013.OpenShiefc数据库加密-root权限-技能
一 Kubetcl namespace
1.1 namespace描述
- 命名资源,以避免基本的命名冲突;
- 将管理权限授予受信任的用户;
- 限制用户资源消耗的能力;
- 用户和用户组隔离。
1.2 project
- Object:pod、service、rc等;
- Policies:决定用户可以或不能对对象执行哪些操作的规则;
- Constraints:可以限制的每种对象的配额。
1.3 cluster管理
1.4 创建project
二 OpenShift角色
2.1 角色概述
2.2 查看本地policy
2.3 管理role绑定
命令 | 描述 |
oc adm policy who-can verb resource | 设置哪些用户可以对资源执行操作 |
oc adm policy add-role-to-user role username | 将指定角色绑定到指定用户 |
oc adm policy remove-role-from-user role username | 从指定用户中移除给定角色 |
oc adm policy remove-user username | 删除指定的用户及其所有角色 |
oc adm policy add-role-to-group role groupname | 将指定的角色绑定到指定的组 |
oc adm policy remove-role-fromgroup role groupname | 从指定组中移除给定角色 |
oc adm policy remove-group groupname | 删除指定的组及其所有角色 |
命令 | 描述 |
oc adm policy add-cluster-role-to-user role username | 将集群中所有项目的指定角色绑定到指定用户 |
oc adm policy remove-cluster-role-from-user role username | 为集群中的所有项目从指定用户中删除指定角色 |
oc adm policy add-cluster-role-togroup role groupname | 为集群中的所有项目将指定的角色绑定到指定的组 |
oc adm policy remove-cluster-role-from-group role groupname | 从集群中所有项目的指定组中移除给定角色 |
三 安全上下文约束(SCCS)
3.1 SCCS概述
1 [user@demo ~]$ oc get scc #列出可用的SCC2 [user@demo ~]$ oc describe scc scc_name #现实特定SCC详细信息
3 [user@demo ~]$ oc adm policy add-scc-to-user scc_name user_name
4 [user@demo ~]$ oc adm policy add-scc-to-group scc_name group_name #要授予用户或组特定的SCC
5 [user@demo ~]$ oc adm policy remove-scc-from-user scc_name user_name
6 [user@demo ~]$ oc adm policy remove-scc-from-group scc_name group_name #从特定的SCC中删除用户或组
四 服务账户
4.1 服务账户
4.2 Web管理user成员
4.3 Cli管理user成员
4.4 身份验证和授权
- user和group
- Authentication Tokens
4.5 身份验证类型
- Basic Authentication (Remote)
- Request Header Authentication
- Keystone Authentication
- LDAP Authentication
- GitHub Authentication
五 管理项目及账户
5.1 前置准备
5.2 本练习准备
5.3 创建htpasswd账户
1 [kiosk@foundation0 ~]$ ssh root@master2 [root@master ~]# htpasswd -b /etc/origin/master/htpasswd user1 redhat
3 [root@master ~]# htpasswd -b /etc/origin/master/htpasswd user2 redhat
4#添加基于htpasswd形式的user1和user2,密码都为redhat。
5.4 设置策略
1 [student@workstation ~]$ oc login -u admin -p redhat https://master.lab.example.com #使用管理员登录2 [student@workstation ~]$ oc adm policy remove-cluster-role-from-group \
3 self-provisioner system:authenticated:oauth
4#删除所有赋予普通创建项目的功能,该命令可参考本环境如下目录中的命令。
5 [student@workstation ~]$ cat /home/student/DO280/labs/secure-resources/configure-policy.sh
6#!/bin/bash
7 oc adm policy remove-cluster-role-from-group \
8 self-provisioner system:authenticated system:authenticated:oauth
5.5 验证策略
1 [student@workstation ~]$ oc login -u user1 -p redhat https://master.lab.example.com #使用普通用户user1登录2 [student@workstation ~]$ oc new-project test #测试创建project
3 Error from server (Forbidden): You may not request a new project via this API.
5.6 创建项目
1 [student@workstation ~]$ oc login -u admin -p redhat https://master.lab.example.com #使用集群管理员登录2 [student@workstation ~]$ oc new-project project-user1 #创建两个项目
3 [student@workstation ~]$ oc new-project project-user2
5.7 将项目与user关联
1#选择项目12 Now using project "project-user1" on server "https://master.lab.example.com:443".
3 [student@workstation ~]$ oc policy add-role-to-user admin user1 #将user1添加为项目1的管理员
4 role "admin" added: "user1"
5 [student@workstation ~]$ oc policy add-role-to-user edit user2 #将user2添加为项目1的开发员
6 role "edit" added: "user2"
7
8 [student@workstation ~]$ oc project project-user2 #选择项目2
9 Now using project "project-user2" on server "https://master.lab.example.com:443".
10 [student@workstation ~]$ oc policy add-role-to-user edit user2 #将user2添加为项目2的开发员
11 role "edit" added: "user2"
5.8 验证访问
1 [student@workstation ~]$ oc login -u user1 -p redhat https://master.lab.example.com #使用user1登录2 [student@workstation ~]$ oc project project-user1 #验证项目1的访问
3 Already on project "project-user1" on server "https://master.lab.example.com:443".
4 [student@workstation ~]$ oc project project-user2 #验证项目2的访问
5 error: You are not a member of project "project-user2".
6 You have one project on this server: project-user1
7
8 [student@workstation ~]$ oc login -u user2 -p redhat https://master.lab.example.com #使用user2登录
9 [student@workstation ~]$ oc project project-user1
10 Already on project "project-user1" on server "https://master.lab.example.com:443". #验证项目1的访问
11 [student@workstation ~]$ oc project project-user2
12 Now using project "project-user2" on server "https://master.lab.example.com:443". #验证项目2的访问
5.9 部署特权应用
1 [student@workstation ~]$ oc login -u user2 -p redhat https://master.lab.example.com2 [student@workstation ~]$ oc project project-user1
3 Now using project "project-user1" on server "https://master.lab.example.com:443".
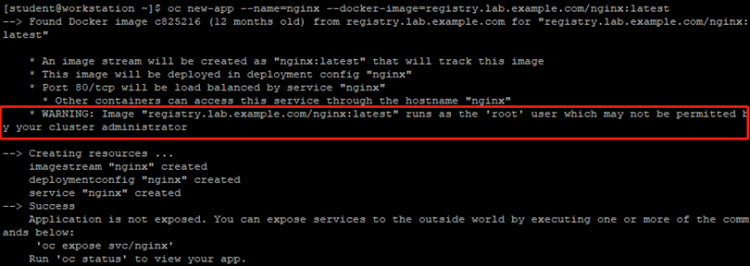
4 [student@workstation ~]$ oc new-app --name=nginx --docker-image=registry.lab.example.com/nginx:latest
5#使用在项目1上不具备admin权限的用户user2登录,并部署应用,会出现如下提示:
5.10 验证部署
1 [student@workstation ~]$ oc get pods5.11 故障排除
1 [student@workstation ~]$ oc login -u user1 -p redhat https://master.lab.example.com #使用项目1的admin账户登录2 [student@workstation ~]$ oc create serviceaccount useroot #创建服务账户
3 serviceaccount "useroot" created
4 [student@workstation ~]$ oc login -u admin -p redhat https://master.lab.example.com #使用集群管理员登录
5 [student@workstation ~]$ oc project project-user1 #选择项目1
6 Already on project "project-user1" on server "https://master.lab.example.com:443".
7 [student@workstation ~]$ oc adm policy add-scc-to-user anyuid -z useroot #设置SCC策略
8 scc "anyuid" added to: ["system:serviceaccount:project-user1:useroot"] #将服务帐户与anyuid安全上下文关联,此操作需要集群管理员用户。
9 [student@workstation ~]$ oc login -u user2 -p redhat https://master.lab.example.com #切换user2用户
10 [student@workstation ~]$ oc project project-user1
11 Already on project "project-user1" on server "https://master.lab.example.com:443".
12 [student@workstation ~]$ oc patch dc nginx --patch='{"spec":{"template":{"spec":{"serviceAccountName": "useroot"}}}}'
5.12 验证确认
1 [student@workstation ~]$ oc get pods2 NAME READY STATUS RESTARTS AGE
3 nginx-2-98k8f 1/1 Running 0 3m
4
5.13 暴露服务
1 [student@workstation ~]$ oc expose svc nginx2 route "nginx" exposed
3 [student@workstation ~]$ oc get svc
4 NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
5 nginx ClusterIP 172.30.118.63 <none> 80/TCP 13m
6 [student@workstation ~]$ oc get route
7 NAME HOST/PORT PATH SERVICES PORT TERMINATION WILDCARD
8 nginx nginx-project-user1.apps.lab.example.com nginx 80-tcp None
5.14 测试访问
1 [student@workstation ~]$ curl -s http://nginx-project-user1.apps.lab.example.com
5.15 策略删除演示
1 [student@workstation ~]$ oc login -u admin -p redhat2 [student@workstation ~]$ oc adm policy add-cluster-role-to-group self-provisioner system:authenticated system:authenticated:oauth
3 cluster role "self-provisioner" added: ["system:authenticated" "system:authenticated:oauth"]
4 [student@workstation ~]$ oc delete project project-user1
5 project "project-user1" deleted
6 [student@workstation ~]$ oc delete project project-user2
7 [root@master ~]# htpasswd -D /etc/origin/master/htpasswd user1
8 [root@master ~]# htpasswd -D /etc/origin/master/htpasswd user2
#为所有常规用户重新启用项目创建,即重置为初始状态。本环境中,相关操作命令可以从/home/student/DO280/labs/secure-resources文件夹中的restore-policy.sh脚本运行或复制。
六 管理加密信息
6.1 secret特性
- Secrets data可以独立于其定义引用。
- Secrets data Volume由临时文件存储支持。
- 可以在名称空间中共享Secrets data。
6.2 创建Secrets
1 [user@demo ~]$ oc create secret generic secret_name \2 --from-literal=key1=secret1 \
3 --from-literal=key2=secret2 #用secret data创建secret对象
4 [user@demo ~]$ oc secrets add --for=mount serviceaccount/serviceaccount-name \
5 secret/secret_name #更新pod的服务帐户,允许引用该secrets。
6.3 使用secret暴露Pod
1 env:2 - name: MYSQL_ROOT_PASSWORD
3 valueFrom:
4 secretKeyRef:
5 key: username
6name: demo-secret
6.4 web端管理secret
6.5 Secret使用场景
- password和user names
- 传输层安全性(TLS)和密钥对
七 ConfigMap对象
7.1 ConfigMap概述
7.2 CLI创建ConfigMap
1 [user@demo ~]$ oc create configmap special-config \2 --from-literal=serverAddress=172.20.30.40
3 [user@demo ~]$ oc get configmaps special-config -o yaml #查看configMap
4 apiVersion: v1
5data:
6 key1: serverAddress=172.20.30.40
7 kind: ConfigMap
8 metadata:
9 creationTimestamp: 2017-07-10T17:13:31Z
10name: special-config
11 ……
12 在配置映射的pod定义中填充环境变量APISERVER。
13 env:
14 - name: APISERVER
15 valueFrom:
16 configMapKeyRef:
17name: special-config
18 key: serverAddress
7.3 web管理ConfigMap
八 加密练习
8.1 前置准备
8.2 本练习准备
8.3 创建项目
1 [student@workstation ~]$ oc login -u developer -p redhat2 [student@workstation ~]$ cd /home/student/DO280/labs/secure-secrets/
3 [student@workstation secure-secrets]$ less mysql-ephemeral.yml #导入本环境MySQL模板
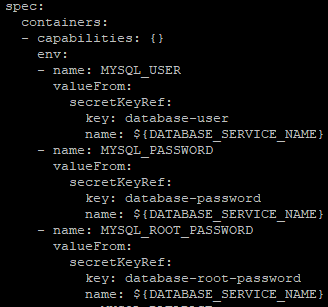
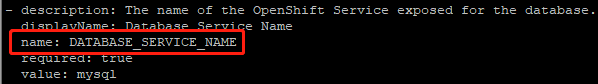
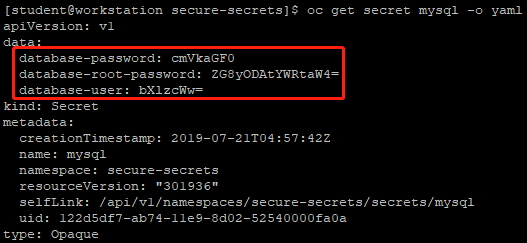
- 应用程序访问的数据库用户名由database-user定义。
- 数据库用户的密码由database-password定义。
- 数据库管理员密码由database-root-password定义
8.4 创建新secret
1 [student@workstation secure-secrets]$ oc create secret generic mysql \2 --from-literal='database-user'='mysql' \
3 --from-literal='database-password'='redhat' \
4 --from-literal='database-root-password'='do280-admin'
5 [student@workstation secure-secrets]$ oc get secret mysql -o yaml #确认secret
8.5 创建应用
1 [student@workstation secure-secrets]$ oc new-app --file=mysql-ephemeral.yml2 [student@workstation secure-secrets]$ oc get pods #确认应用
3 NAME READY STATUS RESTARTS AGE
4 mysql-1-j4fnz 1/1 Running 0 1m
8.6 端口转发
1 [student@workstation secure-secrets]$ cd2 [student@workstation ~]$ oc port-forward mysql-1-j4fnz 3306:3306
8.7 确认验证
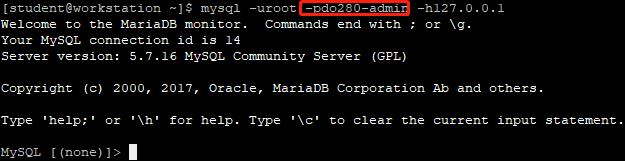
1 [student@workstation ~]$ mysql -uroot -pdo280-admin -h127.0.0.1 #新开终端测试MySQL
九 管理security policy
9.1 OCP authorization授权
默认角色 | 描述 |
cluster-admin | 此角色中的所有用户都可以管理OpenShift集群。 |
cluster-status | 此角色中的所有用户都提供对集群信息的只读访问。 |
默认角色 | 描述 |
edit | 角色中的用户可以从项目中创建、更改和删除公共应用程序资源,比如service和dc。 但是不能对限制范围和配额等管理资源采取行动,也不能管理对项目的访问权限。 |
basic-user | 角色中的用户具有对项目的读访问权。 |
self-provisioner | 角色中的用户可以创建新项目。这是一个集群角色,而不是项目角色。 |
admin | 角色中的用户可以管理项目中的所有资源,包括授予对项目的其他用户的访问权 |
9.2 相关命令
1 向集群用户添加角色2 $ oc adm policy add-cluster-role-to-user cluster-role username
3 示例:将普通用户更改为集群管理员。
4 $ oc adm policy add-cluster-role-to-user cluster-role username
5 从用户中删除集群角色
6 $ oc adm policy remove-cluster-role-from-user cluster-role username
7 示例:将集群管理员更改为普通用户。
8 $ oc adm policy remove-cluster-role-from-user cluster-admin username
9 将指定的用户绑定到项目中的角色
10 $ oc adm policy add-role-to-user role-name username -n project
11 示例:在WordPress项目中dev用户绑定basic-user角色。
12 $ oc adm policy add-role-to-user basic-user dev -n wordpress
9.3 权限及规则
1 $ oc adm policy who-can delete user
9.4 user类型
9.5 安全上下文约束(SCCS)
- 运行特权容器
- 请求容器的额外功能
- 使用主机目录作为卷
- 更改容器的SELinux上下文
- 更改用户ID
- anyuid
- hostaccess
- hostmount-anyuid
- nonroot
- privileged
- restricted(默认)
9.6 OpenShift与SELinux
9.7 特权容器
十 资源访问控制综合实验
10.1 前置准备
10.2 本练习准备
1 [student@workstation ~]$ lab secure-review setup10.3 创建用户
1 [root@master ~]# htpasswd /etc/origin/master/htpasswd user-review2 New password: 【redhat】
3 Re-type new password: 【redhat】
10.4 修改策略
1 [student@workstation ~]$ oc login -u admin -p redhat2 [student@workstation ~]$ oc adm policy remove-cluster-role-from-group \
3 self-provisioner system:authenticated system:authenticated:oauth
4 禁用所有常规用户的项目创建功能
10.5 确认验证
1 [student@workstation ~]$ oc login -u user-review -p redhat2 [student@workstation ~]$ oc new-project test #普通用户无法创建项目
3 Error from server (Forbidden): You may not request a new project via this API.
10.6 创建项目
1 [student@workstation ~]$ oc login -u admin -p redhat2 [student@workstation ~]$ oc new-project secure-review #使用管理员创建项目
10.7 授权用户
1 [student@workstation ~]$ oc project secure-review2 Already on project "secure-review" on server "https://master.lab.example.com:443".
3 [student@workstation ~]$ oc policy add-role-to-user edit user-review #将edit的role和user-review进行关联
10.8 测试访问
1 [student@workstation ~]$ oc login -u user-review -p redhat2 [student@workstation ~]$ oc project secure-review #测试访问
3 Already on project "secure-review" on server "https://master.lab.example.com:443".
10.9 检查模板
1 [student@workstation ~]$ cd /home/student/DO280/labs/secure-review/2 [student@workstation secure-review]$ less mysql-ephemeral.yml
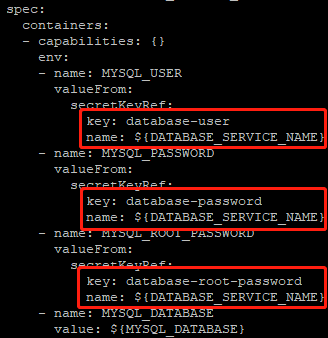
- 应用程序访问的数据库用户名由database-user定义。
- 数据库用户的密码由database-password定义。
- 数据库管理员密码由database-root-password定义
10.10 创建secret
1 [student@workstation secure-review]$ oc create secret generic mysql \2 --from-literal='database-user'='mysql' \
3 --from-literal='database-password'='redhat' \
4 --from-literal='database-root-password'='do280-admin'
5 [student@workstation secure-review]$ oc get secret mysql -o yaml #确认验证secret
10.11 部署应用
1 [student@workstation secure-review]$ oc new-app --file=mysql-ephemeral.yml2 [student@workstation secure-review]$ oc get pods
3 NAME READY STATUS RESTARTS AGE
4 mysql-1-2lr7t 1/1 Running 0 31s
10.12 转发端口
1 [student@workstation ~]$ oc port-forward mysql-1-2lr7t 3306:330610.13 测试访问
1 [student@workstation ~]$ mysql -umysql -predhat -h127.0.0.110.14 部署phpmyadmin应用
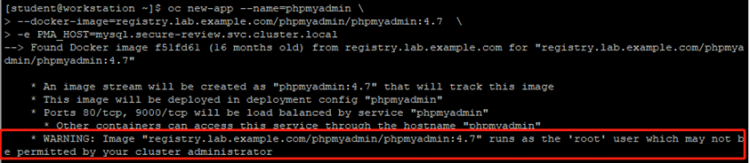
1 [student@workstation ~]$ oc new-app --name=phpmyadmin \2 --docker-image=registry.lab.example.com/phpmyadmin/phpmyadmin:4.7 \
3 -e PMA_HOST=mysql.secure-review.svc.cluster.local
10.15 查看pod
1 [student@workstation ~]$ oc get pods2 NAME READY STATUS RESTARTS AGE
3 mysql-1-2lr7t 1/1 Running 0 8m
4 phpmyadmin-1-v7tl7 0/1 Error 2 1m
5 因为没有root权限,因此部署失败,需要提权。
10.16 授予权限
1 [student@workstation ~]$ oc login -u admin -p redhat #使用管理员登录2 [student@workstation ~]$ oc create serviceaccount phpmyadmin-account #首先创建服务账户
3 [student@workstation ~]$ oc adm policy add-scc-to-user anyuid -z phpmyadmin-account
4 scc "anyuid" added to: ["system:serviceaccount:secure-review:phpmyadmin-account"] #将服务帐户与anyuid安全上下文关联
10.17 更新应用
1 [student@workstation ~]$ oc patch dc phpmyadmin --patch='{"spec":{"template":{"spec":{"serviceAccountName": "phpmyadmin-account"}}}}'
10.18 确认验证
1 [student@workstation ~]$ oc login -u user-review -p redhat2 [student@workstation ~]$ oc get pods #确认pod是否正常
3 NAME READY STATUS RESTARTS AGE
4 mysql-1-2lr7t 1/1 Running 0 13m
5 phpmyadmin-2-bdjvq 1/1 Running 0 1m
10.19 暴露服务
1 [student@workstation ~]$ oc expose svc phpmyadmin --hostname=phpmyadmin.apps.lab.example.com10.20 访问测试
1 [student@workstation ~]$ curl -s http://phpmyadmin.apps.lab.example.com10.21 确认及删除
1 [student@workstation ~]$ lab secure-review grade #环境脚本判断2 [student@workstation ~]$ oc login -u admin -p redhat
3 [student@workstation ~]$ oc adm policy add-cluster-role-to-group \
4 self-provisioner system:authenticated system:authenticated:oauth
5 [student@workstation ~]$ oc delete project secure-review
6 [student@workstation ~]$ ssh root@master htpasswd -D \
7 /etc/origin/master/htpasswd user-review #删除用户
8 [student@workstation ~]$ oc delete useruser-review #删除项目
以上是 013.OpenShiefc数据库加密-root权限-技能 的全部内容, 来源链接: utcz.com/a/61030.html