ssh端口转发
假设现在有两台服务器client1,client2,他们直接不能直接相互通信,但是他们均能连接上第三台服务器balance,我们可以在client1,client2和balance三台机器之间建立ssh隧道来让client1和client2实现通信。
ssh端口转发有三种实现方式:本地转发,远程转发,和动态转发。
一. 准备工作
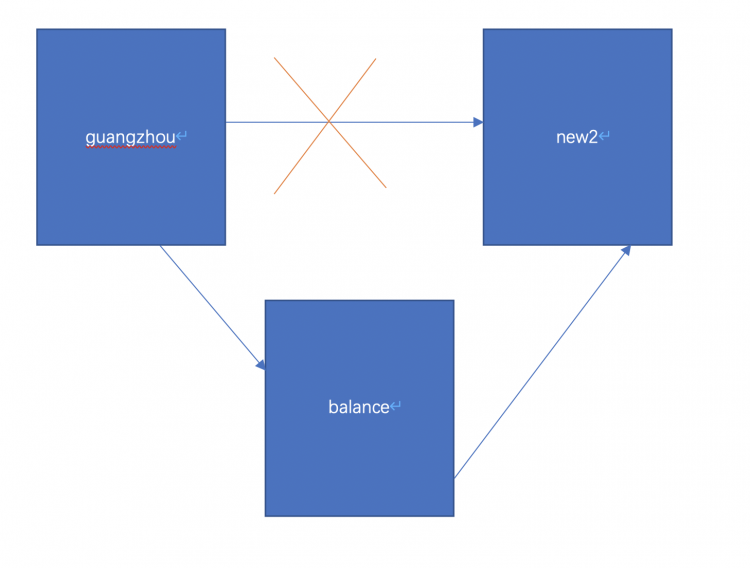
实现目标: guangzhou能访问balance但不能直接访问new2,balance可以访问new2;guangzhou通过balance做端口转发可以间接访问new2。
1.1 服务器IP:
服务器guangzhou: 106.55.241.99
服务器new2: 106.55.171.53
服务器balance: 124.156.143.168
1.2 服务器间通信
服务器guangzhou:
#可访问new2[root@guangzhou
~]# telnet 106.55.171.5322Trying
106.55.171.53...Connected to
106.55.171.53.Escape character is
'^]'.SSH
-2.0-OpenSSH_7.4#可访问balance
[root@guangzhou
~]# telnet 124.156.143.16822Trying
124.156.143.168...Connected to
124.156.143.168.Escape character is
'^]'.SSH
-2.0-OpenSSH_7.4
服务器balance:
#可访问new2
[root@Balance ~]# telnet 106.55.241.9922Trying
106.55.241.99...Connected to
106.55.241.99.Escape character is
'^]'.SSH
-2.0-OpenSSH_7.4
现在上new2防火墙添加禁止guangzhou访问并重启firewalld服务:
[root@new2 ~]# firewall-cmd --permanent --add-rich-rule='rule family=ipv4 source address="106.55.241.99" drop'success
[root@new2
~]# firewall-cmd --reloadsuccess
登陆guangzhou服务器执行命令: telnet 106.55.171.53 22 ,结果无响应,说明防火墙禁止访问设置成功。
目前guangzhou无法直连new2,可连接balance,balance可连接new2.
二. 配置端口转发
2.1 本地转发
命令:-L localport:remotehost:remotehostport sshserver
说明:localport 本机开启的端口号
remotehost 最终连接机器的IP地址
remotehostport 转发机器的端口号
sshserver 转发机器的IP地址
# -L guangzhou-Server-Ip:new2-Server-Ip:new2-Server-Port balance-Server-User@balance-Server-Ip
[root@guangzhou ~]# ssh -L 9001:106.55.171.53:22 root@124.156.143.168root@
124.156.143.168's password:Last failed login: Thu Oct 819:29:00 CST 2020 from 61.135.223.109 on ssh:notty
There were 8 failed login attempts since the last successful login.
Last login: Thu Oct 819:26:382020 from 106.55.241.99
[root@Balance ~]#
新开窗口打开guangzhou服务器:
[root@guangzhou ~]# ssh -p 9001 root@127.0.0.1The authenticity of host
'[127.0.0.1]:9001 ([127.0.0.1]:9001)' can't be established.ECDSA key fingerprint is SHA256:huOuuKbfM9TN6+rpCMjB2Hk0HI4GSF1WCj7gIVyu48I.
ECDSA key fingerprint is MD5:0f:55:88:04:62:82:fc:8b:6a:f5:9e:5c:56:e1:0b:cc.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '[127.0.0.1]:9001' (ECDSA) to the list of known hosts.
root@127.0.0.1's password:
Last failed login: Thu Oct 819:29:28 CST 2020 from 213.154.70.102 on ssh:notty
There were 832 failed login attempts since the last successful login.
Last login: Thu Oct 818:41:462020 from 106.55.241.99
[root@new2 ~]#
上面可见后面新开窗口通过访问9001端口可以连接上new2服务器。
2.2 远程转发
命令:-R sshserverport:remotehost:remotehostport sshserver
说明:sshserverport 被转发机器开启的端口号
remotehost 最终连接机器的IP地址
remotehostport 被转发机器的端口号
sshserver 被转发机器的IP地址
#balance服务器上开启端口转发服务
# -R guangzhou-Server-Port:new2-Server-Ip:new2-Server-Port -fN guangzhou-Server-Ip
[root@Balance ~]# ssh -R 9100:106.55.171.53:22 -fN 106.55.241.99root@
106.55.241.99's password:[root@Balance ~]#
#guangzhou服务器上查看balance端口转发开启的9100端口
[root@guangzhou ~]# ss -ntlState Recv
-Q Send-Q Local Address:Port Peer Address:PortLISTEN
0128 *:27017 *:*LISTEN
0511 *:6379 *:*LISTEN
0128 *:9100 *:*LISTEN
0128 *:111 *:*LISTEN
0128 *:4369 *:*LISTEN
0128 *:22 *:*LISTEN
080 :::3306 :::*LISTEN
0511 :::6379 :::*LISTEN
0128 :::111 :::*LISTEN
0128 :::4369 :::*#连接9100端口,确认可以连接上new2服务器
~]# ssh -p 9100 root@127.0.0.1
[root@guangzhouThe authenticity of host
'[127.0.0.1]:9100 ([127.0.0.1]:9100)' can't be established.ECDSA key fingerprint is SHA256:huOuuKbfM9TN6+rpCMjB2Hk0HI4GSF1WCj7gIVyu48I.
ECDSA key fingerprint is MD5:0f:55:88:04:62:82:fc:8b:6a:f5:9e:5c:56:e1:0b:cc.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '[127.0.0.1]:9100' (ECDSA) to the list of known hosts.
root@127.0.0.1's password:
Last failed login: Fri Oct 911:28:02 CST 2020 from 61.7.235.211 on ssh:notty
There were 3 failed login attempts since the last successful login.
Last login: Fri Oct 911:26:162020 from 117.136.79.20
[root@new2 ~]#
远程转发就是做了一层请求代理服务,将指定客户端IP和客户端端口的请求转发到指定第三方服务器IP和端口。
2.3动态转发
命令:-D localhost:localport -fN sshserver
#guangzhou服务器上关掉所有ssh连接[root@guangzhou
~]# killallssh[root@guangzhou
~]# ssh -D 9200 -fN 124.156.143.168root@
124.156.143.168's password:[root@guangzhou ~]# curl --socks5 127.0.0.1:9200 http://106.55.171.53
hello~
以上通过设置guangzhou服务器9200端口转发已经可以正常请求new2服务器上的web服务
以上是 ssh端口转发 的全部内容, 来源链接: utcz.com/a/56815.html