命令会通过我们刚才配置的连接数据库的地址,通过keystone连接到数据库中创建一堆表;
验证:在node02上验证,看看keystone库中是否多了很多表?
MariaDB [(none)]> use keystoneReading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [keystone]> show tables;
+-----------------------------+
| Tables_in_keystone |
+-----------------------------+
| access_token |
| application_credential |
| application_credential_role |
| assignment |
| config_register |
| consumer |
| credential |
| endpoint |
| endpoint_group |
| federated_user |
| federation_protocol |
| group |
| id_mapping |
| identity_provider |
| idp_remote_ids |
| implied_role |
| limit |
| local_user |
| mapping |
| migrate_version |
| nonlocal_user |
| password |
| policy |
| policy_association |
| project |
| project_endpoint |
| project_endpoint_group |
| project_tag |
| region |
| registered_limit |
| request_token |
| revocation_event |
| role |
| sensitive_config |
| service |
| service_provider |
| system_assignment |
| token |
| trust |
| trust_role |
| user |
| user_group_membership |
| user_option |
| whitelisted_config |
+-----------------------------+
44 rows in set (0.00 sec)
MariaDB [keystone]>
7、在控制节点上初始化Fernet密钥
[root@node01 ~]# keystone-manage fernet_setup --keystone-user keystone --keystone-group keystone[root@node01 ~]# keystone-manage credential_setup --keystone-user keystone --keystone-group keystone
[root@node01 ~]#
提示:以上命令会在/etc/keystone/fernet-keys/目录下生成两个key文件;
验证:查看/etc/keystone/fernet-keys/目录下是否有两个key生成?
[root@node01 ~]# ll /etc/keystone/fernet-keys/total 8
-rw------- 1 keystone keystone 44 Oct 28 19:23 0
-rw------- 1 keystone keystone 44 Oct 28 19:23 1
[root@node01 ~]#
8、配置httpd代理keystone
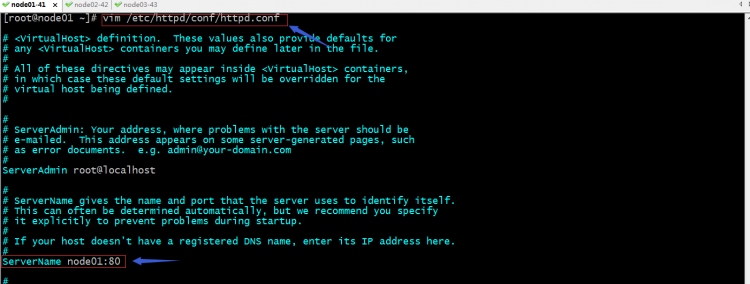
提示:以上主要修改了httpd的servername监听地址,其实这里不修改也行,不影响;重要的是下面的配置;
把/usr/share/keystone/wsgi-keystone.conf连接至/etc/httpd/conf.d/下
[root@node01 ~]# ln -sv /usr/share/keystone/wsgi-keystone.conf /etc/httpd/conf.d/‘/etc/httpd/conf.d/wsgi-keystone.conf’ -> ‘/usr/share/keystone/wsgi-keystone.conf’
[root@node01 ~]# ll /etc/httpd/conf.d/
total 16
-rw-r--r-- 1 root root 2926 Apr 2 2020 autoindex.conf
-rw-r--r-- 1 root root 366 Apr 2 2020 README
-rw-r--r-- 1 root root 1252 Nov 27 2019 userdir.conf
-rw-r--r-- 1 root root 824 Nov 27 2019 welcome.conf
lrwxrwxrwx 1 root root 38 Oct 28 19:30 wsgi-keystone.conf -> /usr/share/keystone/wsgi-keystone.conf
[root@node01 ~]#
提示:以上操作就是把httpd代理keystone的配置导入到httpd中,默认安装keystone以后就会有一个这样的配置文件;我们只需要把这个配置文件软连接到httpd的配置目录下即可;
启动httpd,并设置为开机启动
[root@node01 ~]# systemctl start httpd[root@node01 ~]# systemctl enable httpd
Created symlink from /etc/systemd/system/multi-user.target.wants/httpd.service to /usr/lib/systemd/system/httpd.service.
[root@node01 ~]# ss -tnl
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 128 *:22 *:*
LISTEN 0 100 127.0.0.1:25 *:*
LISTEN 0 128 :::80 :::*
LISTEN 0 128 :::22 :::*
LISTEN 0 100 ::1:25 :::*
LISTEN 0 128 :::5000 :::*
[root@node01 ~]#
提示:如果能够看到5000端口正常监听,说明我们导入的配置没有问题;
9、通过OS_TOKEN环境变量导出admin的token,使用OS_URL环境变量导出控制节点api接口地址,使用OS_IDENTITY_API_VERSION环境变量导出api的版本号
[root@node01 ~]# export OS_TOKEN=752e7981c9f3bb1b1a91[root@node01 ~]# export OS_URL=http://node01:5000/v3
[root@node01 ~]# export OS_IDENTITY_API_VERSION=3
提示:这里的admin_token就是我们刚才在配置文件中配置的token;因为最开始我们只有手动生成一个token进行验证;
10、在导出以上三个环境变量的终端上创建域、用户、项目、角色、服务;
创建default域
[root@node01 ~]# openstack domain create --description "Default Domain" default+-------------+----------------------------------+
| Field | Value |
+-------------+----------------------------------+
| description | Default Domain |
| enabled | True |
| id | 47c0915c914c49bb8670703e4315a80f |
| name | default |
| tags | [] |
+-------------+----------------------------------+
[root@node01 ~]#
创建一个admin的项目 并把域指向default
[root@node01 ~]# openstack project create --domain default --description "Admin Project" admin+-------------+----------------------------------+
| Field | Value |
+-------------+----------------------------------+
| description | Admin Project |
| domain_id | 47c0915c914c49bb8670703e4315a80f |
| enabled | True |
| id | b4e56eeb160948c581e98d685133d19a |
| is_domain | False |
| name | admin |
| parent_id | 47c0915c914c49bb8670703e4315a80f |
| tags | [] |
+-------------+----------------------------------+
[root@node01 ~]#
创建admin用户并设置密码为admin
[root@node01 ~]# openstack user create --domain default --password-prompt adminUser Password:
Repeat User Password:
+---------------------+----------------------------------+
| Field | Value |
+---------------------+----------------------------------+
| domain_id | 47c0915c914c49bb8670703e4315a80f |
| enabled | True |
| id | a105f256dc9f42438212e9d96d46b60d |
| name | admin |
| options | {} |
| password_expires_at | None |
+---------------------+----------------------------------+
[root@node01 ~]#
创建admin角色
[root@node01 ~]# openstack role create admin+-----------+----------------------------------+
| Field | Value |
+-----------+----------------------------------+
| domain_id | None |
| id | 7f1f7aa119034c2fbd15b46b90632d18 |
| name | admin |
+-----------+----------------------------------+
[root@node01 ~]#
给admin用户授权,将admin用户授予admin项目的admin角色
[root@node01 ~]# openstack role add --project admin --user admin admin[root@node01 ~]#
创建一个用于测试的demo项目
[root@node01 ~]# openstack project create --domain default --description "Demo Project" demo+-------------+----------------------------------+
| Field | Value |
+-------------+----------------------------------+
| description | Demo Project |
| domain_id | 47c0915c914c49bb8670703e4315a80f |
| enabled | True |
| id | 1a918887f38a42c28f9d0d3774f34b16 |
| is_domain | False |
| name | demo |
| parent_id | 47c0915c914c49bb8670703e4315a80f |
| tags | [] |
+-------------+----------------------------------+
[root@node01 ~]#
创建demo用户并设置密码为demo
[root@node01 ~]# openstack user create --domain default --password-prompt demoUser Password:
Repeat User Password:
+---------------------+----------------------------------+
| Field | Value |
+---------------------+----------------------------------+
| domain_id | 47c0915c914c49bb8670703e4315a80f |
| enabled | True |
| id | 5453d68782a34429a7dab7da9c51f0d9 |
| name | demo |
| options | {} |
| password_expires_at | None |
+---------------------+----------------------------------+
[root@node01 ~]#
创建一个user角色
[root@node01 ~]# openstack role create user+-----------+----------------------------------+
| Field | Value |
+-----------+----------------------------------+
| domain_id | None |
| id | ee2f38096e42409eb47ae67a8c289279 |
| name | user |
+-----------+----------------------------------+
[root@node01 ~]#
把demo用户添加到demo项目,然后赋予user角色权限
[root@node01 ~]# openstack role add --project demo --user demo user[root@node01 ~]#
验证:查看现有的用户、项目、角色、域是否是我们创建的
[root@node01 ~]# openstack user list+----------------------------------+-------+
| ID | Name |
+----------------------------------+-------+
| 5453d68782a34429a7dab7da9c51f0d9 | demo |
| a105f256dc9f42438212e9d96d46b60d | admin |
+----------------------------------+-------+
[root@node01 ~]# openstack project list
+----------------------------------+-------+
| ID | Name |
+----------------------------------+-------+
| 1a918887f38a42c28f9d0d3774f34b16 | demo |
| b4e56eeb160948c581e98d685133d19a | admin |
+----------------------------------+-------+
[root@node01 ~]# openstack role list
+----------------------------------+-------+
| ID | Name |
+----------------------------------+-------+
| 7f1f7aa119034c2fbd15b46b90632d18 | admin |
| ee2f38096e42409eb47ae67a8c289279 | user |
+----------------------------------+-------+
[root@node01 ~]# openstack domain list
+----------------------------------+---------+---------+----------------+
| ID | Name | Enabled | Description |
+----------------------------------+---------+---------+----------------+
| 47c0915c914c49bb8670703e4315a80f | default | True | Default Domain |
+----------------------------------+---------+---------+----------------+
[root@node01 ~]#
提示:可以看到当前控制节点上有两个用户,两个项目,两个角色,分别是admin和demo;一个default域;这都是我们刚才创建的;
创建一个service项目,各服务之间与keystone进行访问和认证,service用于给服务创建用户;
[root@node01 ~]# openstack project create --domain default --description "Service Project" service+-------------+----------------------------------+
| Field | Value |
+-------------+----------------------------------+
| description | Service Project |
| domain_id | 47c0915c914c49bb8670703e4315a80f |
| enabled | True |
| id | 9c9d6f24fc23464a810ef97ce199bffa |
| is_domain | False |
| name | service |
| parent_id | 47c0915c914c49bb8670703e4315a80f |
| tags | [] |
+-------------+----------------------------------+
[root@node01 ~]#
创建一个keystone认证服务
[root@node01 ~]# openstack service create --name keystone --description "OpenStack Identity" identity+-------------+----------------------------------+
| Field | Value |
+-------------+----------------------------------+
| description | OpenStack Identity |
| enabled | True |
| id | a32cffed26924a87b21b4e86e00c63b4 |
| name | keystone |
| type | identity |
+-------------+----------------------------------+
[root@node01 ~]#
查看当前服务列表
[root@node01 ~]# openstack service list+----------------------------------+----------+----------+
| ID | Name | Type |
+----------------------------------+----------+----------+
| a32cffed26924a87b21b4e86e00c63b4 | keystone | identity |
+----------------------------------+----------+----------+
[root@node01 ~]#
11、创建endpoint(注册服务)
创建公共端
[root@node01 ~]# openstack endpoint create --region RegionOne identity public http://controller:5000/v3+--------------+----------------------------------+
| Field | Value |
+--------------+----------------------------------+
| enabled | True |
| id | 5293ad18db674ea1b01d8f401cb2cf14 |
| interface | public |
| region | RegionOne |
| region_id | RegionOne |
| service_id | a32cffed26924a87b21b4e86e00c63b4 |
| service_name | keystone |
| service_type | identity |
| url | http://controller:5000/v3 |
+--------------+----------------------------------+
[root@node01 ~]#
创建私有端
[root@node01 ~]# openstack endpoint create --region RegionOne identity internal http://controller:5000/v3+--------------+----------------------------------+
| Field | Value |
+--------------+----------------------------------+
| enabled | True |
| id | 6593f8d808094b01a6311828f2ef72bd |
| interface | internal |
| region | RegionOne |
| region_id | RegionOne |
| service_id | a32cffed26924a87b21b4e86e00c63b4 |
| service_name | keystone |
| service_type | identity |
| url | http://controller:5000/v3 |
+--------------+----------------------------------+
[root@node01 ~]#
创建管理端
[root@node01 ~]# openstack endpoint create --region RegionOne identity admin http://controller:5000/v3+--------------+----------------------------------+
| Field | Value |
+--------------+----------------------------------+
| enabled | True |
| id | 3bd05493999b462eb4b4af8d5e5c1fa9 |
| interface | admin |
| region | RegionOne |
| region_id | RegionOne |
| service_id | a32cffed26924a87b21b4e86e00c63b4 |
| service_name | keystone |
| service_type | identity |
| url | http://controller:5000/v3 |
+--------------+----------------------------------+
[root@node01 ~]#
验证:看看endport 列表是否都已经有我们刚才创建的三个端点?
[root@node01 ~]# openstack endpoint list+----------------------------------+-----------+--------------+--------------+---------+-----------+---------------------------+
| ID | Region | Service Name | Service Type | Enabled | Interface | URL |
+----------------------------------+-----------+--------------+--------------+---------+-----------+---------------------------+
| 3bd05493999b462eb4b4af8d5e5c1fa9 | RegionOne | keystone | identity | True | admin | http://controller:5000/v3 |
| 5293ad18db674ea1b01d8f401cb2cf14 | RegionOne | keystone | identity | True | public | http://controller:5000/v3 |
| 6593f8d808094b01a6311828f2ef72bd | RegionOne | keystone | identity | True | internal | http://controller:5000/v3 |
+----------------------------------+-----------+--------------+--------------+---------+-----------+---------------------------+
[root@node01 ~]#
提示:如果创建错误或者多创建了,就需要全部删除,重新注册;
到此keystone服务就配置完了;接下来测试keystone是否可以用来做认证服务
验证:重新打开一个终端窗口,导出OS_IDENTITY_API_VERSION环境变量,使用命令的方式验证admin用户密码是admin
[root@node01 ~]# echo $OS_IDENTITY_API_VERSION[root@node01 ~]# export OS_IDENTITY_API_VERSION=3
[root@node01 ~]# echo $OS_IDENTITY_API_VERSION
3
[root@node01 ~]# openstack --os-auth-url http://node01:5000/v3 --os-project-domain-name default --os-user-domain-name default --os-project-name admin --os-username admin token issue
Password:
+------------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
| Field | Value |
+------------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
| expires | 2020-10-28T13:16:54+0000 |
| id | gAAAAABfmWE2udKuo4ambgxh3RsrzoDwrA8IHa1dx5gYk_sZoU5HmZUM9qHTguwMasYGzRIno0LawlZDbB4i3IJold3sZdAlEZGwiNuPtYJMgP5nikDUR8YrXNPNQNDMjCchDMMN6bWhZ26pQXVEZ0VXcN5v5xOj_bx7nskJ8bnvKWFiRf4ckPQ |
| project_id | b4e56eeb160948c581e98d685133d19a |
| user_id | a105f256dc9f42438212e9d96d46b60d |
+------------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
[root@node01 ~]#
提示:输入正确的密码会返回一个表,记录的有过期时长,id,和项目id和用户id;如果输入密码错误则不会返回这些内容,其实这些内容主要用来描述返回给用户token属性,我们可以理解它就是返回了这样一个token给我们;
[root@node01 ~]# openstack --os-auth-url http://node01:5000/v3 --os-project-domain-name default --os-user-domain-name default --os-project-name admin --os-username admin token issuePassword:
The request you have made requires authentication. (HTTP 401) (Request-ID: req-79d8afbe-56dc-47f9-ab4e-8065a295923e)
[root@node01 ~]#
提示:输入错误的密码它给我们返回了响应码为401,表示验证未通过;
创建admin用户环境变量脚本
[root@node01 ~]# cat admin.sh#!/bin/bash
export OS_PROJECT_DOMAIN_NAME=Default
export OS_USER_DOMAIN_NAME=Default
export OS_PROJECT_NAME=admin
export OS_USERNAME=admin
export OS_PASSWORD=admin
export OS_AUTH_URL=http://controller:5000/v3
export OS_IDENTITY_API_VERSION=3
export OS_IMAGE_API_VERSION=2
[root@node01 ~]# chmod a+x admin.sh
[root@node01 ~]#
创建demo用户环境变量脚本
[root@node01 ~]# cat demo.sh#!/bin/bash
export OS_PROJECT_DOMAIN_NAME=Default
export OS_USER_DOMAIN_NAME=Default
export OS_PROJECT_NAME=demo
export OS_USERNAME=demo
export OS_PASSWORD=demo
export OS_AUTH_URL=http://controller:5000/v3
export OS_IDENTITY_API_VERSION=3
export OS_IMAGE_API_VERSION=2
[root@node01 ~]# chmod a+x demo.sh
[root@node01 ~]#
提示:有了上面两个脚本以后,我们就实现要使用那个用户测试,直接把对应的用户环境变量导出即可;
验证:测试admin用户的环境变量脚本是否可用?
[root@node01 ~]# lltotal 8
-rwxr-xr-x 1 root root 272 Oct 28 20:23 admin.sh
-rwxr-xr-x 1 root root 269 Oct 28 20:24 demo.sh
[root@node01 ~]# source admin.sh
[root@node01 ~]# openstack token issue
+------------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
| Field | Value |
+------------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
| expires | 2020-10-28T13:29:08+0000 |
| id | gAAAAABfmWQU2Z97wzxv94lLY4hcSWe4X6Udp_OyeYw3_wY54_znLFb4TFLcMnR96-ogNAcJEvXiQcJWdvQJHBObYbR-gAEulagQq2sjXLxedMYLUN4j2y_L4G5NhbaogGKtHed4WMR0N72Js4INyHjKWCwwSd2d4NJpZUe14pQjNX8ihleP09g |
| project_id | b4e56eeb160948c581e98d685133d19a |
| user_id | a105f256dc9f42438212e9d96d46b60d |
+------------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
[root@node01 ~]#
提示:重新开一个终端,导出admin用户环境变量,然后直接使用openstack token issue命令就能验证admin用户;有了这个环境变量脚本,我们不用输密码和不用写那么长的命令了;
验证demo用户的环境变量脚本
[root@node01 ~]# lltotal 8
-rwxr-xr-x 1 root root 272 Oct 28 20:23 admin.sh
-rwxr-xr-x 1 root root 269 Oct 28 20:24 demo.sh
[root@node01 ~]# source demo.sh
[root@node01 ~]# openstack token issue
+------------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
| Field | Value |
+------------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
| expires | 2020-10-28T13:31:34+0000 |
| id | gAAAAABfmWSmj5PHp8x3m3szKwZ0_dWSdY-JM-TBbo-bMk4OaTHl3BLNVrglKXRMe5jpbCOBPb5l2AyHWVvzvJdi2Jx4va7PJksJGlx_JluhOx9vry1kjiZoKcW7Ri3Y7qkYFvDcpDHXy0KkYeHSyMW9zjNaFvvJtrPpozgfw7gsghYJNfZoYz0 |
| project_id | 1a918887f38a42c28f9d0d3774f34b16 |
| user_id | 5453d68782a34429a7dab7da9c51f0d9 |
+------------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
[root@node01 ~]#
提示:demo用户的环境变量脚本也都能够正常通过验证;到此keystone服务的安装配置测试就完成了;
以上是 高性能计算协作平台之OpenStack网络安全认证Keystone 的全部内容, 来源链接: utcz.com/a/63609.html